The MacValley blog
![]()
Welcome to the MacValley blog, your first stop for all the latest MacValley news and views.
|
The MacValley blog Editor: Tom Briant
|
Labels used in posts
|
To search the blog posts please use the box below
Sunday, August 31, 2014
An essential OS X Mavericks problem-solving guide | Computerworld
This article has lots of tips for you if your Mavericks installation doesn’t work.
It’s by Jonny Evans, Computerworld’s resident Apple geek
Tom Briant
Editor, MacValley Blog
An essential OS X Mavericks problem-solving guide | Computerworld: ""
(Via.)
Senior Correspondent Arnold Woodworth's Weekly Update
Apple loses bid to block Samsung phones
http://www.iol.co.za/scitech/technology/news/apple-loses-bid-to-block-samsung-phones-1.1742230#.U_7g8qXvbnc
11 Rare Apps That Were Yanked from Apple’s App Store
https://www.yahoo.com/tech/11-rare-apps-that-were-yanked-from-apples-app-store-96091989324.html
Why Tech Sites have a Horrible Pro-Apple Bias
while accusations of “pro-Apple bias” occur so often that they’re practically meaningless, that doesn’t mean Apple doesn’t have a brilliant strategy for monitoring and manipulating media coverage about the company that is lightyears beyond what Amazon, Microsoft or even Google do.
“Their strategy is to say nothing,” says one of Gurman’s sources. “It keeps everyone guessing what Apple is up to, generates free publicity, and keeps them out of the trouble everyone gets into. Once you start answering questions, you get your foot in your mouth.”
http://www.techly.com.au/2014/08/31/tech-sites-horrible-pro-apple-bias/
Apple tells developers they may not sell personal health data to advertisers
Apple announced in June this year that a new standard app called "Health" will collect data on blood pressure, heart rate, and stats on diet and exercise.
developers "must not sell an end-user's health information collected through the HealthKit APIs to advertising platforms, data brokers or information resellers". Although, the rules add that they could share their data with "third parties for medical research purposes" as long as they get users' consent.
http://www.theguardian.com/technology/2014/aug/29/apple-health-data-privacy-developers-advertisers
Apple co-founder Woz calls wearables 'a hard sell,' wants bigger screen
Steve "Woz" Wozniak thinks Apple is poised to take wearables to the next level. But unlike smartphones and tablets, wearables may prove a tougher sell to consumers -- including him.
http://www.cnet.com/news/apple-co-founder-woz-calls-wearables-a-hard-sell-wants-bigger-screen/
After Exposing Sexism In The Video Game Industry, This Woman Received Rape Threats On Twitter
http://www.businessinsider.com/game-industry-critic-faces-rape-threats-2014-8
Here's Why This CEO Finds All Her Employees Through LinkedIn
http://www.businessinsider.com/ceo-finds-all-employees-through-linkedin-2014-8
Twitter Analytics Is A Gold Mine Of Information About Your Tweets
If you’re looking for an ego boost, look no further: There’s an easy way to see just how many people witness your Twitter brilliance each day.
http://www.bustle.com/articles/37820-twitter-analytics-is-a-gold-mine-of-information-about-your-tweets
Twitter this week opened up its analytics tool to everyone after testing it with a small group of userssince June.
http://www.pcmag.com/article2/0,2817,2465499,00.asp
Twitter Now Shows You Exactly How Many People See Your Tweets — And It's Mesmerizing
Sometimes, tweeting is like gazing into the abyss, as Nietzsche may have said. With Twitter Analytics, you can now find out whether the abyss is retweeting you.
it's about finding out the real reasons that your followers find you interesting, and how that compares with your perception of yourself.
And that is why Twitter Analytics is so compelling: It's like seeing yourself in a brutal social media vanity mirror. Sometimes hideous, sometimes not so bad ... but you cannot look away.
http://www.businessinsider.com/twitter-analytics-dashboard-launched-2014-8
Celebrities and other big wigs on Twitter have long had access to their accounts' metrics, able to see user engagement and other information on followers and account activity. That feature has been extended to include (almost) every user, regardless of whether they're verified.
Twitter Analytics can now be accessed by anyone who has had a Twitter account for longer than two weeks.
http://www.slashgear.com/twitter-rolls-out-activity-dashboard-for-the-little-people-28343134/
Here's Why Amazon Just Paid Nearly $1 Billion For A Site Where You Watch People Play Video Games
Amazon said Monday it's buying video-streaming site Twitch for $970 million in cash, noting that in just three years it's built a platform that attracts millions of visitors every month.
People love watching other people play games and commenting on them.
http://www.businessinsider.com/heres-why-amazon-paid-almost-1-billion-for-twitch-2014-8
Amazon Buys Twitch? Really?
It's worth a billion dollars to watch someone else play a video game?
I will note that it was worth billions to sell pet supplies over the Internet too.
In 1999.
http://www.market-ticker.org/akcs-www?post=229343
Twitch.tv Brought Down By Lizard Squad DDoS Attacks
The DDoS attacks came the day after it was announced that Amazon had purchased Twitch for $970 million
http://hothardware.com/News/Twitchtv-Brought-Down-By-Lizard-Squad-Attacks/#!bLYDCp
Study finds human are happy to be managed by robots
HUMAN workers prefer to take orders from robots than their colleagues, researchers have found.
http://www.iol.co.za/business/international/study-finds-human-are-happy-to-be-managed-by-robots-1.1741530#.U_2adaXvbnc
New research from MIT shows that robots are not only more efficient than humans at controlling human workers, but that the workers prefer receiving orders from robots than from another person in a higher-up position.
Instead of coming up with a plan by hand, it's about developing tools to help create plans automatically
http://www.techtimes.com/articles/14097/20140826/should-robots-take-control-mit-scientists-say-yes.htm
Massive, open, online courses (MOOC) were once hailed as the next big disruption to traditional higher education, opening the door to a college education to anyone, anywhere in the world. But the low percentage of students who complete such classes on their own, and the fact that most people who sign up for MOOCs already have a college degree, have educators rethinking how the new format for college coursework can best be put to use.
http://www.pbs.org/newshour/rundown/still-little-consensus-role-massive-online-courses-higher-education/
ALERT: Malware 'Meteroids'
This author found a particularly-pernicious bit of spyware and had some fun getting rid of it.
It affects Windows machines. The author doesn't say if it affects Macs.
the service survives the uninstall, and worse, it is capable of and does "hook" a browser session even without an extension loaded!
most anti-virus systems will not pick it up.
http://www.market-ticker.org/akcs-www?post=229340
How To Never, EVER Worry About Your Passwords Getting Hacked Or Stolen
It's time to get smarter about your passwords by using a password manager app. Such an app makes it ridiculously easy to create unguessable passwords and change them whenever the need strikes.
AW comment: This borders on being a long advertisement for a product called "Last Pass". I've never heard of this product before.
AW comment: That said, password security is very important, and a good password management app can help.
AW comment: Another product for the Mac called "1Password" is worth a look.
http://www.businessinsider.com/how-to-use-password-manager-lastpass-2014-8
Tuesday, August 26, 2014
Newegg rolls out same-day delivery in Los Angeles | PCWorld
If you’re too lazy to put on pants and shoes and have enough cash to afford same day delivery, Newegg is starting a same day delivery option for those of us living within 50 miles of the City of Industry. Get that motherboard today!
A side note: Try to stagger your deliveries, so that they don’t clog the street.
Newegg rolls out same-day delivery in Los Angeles | PCWorld: ""
(Via.)
Rumored 12.9-inch iPad could be better for business productivity | PCWorld
PC World’s Tony Bradley speculates that a 12.9 “iPad Pro” would fail unless they follow his commandments.
Who’s up for printing out this article and serving it to Tony in 2015 on toast with suitable condiments? Stream his doleful countenance chowing down on this sandwich of shame? Excellent!
Tom Briant
Editor, MacValley Blog
Rumored 12.9-inch iPad could be better for business productivity | PCWorld: ""
(Via.)
The LA Unified School District, iPads, and other news
In a story in Appleinsider quoting the Los Angeles Times, the LAUSD has halted the program for equipping students with iPads. Accusations of conflict of interest between top LAUSD employees have emerged. The school district will try out various Windows laptops and Chromebooks, too.
The editor did not go to school in the LAUSD. He is quite aware that many members of MacValley either currently work for or worked in LAUSD. He would welcome their comments.
The editor will repeat a comment he made earlier about the LA School Board and us, the voters. We can’t ignore these elections or just vote for the candidate because the Teacher’s Union endorses them or opposes them. If the LA School Board is going to spend billions of our tax dollars on technology, it’s up to the voters to ensure they send candidates to office who won’t be baffled by the flashiest Keynote or Powerpoint presentation.
While on the topic of iPads, Bloomberg News reports that Apple will bring out a 12.9” iPad next year. Features and price are unknown at this time.
Tom Briant
Editor, MacValley Voice
Sunday, August 24, 2014
How I got Synergy to work with Ubuntu Linux without any terminal work and remaining relatively calm
In a prior article I wrote about using the open-source program Synergy to link up my Mac Mini as the server and my Windows 7 machine as the client. The server’s keyboard and pointing device controlled both computers. I could also share the clipboard between the two machines and sent text & pictures between them.
Now I will teach you how to do this with Ubuntu Linux. By Ubuntu Linux, I include all the derviative distributions of Ubuntu cooked up by various people to meet their particular needs or fancies. In this case, I will show you how to use Synergy with the popular distro LinuxMint 17.
First, you need to download the necessary file(s) to make Synergy run. Go to their Web site synergy-project.org They’ve had numerous Web sites over the years and this is their current one.
As I wrote in the earlier article, make life easier on yourself by spending $2.00 to become a Premium member. You get access to their help and (and!) get ad-free downloads. That, to me, was worth the $2.00.
For their Ubuntu and Debian versions, they offer Synergy as both a 32-bit and a 64-bit download. Pick the one that fits your machine. I have a 64-bit machine so I chose 64-bit Synergy.
So you chose the appropriate file to download. You will download a .deb file, which is short for debian. Debian is the root source of Ubuntu and LinuxMint. Its installation files have the .deb extension. Think of them as the equivalent of OS X .pkg files. You want to save it for now.
Here is your Synergy .deb file in the Downloads folder. It’s just like the .dmg files you download to your Mac in many respects. But not all.
Click on the .deb file and it starts up the package installer program.
In many cases, you will get a warning like this if you try to install a .deb file that you downloaded on your own. Ubuntu comes with its own App Store called the Software Manager. It includes a wide-range of apps which you can install and uninstall from the Software Center. I’m convinced that Apple saw this and stole the idea for the iTunes App Store.
You may find that only the older version of the program is available through the Software Manager. In this case, you will install the latest version of Synergy, 1.5.1, instead of the version available through the Software Manager of 1.4.
So just click on the Close button and proceed. Click on Install Package.
Synergy installs without problems. Where do you find it in LinuxMint? You would go to the Menu in the lower left-hand corner of your screen. You would go to the Accessories subsection and scroll down to Synergy. If you’ve used Windows during the past 10 years, this will be totally familiar to you.
Configuring the Linux Synergy Server and the Mac Client
Now click on the Synergy icon in Accessories. You will see this screen allowing you to configure Synergy as either the server, whose keyboard and pointing device control all the computers; or as the client, one of the computer controlled by the server.
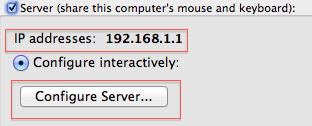
We’ll start with the server configuration. Click on the check box for Server (share this computer’s mouse and keyboard)
Note the server’s IP address, which you will need when configuring the client.
Now click on the button Configure Server….
You will see the following screen:
In the center of the 5 x 3 grid, you see an icon of a monitor with the server’s name on it.
At the top left-hand corner, you see a trash can. Drag a screen to the trashcan to delete it.
At the top right-hand corner, you see an icon of a monitor screen. Drag new screens to the grid or move existing ones around.
So drag a new screen onto the grid:
The new screen lacks a name, especially the name of the client computer. Double-click on it to rename it.
In this illustration, I changed the name from “Unnamed” to “thomass-mini”, the screen name of my Mac Mini. That provides sufficient information to Synergy to identify the client computer.
Don’t worry about the rest of the screen’s options. For now, you only needed the client’s screen name.
In the screenshot, you see that the server and client computers have their names. Click on OK and proceed.
This is the screenshot from the Windows version of Synergy 1.5.1. It’s the same for the Mac version.
For the client computer(s), click on the box Client (use another computer’s keyboard and mouse)
The client’s screen name will be filled in by Synergy. You only need to add the server’s IP address. I said IP address and not the server’s screen name! Look back at the server’s configuration screen and you’ll see the IP address just under the check box for Server. You’d want the first one listed.
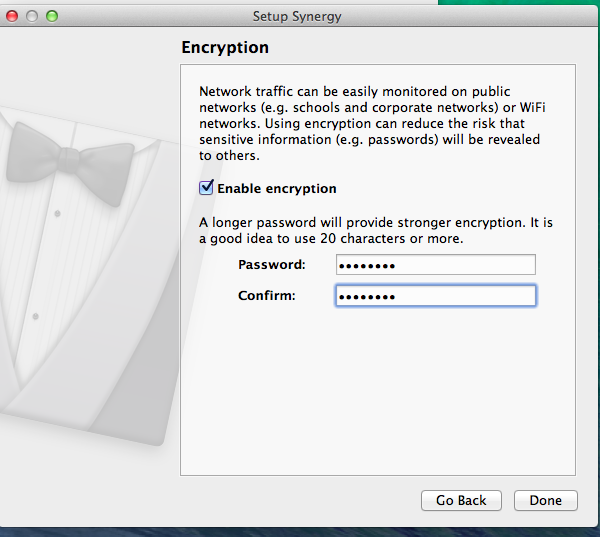
Now for the final steps. You want to make sure you use an encrypted connection. For Linux and Windows, go under the Edit menu to its sole item, Settings.
Click on Settings and you see this window:
If you want to change the password, just backspace over the old one and type in the new one. Then click on OK.
For the Mac’s Synergy password, don’t go to the Edit menu in the Menu Bar. You want to go to the Preferences item under the Synergy item on the Menu Bar.
And under Preferences, you ‘ll find the Encryption text box.
Now click on OK in the open dialogue boxes and click Apply in the Configure Server and Client screens on the respective computers.
Troubleshooting
If Synergy doesn’t work, check the following:
1) Do you have multiple instances of Synergy running on the Linux machine? If so, shut them all down. Now go back to Accessories and start up Synergy.
2) Still isn’t running? Click on the Configure Server… button and look at the configuration grid. Do you see the Server and the named client.
If you don’t see a client, drag a screen down to the appropriate grid cell. Now name it after the client computer. Refer to the client’s configuration screen for the correct spelling. Word Case counts in this case.
If you see a client with the name Unnamed. Click on it and rename it to the client’s name. Make sure to spell the client’s name exactly as it’s displayed on the client’s configuration screen. Word Case counts in this case.
Did you enter the right IP address from the server when setting up the client? Check that.
3) If you’re getting a “Protocol Error” you need to check the passwords. You need to set up the same password for both computers.
4) Check the Ethernet connection. Try to access, say, CNN.com from Safari. If you can, your Ethernet connection is good. If not, check a wired connection to make sure the cable fits snugly into the RJ-45 jack on the computer and on the router.
5) If it’s a wireless connection, make sure you have access to the router. Did you enter the password? And are you on the same wireless network as the server?
Conclusion
Synergy enables you to share keyboard and pointing device (I’m using a trackball with my Linux server) between several different computers. In the past, it has been tricky at best to impossible for even Macworld to set up. With version 1.5.1, it has finally improved to the point where I, a blogger writing in his shorts, can do it.
If you’re going to use it on a wireless network, make sure to set up encryption. I recommend encryption in all cases.
Finally, it’s a thrill to see my cursor move from my Linux machine over to the two screen of my Mac Mini.
If you like it, contribute some money to their efforts.
Tom Briant
Editor, MacValley Blog
Saturday, August 23, 2014
Senior Correspondent Arnold Woodworth's Weekly Roundup
Apple on Friday announced a free replacement program for iPhone 5 batteries after discovering certain units sold during a five-month period after the product's launch in 2012 contain faulty components.
http://appleinsider.com/articles/14/08/22/apple-activates-iphone-5-battery-replacement-program
Apple updates iMovie for Mac, iWork suite for OS X and iOS with minor bug fixes
http://appleinsider.com/articles/14/08/21/apple-updates-iwork-suite-for-os-x-and-ios-with-minor-bug-fixes-stability-improvements
Why Everything Gets Better With Apple, Worse for Others
http://www.macobserver.com/tmo/article/why-everything-gets-better-for-apple-worse-for-others
How Apple took over the only segment of the PC market that still matters
http://www.zdnet.com/how-apple-took-over-the-only-segment-of-the-pc-market-that-still-matters-7000032801/
A new theory on why Apple device owners spend far more than Android users
Apple users place more value on their time, says Nikki Baird. They don't spend time messing around with geeky computer stuff, but Android users do.
http://www.internetretailer.com/2014/08/19/new-theory-why-apple-trumps-android-mobile-commerce
Here's How Apple's Products Have Evolved Over The Years
http://www.businessinsider.com/heres-how-apples-products-have-evolved-over-the-years-2014-8
The Best Typeface Apple Ever Had
The font named "Chicago", which came with the very first Macintosh.
http://gizmodo.com/the-best-typeface-apple-ever-had-1625325454
Die in Delaware and your heirs get your online accounts
When people die, it often means the end of their online identity as well.
But this month, Delaware became the first state to pass a broad law giving heirs the right to access online accounts and digital assets of someone who has passed away.
http://money.cnn.com/2014/08/20/pf/death-online-accounts/
Facebook Is Testing A 'Satire' Tag Since Users Think The Onion Articles Are True
http://www.forbes.com/sites/amitchowdhry/2014/08/18/facebook-is-testing-a-satire-tag-since-users-think-the-onion-articles-are-true/
This Is What Tech Was Like In 1994
http://www.businessinsider.com/tech-in-1994-the-year-the-web-was-born-2014-8
I've come to the conclusion that the technology industry as we know it will soon cease to exist. We are currently in the early stages of a global transformation that's so enormous and pervasive it's actually hard to see.
Simply put, all the old boundaries have evaporated. All the characterizations and labels we've used for years no longer apply.
the common wisdom about management, markets and investing are being rendered obsolete in real time.
entrepreneurs, executives and investors are crossing boundaries in ways we've never seen before.
http://www.foxbusiness.com/technology/2014/08/21/tech-industry-is-vanishing-before-our-eyes/
The New Editors of the Internet
Twitter and YouTube are among a tiny group of giant companies with greater and greater power-and less and less accountability-over what we read, hear, and watch online.
Who gave them this power? We did.
We need, as web inventor Tim Berners-Lee has urged, to re-decentralize the Internet, and restore its promise as a medium where the action takes place at the edges of networks-where we wouldn't need permission to communicate and innovate.
The first way we users of Internet services can re-decentralize is to create-and make use of-our own home base online. In practical terms, this means getting your own domain name and creating, at a minimum, a blog where you establish your own identity. The page you think is yours at LinkedIn, Tumblr, Instagram (Facebook), or any of the other centralized services is emphatically not truly your own; it's theirs.
You can also keep an eye on a small but growing movement among some software developers who are working quietly to give us some vital tools. I'm a big fan of what the "Indie Web" people are doing.
Crucially, you can recognize the even greater emerging threat to your freedom of expression in the dominance of telecom companies that want absolute control over the Internet by killing what's known as network neutrality.
This is a pivotal time for our communications ecosystem. As we cede control to governments and corporations-and as they take it away from us-we are risking a most fundamental liberty, the ability to freely speak and assemble. Let's not trade our freedom for convenience.
http://www.theatlantic.com/technology/archive/2014/08/the-new-editors-of-the-internet/378983/
Re-Using the Same Password on Multiple Web Sites is the Most Dangerous Thing You Can Do Online
If a hacker obtains your password, the first thing he or she does is check whether or not that password works for other websites
http://www.businessinsider.com/biggest-password-mistake-2014-8
Now that the age of digital patient information is upon us, along with it comes theft of data.
http://blogs.marketwatch.com/health-exchange/2014/08/21/theft-of-patient-data-shows-up-as-health-digital-movement-spreads/
About 4.5 Million face risk of ID theft after hospital network hacked
About 4.5 million people in 28 states face the risk of identity theft due to a massive data breach at Community Health Systems (CHS) a Franklin, Tenn., based health network.
CHS, which operates over 200 hospitals, disclosed in a regulatory filing Monday that hackers, apparently based out of China, accessed systems containing the data sometime in April and June.
The hackers successfully bypassed the company's security controls and siphoned out names, Social Security Numbers, addresses, birthdates and phone numbers of people who received or were referred for services by CHS affiliated doctors over the past five years.
http://www.computerworld.com/s/article/9250464/About_4.5M_face_risk_of_ID_theft_after_hospital_network_hacked
Why would Chinese hackers want US hospital patient data?
Medical records data can be a valuable asset, especially in a country where many have no health insurance
people without health insurance can potentially get treatment by using medical data of one of the hacking victims.
Already this year, around 150 incidents of lost or stolen personal data -- either due to hacking or ineptitude -- have been reported by medical establishments to the U.S. Department of Health and Human Services.
http://www.computerworld.com/s/article/9250477/Why_would_Chinese_hackers_want_US_hospital_patient_data_
What to do if your Social Security number was stolen
http://www.marketwatch.com/story/what-to-do-if-your-social-security-number-was-stolen-2014-08-20
Little-known ways hackers take over your phone, data and money
http://www.marketwatch.com/story/little-known-ways-hackers-take-over-your-phone-data-and-money-2014-08-22
Dukto-cross platform file transfer between Windows, OS X, and Linux
In my previous article about Synergy, I mentioned the open-source application Dukto for transferring files and folders between various platforms. This is how to set it up and get it working between Windows and OS X. Linux I’ll go into in a subsequent article.
First go to Dr. Colombo’s personal Web site for the installers for Windows and OS X. You’ll have to scroll down the page to reach them, but he clearly marked them.
This is what you see when you open the .DMG file for Dukto. He’s got a sense of humor.
So you’ve installed the Dukto app. Click on it.
I got this message from OS X:
So I allow network connections. Now Dukto comes up.
And no, that’s NOT my picture. That’s some idiot in Florida caught doing something hilariously disgusting. Any readers in Florida care to comment?
So you install Dukto in Windows by clicking on the .EXE, following the steps. You end up with Dukto in your Start Menu (this is Windows 7)
You double-click on it and get this on your desktop:
How to send files from one machine to the other:
You double-click on Captain Obvious here on the Windows machine.
The next window asks you “What do you want to do?” Well, I want to send some files
Click on “Send some files” and you get the Windows File Dialog box.
Select the files you want to send to the other machine and click on the Open button. Dukto sends you the files to your OS X machine to your Desktop. There’s the Router manual that was on the Windows machine now on the OS X machine.
That’s a brief explanation of how Dukto works. If you click on the gear that you see at the bottom of the screenshot, you can change where the files go. You won’t have to mess up your desktop.
Tom Briant
Editor, MacValley Blog
How I got the latest version of Synergy to work reliably without tearing out my hair
You have two or more computers, each with their own monitor and set of tasks to perform. You have them arranged on an old piece of recycled kid’s desk furniture. You resent having to shove one keyboard and pointing device out of the way to get to the next one when you change your focus from computer to computer. How do you solve this problem?
You can use a hardware K(eyboard) V(ideo) and M(ouse) switch to move between them, but you have to set up the cabling necessary for the switch to work. Not to mention the cost of the switch. After two machines, the cost becomes prohibitive unless you can write it off on your taxes.
I've mentioned the J5-400 Wormhole USB cable, which provides a plug and play solution between Windows to Macs, Macs to Macs, and Windows to Windows. If you go out in the field and need to set up a quick connection between your work machine and the client, then I'd wholeheartedly recommend it. It lets you share a keyboard and pointing device, share a clipboard, and even drag files from one screen to another.
Now let's take the situation faced by many. They use their computers for work and non-work activities. They have a mix of computers. Some have two Macs, some have a Windows and a Mac, and some even have a Linux machine. They want to know how to use software and their existing wired/wireless network so that they can use just one keyboard and pointing device to control their digital devices.
That's where Synergy comes in. I'm using the latest version 1.5.1 and I got it to work after some fiddling with it.
The two main things I did to set up Synergy were to invest in a Premium account with Synergy for $2 and to use encryption. These two steps made the process work smoothly.
Here's how I did it.
Step 1: I logged onto the synergy-project.org, which is their Web site now. They've had several different Web sites over the years.
When I started to download, they put up a “begware” notice. Please help us! They asked for as little as 99 cents. I decided to pay $2 for a premium account, which gives me access to their help. Even better, I got access to ad-free downloads. So the $2 was well-spent. You'll need Paypal for this.
If you don’t know whether your Windows computer runs 32-bit Windows or 64-windows, look at the computer’s manual. I wrote this using a 64-bit version of Windows 7. Go to your Window’s Control Panel and click on System for whether you run a 32-bit or 64-bit system.
So you've downloaded Synergy in its Windows and OS X versions. You'll want the latest version, 1.5.1.
For the Mac, You double-click on the downloaded .dmg file to mount it. You copy the application to your applications folder and double-click on it.
Step 2: If you run into a notice that this is not Apple approved software and won't run when you double-click on it, do the following.
Control-click with your touchpad or right-click with your two-button mouse on the Synergy icon. You'll get a drop-down menu. It's first item will be “Open...”
Click on “Open...” You'll get a notice that if you want to run this software despite Apple's misgivings, click on OK. You click on OK and Synergy starts up. You only need to do this once.
Step #3: What about encryption? If you set up the OS X version as your server, the OS X version asks for encryption. They highly recommend it. In fact, for me this proved crucial in getting Synergy to work. So make up a password.
Can't think of one? Take the name of your favorite TV show and stick a special character between the words. You can go back and change it later to something more inscrutable.
(If you have to go back and change a password in the Mac version, go under Preferences. If you don’t see the Mac version, click on the circular icon in the menu bar and click on Show)
Now you've reached the actual configuration screen. You can configure the Mac as either the server, whose keyboard and pointing device control the other computers. Their keyboard and pointing devices still work, but only for them. Only the server has free range over all the computers; or as the client, taking direction from the server's keyboard and pointing device.
I’ll assume you want to set up your Mac as the server, so I’ll start with setting up the server first.
Looking at the screenshot, you can interactively configure your computers or use an existing configuration file. As this is your first time, you'll need to interactively configure.
I'll get to the client side after this.
Click on the “Configure Server” box. The screen changes and you see a 5x3 grid with your server in the center.
Read the simple instructions at the bottom. You drag a new screen from the icon well onto the grid. Move it to fit your needs.
When you move a new screen onto the grid, its name will be “Unnamed”. You want to name it to the name of the computer you want to control. You want to type the exact name of the other computer in the Screen Name box at the top of the window. Synergy is case-sensitive in this regard.
To rename the new screen to the client's name, just double-click on it. Type in the exact spelling and case of the client's name into the Screen Name box. Then click OK.
What about the rest of the Screen Name box? You can ignore it for now. Just type in the name of the client computer correctly.
Where will you get the client machine's exact screen name? You get it when you when you set up the client portion of Synergy. As you see from the screenshot below, you see the exact spelling of the client's name just below the checkbox for Client (use another computer's keyboard and mouse)
Now the client asks for the IP address of the server computer. You get that from the server portion of the setup screen on the Mac side. It's the top item on the screen.
Now for the encryption part of the Windows client. You want to go to the Menu Bar in the main Synergy program window.
Go to the Edit menu, which is next to the file menu. You will find one item, Settings.
Click on Settings and you'll see a check box for encryption and a box to enter your password.
Don’t worry if the password in the screenshot looks longer than what you created. Synergy fills in the spaces to foot hackers. So just click the Enable check box, type in your password, and click the OK button at the bottom. You should be on your way!
If you get a “Protocol Error” that means the password is missing or misspelled on either the client or the server. Fix the error and restart the two halves of Synergy. Hopefully, you get Synergy up and running.
Now click on the “Apply” boxes at the bottom right of the two applications boxes . Hopefully, you're in business. See if you can move your pointing device's cursor between the monitors of the attached computers.
If successful, you can now control two different computers with one keyboard and pointing device.
Here are some situations I ran into.
My Mac Mini has two screens. As this version of Synergy relies on the computer's name and not the placement and number of screens attached to it, this shouldn't present a problem for you.
I also stopped my Synergy session so that I could reconfigure the Windows computer as the server and the Mac as the client. No problems occurred. I didn't have to reenter the password. I just entered the Windows computer's IP address (not it's name in this instance) where the Mac client asked for it.
As I said before, if you want to keep keyboard and pointing devices attached to the client computers, they only work for that local client. Only the server computer's keyboard and pointing device worked across both computers.
The Mac's Synergy software displays an circular icon up in the Menu Bar, Click on it and you can start and stop, hide and show, and finally quit the software.
If the Windows software's icon disappears from view, just go to the Start Menu and click on the program's icon to get the configuration screen again.
Once you've gotten it to work, you can do other things besides move your cursor across two computer's screens. You can copy and paste text and pictures via a shared Clipboard.
What if you have files and folders you want to share between two or more machines? Two ways to handle this situation.
You can set up shared folders between machines. My articles on setting Linux music servers for iTunes have mentioned the Netatalk program. Very handy between a Linux machine and OS X.
The other way uses the Dukto programs. Written by an Italian developer for open-source, they have versions for OS X, Windows, and Linux. In my next article I'll show you how to set it up.
Conclusion
Synergy has eluded my grasp until now. In the past, it eluded Chris Breen’s grasp at Macworld. I figured if Chris could not get it to work with the resources of Macworld behind him…it was impossible.
But now I’ve gotten it to work. Me, just a blogger writing in his shorts from his condo in Canoga Park. I hope it works for you, too. E-mail me at thomasbriant@me.com to tell me your results.
Now as for firewalls. I didn’t have any trouble with them. Windows put up a message, but I only needed to click the “Allow” button and it worked like a charm!
Now for the final question: Will it work after I shut it down the computers? Yes, it did. I had set up my main Mac partition for using Synergy with my Linux machine “Mycroft”. So Synergy rejected my first attempt with the message “Unrecognized client Thomas-PC"
So I just went back to the server screen on the Mac side, changed the name of the client to “Thomas-PC” and it resumed working. Nothing fiddly about it.
Thomas Briant
Editor, MacValley Blog
Thursday, August 21, 2014
Quicken brings out 2015 version for Mac; gets hit with more bad comments than ISIS
Intuit brought out Quicken 2015 today; commenters at Macworld.com were not impressed.
The Macworld review points out that Quicken 2http://www.macworld.com/article/2597380/intuits-quicken-2015-for-mac-revamps-interface-expands-investment-features.html015 does not have all the features of the old Quicken 2007.
Is Intuit a Windows-centric software company that makes Mac software as a hobby? Now I use TurboTax with my Mac and I’ve had nothing but good results.
That said, I don’t plan to upgrade from 2007 to 2015 unless I have to. If Quicken 2007 won’t run on Yosemite, then I’ll consider Quicken 2015. I’ll also consider competitors. Intuit wants $75 for 2015. Would it be worth it?
Wednesday, August 20, 2014
10 Things You Didn't Know Your Mac Could Do - Esquire
This article about 10 things you didn’t know your Mac could do came from Popular Mechanics. Then Esquire.com republished it.
If you’re a Mac maven, you may already know this. If not, take a look and see if you knew about this.
Tom Briant
Editor, MacValley Blog
10 Things You Didn't Know Your Mac Could Do - Esquire: ""
(Via.)
Saturday, August 16, 2014
Revised music royalty rules could hurt Apple's Beats Music, iTunes Radio
Those of you who use Apple products to create music are more than welcome to comment on this story.
I’m not a musician, but I know musicians. They hate Pandora!
Thanks to Appleinsider and GigaOM for these stories.
Tom Briant
Editor, MacValley Blog
Revised music royalty rules could hurt Apple's Beats Music, iTunes Radio: ""
(Via.)
Senior Correspondent Arnold Woodworth's Weekly Roundup
Apple Lays Down Law on Toxic Chemical Use
Apple has banned two chemicals considered hazardous to health from use in the late stages of production of its hardware.
http://www.technewsworld.com/story/80894.html
Apple Taps China Telecom As iCloud Storage Provider For Customers In China
Apple has begun using Chinese servers to store Chinese user data, the company has confirmed.
Apple said that the data stored on China Telecom’s servers will be encrypted, and that it “takes security and privacy very seriously,” however, in order to curtail fears that working with Chinese cloud storage services would provide China’s government with easier access to user data.
http://techcrunch.com/2014/08/15/apple-taps-china-telecom-as-icloud-storage-provider-for-customers-in-china/
Apple's new iPhone exposes 4 stages of stock hype
1. The 'hyperbole' stage
the media reports that a soon to be released product will be GREAT!!
2. The 'from murderously bad to O.K.' stage
Apple more finely calibrates expectations. Wild rumors still abound, but
coverage is generally be more contained and credible.
3. The 'back in bad' stage
How do you write about an exciting product you haven't handled for long?
Easy: Just do it.
Coverage is still over-heated.
4. The 'settle down' stage
In may take a week or two after the actual product release,
but eventually the media will return to what passes for its senses.
http://www.marketwatch.com/story/apples-new-iphone-exposes-5-stages-of-stock-hype-2014-08-13
The Das Keyboard 4 Is The Hacker’s Choice
Founded in 2005 by Daniel Guermeur, the company’s goal was to reproduce the old “clicky” IBM Modem M keyboards of yesteryear. Beloved by programmers for the key travel and sound, these dense slabs of I/O power originally shipped with the original IBM PCs.
The keys have excellent travel – the distance they move down when you tap them – and the clicky switches make it sound like you’re James Bond tapping in nuclear launch codes in the movie Moonraker.
Why is this important? Well, some programmers and writers like to “feel” their keyboard.
http://techcrunch.com/2014/08/12/the-das-keyboard-4-is-the-hackers-choice/?ncid=rss&cps=gravity
The worlds first bionic eye user
http://www.businessinsider.com/second-sight-first-bionic-eyes-2014-8
This Is Microsoft's Very First Web Page ... Back In 1994
http://www.businessinsider.com/microsofts-first-web-page-1994-2014-8
CFPB to bitcoin investors: You're in the 'Wild West'
The Consumer Financial Protection Bureau (CFPB) outlined four major risks: hackers, a lack of protections, cost and scams.
Here are the highlights from the watchdog agency's warning:
Bitcoin users are very, very susceptible to hacks.
Watch out for huge price fluctuations: To call bitcoin's value unstable is putting it mildly.
Bitcoin 'ATMs' are not ATMs at all.
Virtual currencies are still experimental.
You are on your own if something goes wrong.
If you lose your private keys, you're out of luck.
http://www.marketwatch.com/story/cfpb-to-bitcoin-investors-youre-in-the-wild-west-2014-08-11
Why It's Now Impossible to Control Information
1. Every individual is a newspaper.
2. Anything can end up in the court of public opinion.
3. Twitter is the world's most important medium.
http://www.baselinemag.com/social-media/why-its-now-impossible-to-control-information.html
What's the 'Internet of Business Things'?
As more things get connected to each other, how can businesses capitalize on the growing "Internet of Things"? PricewaterhouseCoopers chief technologist Chris Curran talks.
http://live.wsj.com/video/whats-the-internet-of-business-things-2014-08-13-161151315/7301CBAA-4497-4C8A-8AE9-A0A54B8C030B.html
Consumer Reports says Fire phone is an Amazon trap
Amazon's new phone doesn't host many of the most popular apps
http://www.marketwatch.com/story/fire-phone-users-get-trapped-in-amazon-world-2014-08-15
Is artificial intelligence more dangerous than nukes? Could AI replace and even eradicate humans? Some experts say these possibilities are not that far-fetched.
it certainly isn't lunacy-though, at least for now, a machine takeover remains extremely far-fetched.
As we have seen time and time again, too many companies rush too many products to market without adequate consideration for security and outcomes.
Automobiles and medical devices are now targets. Utility grids and traffic systems have already been exploited. Meanwhile, the Internet of things is opening a connected door to a level of online hacking, attacking and cyber-theft that is almost incomprehensible.
Perhaps it's time for humans to begin thinking more intelligently-rather than artificially-about the future.
http://www.baselinemag.com/blogs/will-ai-go-nuclear.html
The Internet's Original Sin
It's not too late to ditch the ad-based business model and build a better web.
Maciej Cegłowski is an important and influential programmer and an enviably talented writer. His talk is a patient explanation of how we've ended up with surveillance as the default, if not sole, internet business model.
The internet spies at us at every twist and turn not because Zuckerberg, Brin, and Page are scheming, sinister masterminds, but due to good intentions gone awry.
Tripod.com tried several different businesses. But, as the author writes, "At the end of the day, the business model that got us funded was advertising. The model that got us acquired was analyzing users' personal homepages so we could better target ads to them."
Advertising became the default business model on the web, "the entire economic foundation of our industry," because it was the easiest model for a web startup to implement, and the easiest to market to investors.
Advertising is the original sin of the web. The fallen state of our Internet is a direct, if unintentional, consequence of choosing advertising as the default model to support online content and services.
An ad supported web grows quickly and is open to those who can't or won't pay. But it has at least four downsides as a default business model.
First it's hard to imagine online advertising without surveillance.
Second, it creates incentives to produce and share content that generates pageviews and mouse clicks, but little thoughtful engagement.
Third, the advertising model tends to centralize the web.
Finally, even attempts to mitigate advertising's downsides have consequences.
One simple way forward is to charge for services and protect users' privacy, as Cegłowski is doing with Pinboard.in. What would it cost to subscribe to an ad-free Facebook and receive a verifiable promise that your content and metadata wasn't being resold, and would be deleted within a fixed window?
It's time to start paying for privacy, to support services we love, and to abandon those that are free, but sell us-the users and our attention-as the product.
http://www.theatlantic.com/technology/archive/2014/08/advertising-is-the-internets-original-sin/376041/
John Oliver’s segment on net neutrality this past June perfectly summed up what his HBO show Last Week Tonight is so good at: transcending apathy.
the Last Week Tonight team has found a way to take a seemingly complicated issue, remove the talking points and cultural baggage surrounding it, break it into understandable parts.
http://www.theatlantic.com/entertainment/archive/2014/08/how-john-oliver-is-procuring-latent-activism/376036/
The Fatal Misunderstanding On "Fast Lanes" on the Internet
The proposal to halt "fast lanes" is in fact a proposal to halt how the Internet has always worked and change how it not only works today but has since I was involved in the building out access for ordinary people from the start -- specifically, from 1993 forward when NCSA Mosaic showed up.
There have always been "fast lanes." We called them private interconnects, and they were a salient feature of not only the early Internet but have featured in it since.
By banning such things you increase costs, in some cases by a hell of a lot.
The correct solution to the perceived (yet not actual) "harm" people are talking about is to enforce anti-trust laws where actual violations take place.
http://www.market-ticker.org/akcs-www?post=229305
Here's The Most Common Mistake People Make In Protecting Their Identity
We hardly try to protect ourselves at all.
There are an average of over 11 million identity theft victims a year in the U.S., with an average of over $4,000 lost per incident.
identity theft is "almost the perfect crime." It's rare that thieves are arrested or prosecuted, the payoff can be enormous.
http://www.businessinsider.com/most-common-identity-theft-mistake-2014-8
IBM has announced the latest version of its neurosynaptic processor -- that is, a processor whose workings are inspired by the human brain.
http://www.technewsworld.com/story/80868.html
Wednesday, August 13, 2014
Four Finder timesavers every smart Mac user should know | Macworld
Here’s four simple Finder tricks that can save you time and aggravation. (thank you, Macworld!)
Tom Briant
Editor, MacValley Blog
Four Finder timesavers every smart Mac user should know | Macworld: ""
(Via.)
Saturday, August 9, 2014
Senior Correspondent Arnold Woodworth's Weekend Roundup
This Person Says that Apple's Future iWatch Won’t Go Straight to the Bottom Dresser Drawer
He wrote:
"Apple, in my opinion, is looking at 1) previously unexplored utility in wearables 2) health monitoring that makes sense and 3) fashion. The elegant combination of these elements will set the iWatch apart from geeky smartwatches that can tell us the atmospheric pressure in millbars in Hong Kong."
http://www.macobserver.com/tmo/article/why-the-apple-iwatch-wont-go-straight-to-the-bottom-dresser-drawer
Why Some Schools Are Selling All Their iPads
Four years after Apple introduced its popular tablet, many districts are switching to laptops
It seems that laptops with keyboards are more useful than tablets.
the laptop versus tablet debate is far from settled nationwide. The education market is currently split fairly evenly between the two types of devices.
http://www.theatlantic.com/education/archive/2014/08/whats-the-best-device-for-interactive-learning/375567/
It Really Pays To Be An Apple iOS Developer, But There's Still Hope For Android
Apple iOS developers spend most of their time coding. Android developers? They use the bulk of their time testing and debugging their code.
Making matters worse, iOS developers make more money, on average, than their Android peers.
http://www.businessinsider.com/android-vs-ios-developers-2014-8
The Internet is a dangerous place, a fact that may work to Apple’s advantage.
Apple is trying to position itself as the only company that really cares about Internet security.
http://fortune.com/2014/08/09/live-this-is-cyberwar/
The Most Enduring (and Endearing) Features of OS X Throughout the Years. Part I
http://www.macobserver.com/tmo/article/the-most-enduring-and-endearing-features-of-os-x-throughout-the-years.-part?utm_campaign=tmo_popular_block
Apple And Samsung Drop Patent Disputes Against Each Other Outside Of The U.S.
But not inside the U.S.
http://www.forbes.com/sites/amitchowdhry/2014/08/06/apple-and-samsung-drop-patent-disputes-against-each-other-outside-of-the-u-s/
Judge tells of Silicon Valley ‘fear’ of Steve Jobs
http://www.ft.com/intl/cms/s/0/ee753584-1f5f-11e4-9689-00144feabdc0.html#axzz39vjpyvVr
11 Apps That Every Political Junkie Should Have On Their Phone
http://www.businessinsider.com/11-surprisingly-useful-apps-for-political-junkies-2014-8
The Wearables Revolution will be the biggest market ever
I'm starting to bet a big part of my reputation and a fair amount of my capital on the Wearables Revolution.
I've just come to the realization that the App Revolution is actually just getting started. The Wearables Revolution, which only works because we've become such an app-centric economy, is going to make an even bigger impact than the Smartphone and Tablet Revolutions did with apps.
That is, wearables are to the smartphone and tablet what the smartphone and tablet were to PCs.
The reason apps for wearables is so important is because of the very simple interfaces required by the wearable-form factor.
The Wearables Revolution is going to make a lot of people a lot of fortunes over the next five to 10 years, as people start buying three, five or even 10 wearable computers for every one smartphone they have.
http://blogs.marketwatch.com/cody/2014/08/07/the-wearables-revolution-will-be-the-biggest-market-ever/
The worlds first bionic eye user
http://www.businessinsider.com/second-sight-first-bionic-eyes-2014-8
Robots Will Take Care Of Old People In The Future
http://www.businessinsider.com/a-robot-to-care-for-you-in-old-age-2014-6
Mankind Is Getting Ready To Turn Over Most Decisions To Robots
If robots become more cognitively capable than humans, then what happens to ... everything?
Will super-intelligent robots decide to eliminate humans some day?
http://www.businessinsider.com/decision-making-robots-could-rule-humans-2014-7
Elon Musk says:
"We need to be super careful with artificial intelligence (AI). Potentially more dangerous than nukes."
Nick Bostrom is the founder of Oxford’s Future of Humanity Institute. That group recently partnered with a new group at Cambridge, the Centre for the Study of Existential Risk, to study how things like nanotechnology, robotics, artificial intelligence and other innovations could someday wipe us all out.
the robot takeover is not imminent.
But it seems like it's something all of us should "keep an eye on."
http://www.businessinsider.com/elon-musk-compares-ai-to-nukes-2014-8
An interesting article that compares the Bitcoin rush to the California Gold Rush
The most successful people in the gold rush were sellers of mining equipment.
Looks like the sellers of specialized computers for mining bitcoins are doing well today.
http://moneymorning.com/2014/07/31/investing-in-bitcoin-a-gold-rush-for-the-digital-age-graphic/
How to control facebook ad tracking.
http://live.wsj.com/video/how-to-control-facebook-ad-tracking-2014-08-05-141154050/668A60DB-C0C0-4EB4-83D8-A9372DE27E75.html
AOL still has 2.3 million dialup subscribers—and they’re very profitable
AW comment: I am surprised.
http://qz.com/245585/aol-still-has-2-3-million-dialup-subscribers-and-theyre-very-profitable/
In 2015, it won't matter if hackers steal your password
New technologies could replace passwords next year
The password has been the "is it really you?" test since the 1960s.
Since then, passwords have become an omnipresent nuisance for both users and security officers-perpetually forgotten and inevitably stolen.
Two out of every three data breaches involve the exploitation of weak or stolen passwords.
Until 2015, people can opt for two-factor authentication. In most cases, that means websites will send security codes to users' inboxes or smartphones, which they must enter in addition to the username and password when logging in. It's imperfect, and hackers can sometimes circumvent or spoof it, but it's better than not opting into a second layer of security at all-especially given that most people don't change their passwords in the first place or still name them after their cats.
AW comment:
I'm not convinced that the password replacements are less hackable than passwords, because they still involve sending and receiving data between computers.
http://www.marketwatch.com/story/in-2015-it-wont-matter-if-hackers-steal-your-password-2014-08-08
Blog Archive
-
▼
2014
(176)
-
▼
August
(20)
- An essential OS X Mavericks problem-solving guide ...
- Senior Correspondent Arnold Woodworth's Weekly Update
- Newegg rolls out same-day delivery in Los Angeles ...
- Rumored 12.9-inch iPad could be better for busines...
- The LA Unified School District, iPads, and other news
- How I got Synergy to work with Ubuntu Linux withou...
- Senior Correspondent Arnold Woodworth's Weekly Rou...
- Dukto-cross platform file transfer between Windows...
- How I got the latest version of Synergy to work re...
- Quicken brings out 2015 version for Mac; gets hit ...
- 10 Things You Didn't Know Your Mac Could Do - Esquire
- Revised music royalty rules could hurt Apple's Bea...
- Senior Correspondent Arnold Woodworth's Weekly Rou...
- Four Finder timesavers every smart Mac user should...
- Senior Correspondent Arnold Woodworth's Weekend Ro...
- The iPad doesn't come with a keyboard and other ob...
- Amazon.com: Batman The Complete TV Series Limited ...
- How to Speed Up, Clean Up, and Revive Your Mac
- 5 Smart Playlists That Make iTunes Worth Using
- Senior Correspondent Arnold Woodworth's Weekly Rou...
-
▼
August
(20)