The MacValley blog
![]()
Welcome to the MacValley blog, your first stop for all the latest MacValley news and views.
|
The MacValley blog Editor: Tom Briant
|
Labels used in posts
|
To search the blog posts please use the box below
Wednesday, August 30, 2017
Tuesday, August 29, 2017
News and Views from the Editor-How to find a new off-site backup plan!
Question: When will macOS 10.13 arrive? I would expect it to arrive by the end of October.
If Crashplan for consumer is discontinued, what are my options?
First of all, DON’T PANIC!! Crashplan won’t immediately delete your archives and kick you to the cyber curb. No, read this PC World article for ideas of what to do next.
For Mac owners specifically, Glenn Fleischmann of Macworld has some ideas for you, too. Regarding your off-site backup options.
If you’ve considered a Virtual Private Network (VPN) for home, consider these options, as shown in PC Magazine.
Many users and reviewers consider Excel as their default choice for heavyweight computation. Should you always use Excel, though? Preston Gralla compares Excel to Google Sheets, the on-line spreadsheet, and finds Sheets superior for collaboration in groups, though Excel still leads in many areas.
Finally, what’s a good second monitor for a Mac? Macworld UK examines the offerings. Prices are stated in pounds, but you can use the technical information now.
Tom Briant
Editor, MacValley Blog
Monday, August 28, 2017
Senior Correspondent Arnold Woodworth's Weekly Web Wrap-up for Sunday 8-27-2017
They should have hung their heads in shame instead. Apple took them to the cleaners, and their taxpayers will be paying the bill. The politicians talked as though the data center would put Waukee on the map as a first-class high-tech center. The truth is that it will mark Waukee as a first-class patsy.
Credentials stored in the cloud succumb to forensic software
Jobs’ hesitancy proved to be insightful. In fact, exceptionally so: Seven years later we’re still debating what the iPad actually is.
The latest hint? Six lovingly crafted videos that promote iOS 11 features that were designed specifically for the iPad and iPad Pro. For example, a Mac-like dock with touch user interface.
“AccuWeather’s app employed a Software Development Kit (SDK) from a third-party vendor (Reveal Mobile) that inadvertently allowed Wi-Fi router data to be transmitted to this third-party vendor,” the company wrote in a statement accompanying the app update.
Parallels Desktop 13 offers MacBook Pro Touch Bar support and a host of performance enhancements that make it the go-to solution for running Windows on Mac.
Some devices are designed to listen to you, but you can axe active listening. Here's how.
Turning off active listening isn't always an option, or it's difficult to find, in large part because that's often the point of having such a device. But if you'd like to exercise more control over how Siri, Cortana, Alexa, or Google listen in on your life, read on for the details.
The self-driving car was a dead end.
“She told me she knew immediately that Henry was extremely intelligent. She said nothing about Gus.”
Years later, enter Siri. The voice-recognition software performs a wealth of functions for the autistic community: conversationalist, babysitter and elocution trainer. Like Disney animations, Siri provides a comforting commercial sameness. She has enabled Gus to have real, sustained conversations, albeit ones about turtles.
Users will now be able to sign up for the platform without waiting on a list.
Native image hosting, GIFs, quote posts, private messaging, and live streaming are all recent additions to the social network, as well as a unique payment model which allows users to optionally pay a fee monthly for extras in an attempt to keep Gab ad and investor free.
Brave also offers Brave Payments, in which a user can allocate donations to favorite websites.
Infogalactic launched as an alternative to Wikipedia during the height of the toxic political climate of 2016. Wikipedia moderators at the time began deleting information that could paint conservatives positively, and replaced those articles with information from editorials with notorious left-wing biases. Vox Day, founder of Infogalactic, said these problems stemmed back to Wikipedia’s beginning.
The mantra of Gab.ai since its opening day has been #SpeakFreely. CEO Andrew Torba saw the many controversial bannings of vocal Trump supporters across Twitter, how left-leaning pundits could get away with saying far worse than their right-wing counterparts, and finally said enough is enough. Torba wanted to experience social media without censoring from the other networks, and the only way he saw to do that was to create his own platform.
For years, an online speech battle has played out on social media platforms such as Twitter, Facebook, and Reddit. It typically goes like this: Activists pressure the company to crack down on content they consider offensive. In some cases, they call for a user or organization to be banned outright. The social media company then has a choice: Take action, or disclaim responsibility for the content.
Cutting off domain hosting is a potent weapon against the purveyors of objectionable content—and it could be double-edged.
the structure of their platforms plays an important role in shaping the way we communicate online. For example, Facebook’s news feed, as I’ve explained, inherently prioritizes certain types of speech and interaction over others. In other words, it can’t credibly claim neutrality with respect to content when its algorithms are already tilting the playing field.
The argument that web hosts and domain registrars should refrain from policing the content of the sites they serve, however, seems like a stronger one. GoDaddy’s service doesn’t distinguish between “high-quality” and “low-quality” content the way Facebook’s or Google’s algorithms do. Cloudflare may serve hateful or violent clients along with laudable ones, but it isn’t in the business of recommending or suppressing their content.
Moreover, if Facebook or Twitter bans a group, it can still take its message to any number of other social networks, or start its own. When domain registrars blacklist it, they effectively banish it from the public internet. It’s a far blunter instrument, wielded by a company with no experience or expertise in passing editorial judgments, and little track record of public accountability for its actions.
Those back-end service providers may look like attractive targets for progressive activists today, when they hold the power to exile a noxious and violent white supremacist group to the web’s shadows with the flick of a switch. But it’s hard to shake the feeling that concentrating editorial discretion in these companies’ hands is a gambit that will eventually backfire.
http://www.slate.com/articles/technology/technology/2017/08/the_one_big_problem_with_godaddy_dropping_the_daily_stormer.html
For the Islamic State, that began to happen in the last few years.
“It is the sense of Congress that WikiLeaks and the senior leadership of WikiLeaks resemble a non-state hostile intelligence service often abetted by state actors and should be treated as such a service by the United States,” a section of the Act reads.
The Act almost unanimously passed a Senate panel last month 14-1, rejected by only one man, Sen. Ron Wyden, an Oregon Democrat who staunchly opposed the measure due to the provision that was snuck in about WikiLeaks.
Tuesday, August 22, 2017
Wednesday, August 16, 2017
Saturday, August 12, 2017
Fixing your old computer the easy way and saving some coin, too!
My brother’s computer went blank yesterday. He e-mailed that the screen was broken.
When I got home I looked at the screen. No apparent physical damage, no distorted picture, just ….nothing.
To cut to the chase, I resolved the problem and saved him visiting a repair shop by simply removing the memory modules and then reseating them to ensure a firm physical and electrical connection.
After doing so, the computer came back on and went through the cyber equivalent of “spectacles, testicles, watch and wallet, “ for several minutes before returning to normal operation.
I have had this happen to three different computers, where the On/Off cycling causes tiny metal parts to flex microscopically and work its way out of their sockets.
Now for the details. You’ll need a appropriate sized screwdriver, some good sense, and a bit of patience. Oh, and wash your hands!
Now lay the computer on a clean cotton towel to ensure small parts don’t roll away and get lost on the floor.
How I tested the computer
I tested the video output by plugging in a VGA monitor. I’m a full-on nerd, so I’ve got a couple of extra monitors. Nothing, though, came up. I pressed all the buttons on the side of this Samsung monitor and nothing, but nothing, came up! “It’s dead Jim”
So the problem went beyond a problematic LCD screen. So I thought through my experiences from the past 30 years of working with computers. An old Windows 2000 computer sprang back to life when I moved its single 64 Mb memory chip to another socket 3 years ago. My own late 2011 Mac mini came back to life after I reseated the hard drive’s connections. So I figured it was worth a shot on my brother’s computer.
Now to the details
First, read the manual. “When all else fails, read the instructions,” is an old part of the Murphy’s Laws. You want to advance past fumbling amateur to Grand Nerd Extraordinaire? Read the instructions first!
If you have access to another computer, open up the search engine, whether Google, Bing, Yahoo, or DuckDuckGo, and enter the following “service manual <name of your broken computer>” You can skip the quotation marks and arrows. In my case, I entered service manual Inspirion 6400 and up popped where to go for the Dell service manual.
It’s a PDF that I downloaded. So opening it up, I found the section for Memory Modules. I read that before doing anything. It kept referring to the first steps you should always take when fixing the computer. So like an intelligent person, as you are too, I read them. Unplug the computer, touch a metal surface to discharge any static electricity, and remove the battery.
So I removed the Dell battery, which proved even easier than removing an Apple battery. Just push a latch to one side and pull up gently (!) on the battery to remove it. Set it aside and see if it displays signs of bulging or leaking. Those are not good and fortunately, I didn’t see them with this computer’s battery.
Now to open the memory module bay, you’ll need a teeny-weeny Phillips head screwdriver to unscrew the captive screws holding the bay’s cover in place. Go to Fry’s to get a computer repair kit if necessary. From earlier work on the Mac mini, I had the necessary screwdriver (thank you, Other World Computing!)
Here is the teeny-weeny little Phillips head that I got from Other World Computing while doing a project.
Here is a computer repair kit that I found at Fry’s. It costs about $24 and should cover 99% of situations you encounter.
I unscrewed the captive screws and laid the plastic cover aside.
One side piece of advice, use an old cotton towel on your desktop if you have small screws to keep them from rolling on to the floor.
Now for the money shot!
I looked at the memory chips or modules. Nothing unusual about them. I read the instructions again, which said to GENTLY use your fingers to spread the clips holding the module(s) in place and pull out the module. Oh, and make sure to discharge any static electricity by touching a metal object first!
I looked at the memory module. Hmm, nothing special, just a stock DDR2 memory module. No signs of corrosion or damage. So I reinserted the module into its socket GENTLY and made sure of a firm physical fit.
I reattached the memory bay cover, reinstalled the battery, flipped the computer over, and turned it on. Voila! The Windows 10 boot up sequence began. As I wrote before, Windows goes through a self-diagnostic procedure if it detects something drastic happened. Soon the desktop appeared with my brother’s user name. He sat down and logged in.
He was ecstatic! He didn’t need a new computer, he didn’t need to track down a computer repair shop on Saturday, and he could get back to work.
As my reward, he fixed me dinner. Yum!
And that’s all there was to it.
Tom Briant
Editor, MacValley Blog
Sunday, August 6, 2017
Xnconvert solves the problem of converting old graphics files to new formats
I needed to convert several old graphics files in MacPaint and PC Paintbrush format. I needed to do this with macOS, Ubuntu Linux, and Windows.
I bumbled around looking for solutions. I figured out awkward workarounds in each case, but I believed someone must have arrived at a better solution.
Someone has, and that solution is the graphics batch converter Xnconvert. It easily converted my old files into the contemporary Windows .bmp format, which has been around since at least 1992 in Windows 3.1.
This product reads 500 different formats (!) including some even rarer than MacPaint, such as Atari ST’s Neochrome. It writes to 70 different formats.
The developer asks for a donation to help defray costs. He wants $6.48. Perfectly reasonable and I paid it as quick as I could.
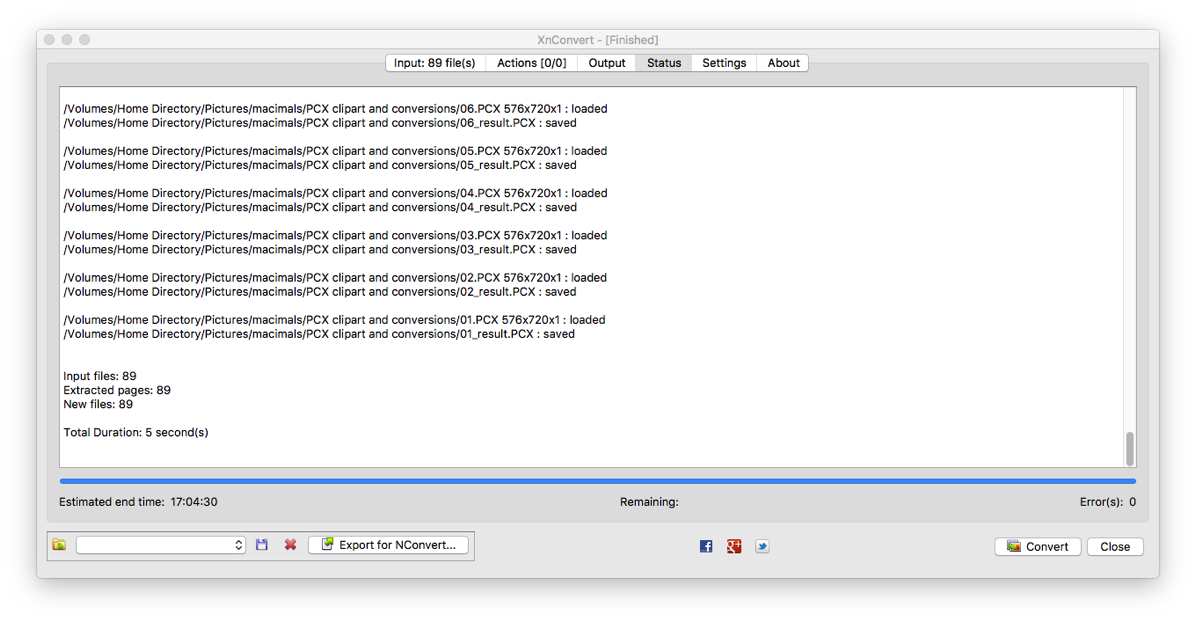
Xnconvert has versions for Windows, macOS, and various distros of Linux. I got it up and working on macOS and Ubuntu Linux quickly and easily. It converted the old files quickly and easily. It displays the progress of each conversion and its success or failure.
I wholeheartedly recommend this product to anyone faced with converting old graphics files in a plethora of formats into a common contemporary format usable across Windows, macOS, and Linux.
This shows the input. I’ve selected the folders that I want to convert. You can convert nested folders.
This shows the speed of the conversion process
This shows the output settings, where you select the output folder and format.
Tom Briant
Editor, MacValley Blog
Wednesday, August 2, 2017
Senior Correspondent Arnold Woodworth's Weekly Web Wrap-up for Tuesday 8-1-2017
Yet in China, when faced with a broad demand by the Chinese internet authority, it was Apple that blinked.
“Apple’s response is tremendously disappointing,” said Eva Galperin, director of cybersecurity at the Electronic Frontier Foundation
http://www.mercurynews.com/2017/07/31/apple-pulling-vpns-from-the-chinese-app-store/
https://www.dexigner.com/news/30353
Who hacks the hackers? An inside look at hunting for insecure connections at the largest cybersecurity gathering in the world.
If your device gets hacked, you end up on the Wall of Sheep.
Thankfully, the hackers aren't after your identity or your money or anything else that could do you real harm. But they don't mind publicly shaming you into being more thoughtful about your security.
When I'm surfing the web, experts say I should use a virtual private network, which routes all your information through secure computers. It's also good to use multi-factor authentication, meaning I get sent a password by text or a special code in an app to be able to log in.
"The bug we found is exactly the kind of bug law enforcement or intelligence would look for in an end-to-end encryption system,” Alex Radocea told ZDNet.
1. Unlock your car doors
2. Measure your lover’s heart beat
Leaderboards is geared toward those who want to inject some friendly competition into their active lifestyles.
The incredible scope and applications of GEOINT is laid out on the .mil website’s About page but their image collection from DigitalGlobe can best be described as … penetrating…
Blog Archive
-
▼
2017
(79)
-
▼
August
(8)
- How to Batch Rename Multiple Files on Your Mac
- News and Views from the Editor-How to find a new o...
- Senior Correspondent Arnold Woodworth's Weekly Web...
- The Best Mac Apps
- How to fix a Mac: troubleshooting the most common ...
- Fixing your old computer the easy way and saving s...
- Xnconvert solves the problem of converting old gra...
- Senior Correspondent Arnold Woodworth's Weekly Web...
-
▼
August
(8)