The MacValley blog
![]()
Welcome to the MacValley blog, your first stop for all the latest MacValley news and views.
|
The MacValley blog Editor: Tom Briant
|
Labels used in posts
|
To search the blog posts please use the box below
Sunday, July 31, 2016
5 free Web tools to organize your thoughts | PCWorld
5 free Web tools to organize your thoughts | PCWorld: ""
(Via.)
This article covers 5 Web-based outlining tools. You can use them with your Mac or Windows or even Linux.
I’m going to cover using Fargo with your Mac in a subsequent article.
Tom Briant
Editor, MacValley Blog
Friday, July 29, 2016
Senior Correspondent Arnold Woodworth's Special Web Wrap-up for Friday July 29 2016
I tried to give up using my phone for a week and it really didn't work out.
PowerPC chips to Intel chips and essentially transplanting the the "brains" of its entire line of personal computers.
PC sales are slumping at a significantly faster rate than during the 2008 recession.
Interesting reader comments.
http://www.computerworld.com/article/3094235/apple-mac/apples-mac-sales-fall-economies-shudder.html
If bitcoin is property, as the IRS agrees it is, and not money, then arguments by regulators like the CFTC, which says bitcoins are a commodity and need to be regulated by them, or the SEC, which says bitcoins fit the definition of securities, so they should be regulated by them, fall by the wayside.
For now the Court’s ruling appears to set the precedent that bitcoins are property.
But that legal definition will be challenged, most likely in an appellate court ruling if the Espinoza case is pursued by prosecutors.
Especially when you’re travelling like I am.
If you carry…
…a smart phone… you’re a target.
…a laptop… you’re a target.
…a tablet… you’re a target.
https://techcrunch.com/2016/07/11/mits-anonymous-online-communications-protocol-riffle-could-beat-tor-at-its-own-game/
Security researchers have discovered a new malware threat that goes to great lengths to remain undetected while targeting energy companies.
The goal of droppers is to prepare the field for the installation of other malware components that can perform specialized tasks. Their priority is to remain undetected, gain privileged access and disable existing protections. These are all tasks that Furtim’s Parent does well.
http://www.computerworld.com/article/3094236/security/stealthy-cyberespionage-malware-targets-energy-companies.html
Foreign Hackers Target Thousands of Gmail Users Every Month
Google revealed that it sends 4,000 warnings monthly about state-sponsored cyberattacks.
http://www.theatlantic.com/technology/archive/2016/07/foreign-hackers-target-thousands-of-gmail-users-every-month/490883/
It’s now a federal crime to share your Netflix password
A federal court ruled that unauthorized password sharing was illegal.
http://www.charlotteobserver.com/news/nation-world/national/article89050727.html
Saturday, July 23, 2016
Excellent review of CleanMyMac 3.x by J P Zhang
Hi Everyone:
JP Zhang, the editor of SoftwareHow, asked me to spread the word about this review of CleanMyMac. I’m happy to do so.
Please click on this link to read his article.
Tom Briant
Editor, MacValley Blog
Monday, July 11, 2016
Monday, July 4, 2016
Your top questions to Mac 911—and some answers | Macworld
Your top questions to Mac 911—and some answers | Macworld: ""
(Via.)
Again, Happy 4th! Got a question? Macworld may have covered it already!
Tom Briant
Editor, MacValley Blog
Can’t save a Microsoft Office document? Look for the forward slash | Macworld
Can’t save a Microsoft Office document? Look for the forward slash | Macworld: ""
(Via.)
Happy 4th! Don’t use forward slashes in Microsoft Office documents!
Tom Briant
editor, MacValley Blog
Sunday, July 3, 2016
Senior Correspondent Arnold Woodworth's Weekly Web Wrap-up for Sunday, July 3, 2016
Video:
Want to see the latest progress at Apple’s new headquarters now under construction in Silicon Valley? One documentarian has you covered.
Matthew Roberts has published his latest video taken from a drone of Apple’s Campus 2 in Cupertino, Calif., including a peek at the main “spaceship” building as well as some of the others nearby.
http://fortune.com/2016/06/30/apple-spaceship-campus-flyover/
Video:
Take a Sneak Peek at Apple's Mindblowing $5 Billion Spaceship Campus
The Apple spaceship is finally looking like it’s almost ready to blast off.
http://gizmodo.com/here-s-a-sneak-peek-at-apple-s-mindblowing-5-billion-s-1782883483
7 clever tricks that will make your iPhone or iPad better
http://www.foxnews.com/tech/2016/07/02/7-clever-tricks-that-will-make-your-iphone-or-ipad-better.html
There will never be anything like the iPhone again
Nine years and a few days ago, Apple released the iPhone, and the world was never the same.
Well, there's some bad news and some good news.
The bad news is that we probably won't another big, world-shaking product introduction like the iPhone any time soon.
The good news is everybody's right! The next big thing is already here, and you probably haven't even noticed it yet.
the iPhone wasn't the first of a new kind of computer, it's the last of the old.
Just know that the arrow of history is pointing towards a whole galaxy of smart everything in constant communication. Where an iPhone is pretty good at lots of things, you're going to see more dedicated tools for specific tasks start to emerge, all powered by intelligence and connectivity.
http://www.techinsider.io/iphone-vs-virtual-reality-and-headphones-and-robotics-2016-7
10 facts about the Apple-1, the machine that made computing history
On June 29, 1975, Steve "Woz" Wozniak tested the first prototype of the Apple computer, and history was made.
http://www.cnet.com/news/apple-1-the-machine-that-made-computing-history/
The oldest library in the world just opened to the public — here's a look inside
1,157 years after it first opened, the world's oldest library has finally been restored and unveiled to the public.
Located in Fez, Morocco, the al-Qarawiyyin library is part of the world's oldest continually operating university, al-Qarawiyyin University, which opened in 859.
http://www.techinsider.io/inside-al-qarawiyyin-the-oldest-library-in-the-world-2016-6
Google's Satellite Map Gets a 700-Trillion-Pixel Makeover
The new map, which activates this week for all users of Google Maps and Google Earth, consists of orbital imagery that is newer, more detailed, and of higher contrast than the previous version.
Most importantly, this new map contains fewer clouds than before—only the second time Google has unveiled a “cloudless” map. Google had not updated its low- and medium-resolution satellite map in three years.
http://www.theatlantic.com/technology/archive/2016/06/google-maps-gets-a-satellite-makeover-mosaic-700-trillion/488939/
The internet does not just radicalize would-be terrorists, it radicalizes everybody.
This video starts off silent, until you click its volume control.
https://twitter.com/billmaher/status/747553266414718977
Powerful facial-recognition software can shred your privacy with just 1 photo
Nearly 250 million video surveillance cameras have been installed throughout the world, and chances are you’ve been seen by several of them today. Most people barely notice their presence anymore — on the streets, inside stores, and even within our homes. We accept the fact that we are constantly being recorded because we expect this to have virtually no impact on our lives. But this balance may soon be upended by advancements in facial recognition technology.
Soon anybody with a high-resolution camera and the right software will be able to determine your identity.
A new app called FindFace, recently released in Russia, gives us a glimpse into what this future might look like. Made by two 20-something entrepreneurs, FindFace allows anybody to snap a photo of a passerby and discover their real name — already with 70% reliability.
http://www.marketwatch.com/story/facial-recognition-will-soon-end-your-anonymity-2016-06-02
A hacker wants to sell 10 million patient records on a black market
These records are being sold in four separate batches. The biggest batch includes 9.3 million patient records stolen from a U.S. health insurance provider.
The three other batches cover a total of 655,000 patient records, from healthcare groups in Atlanta, Georgia, Farmington, Missouri, and another city in the Midwestern U.S. The hacker didn't give the names of the affected groups.
The hacker wants a total of 1,280 bitcoins for the data he stole.
Healthcare providers are seen as especially vulnerable to cyberattacks because they haven't invested as much in IT security, according to experts.
http://www.pcworld.com/article/3089086/a-hacker-wants-to-sell-10-million-patient-records-on-a-black-market.html
The hacker said in one listing that the data was stored on an "accessible internal network" and stored in plaintext -- which if true would be in violation of federal healthcare privacy rules.
http://www.zdnet.com/article/hacker-advertising-huge-health-insurance-database/
The best free weapon for businesses to fight phishing fraud
The organizational culture instinctively and intuitively gave employees all the tools to spot a phish. No technical tools, but the cultural human element allowed our close knit humans to immediately spot complex spear phish campaigns.
This close knit and well connected organization working culture was my best weapon to identify and defeat the phish campaign! And best of all it was already there - no purchase needed!
I discovered this weapon when other staff members in the organization forwarded phish emails into the information security office. The quality of the phish emails was very good. No spelling mistakes and excellent grammar. The wire instructions in the Business email compromise (BEC) phish emails were well laid out. The email had all the hallmarks of a professional spear phish. Yet my people were catching these phish emails very easily. The folks catching the phish and forwarding to me were not computer geeks but regular office staff with average skills in computing and security awareness. How were these folks able to spot these sophisticated spear phish and regular phish attacks?
The more I dug in I realized that while the malicious phish campaign had taken pains to craft a well-polished and targeted phish, they tripped up on some common details:
• The salutation was off. Somebody we refer to as William was named as a Bill in the email or the other way around. James in accounting was referred to as James in the email and not what we normally used, which was ‘Jim’
• The sender signature was incorrect in a similar manner; For example the phish email would say John Doe instead of simply John
• The style of the content was different. The wording of the content seemed different. The email was often very abrupt with no ‘please’ or in some cases no sender name in the message body.
http://www.csoonline.com/article/3086870/security/the-best-free-weapon-to-fight-phishing-fraud.html
Bart ransomware shows it can be effective without sophisticated encryption
In order to protect themselves against ransomware attacks, users should be wary of email attachments, especially those with unusual file extensions like JS. They should also keep their computer software up to date, especially their browsers and browser plug-ins, and they should implement a file backup routine that involves an offline or offsite backup location.
A new ransomware program making the rounds uses a simple, yet effective technique to make user files inaccessible: Locking them in password-protected ZIP archives.
The new threat is called Bart.
Bart stands out through its simplicity and efficiency, according to researchers from security vendor PhishMe.
Unfortunately for users, Bart is proof that attackers don't need advanced crypto knowledge or complex infrastructure to create reliable and effective ransomware programs. That's why this cybercrime model is so successful and why it won't go away anytime soon.
http://www.computerworld.com/article/3088912/security/bart-ransomware-shows-it-can-be-effective-without-sophisticated-encryption.html
Android’s full-disk encryption just got much weaker—here’s why
Unlike Apple's iOS, Android is vulnerable to several key-extraction techniques
A blog post revealed that, in stark contrast to the iPhone's iOS, Qualcomm-powered Android devices store the disk encryption keys in software. That leaves the keys vulnerable to a variety of attacks
http://arstechnica.com/security/2016/07/androids-full-disk-encryption-just-got-much-weaker-heres-why/
Video:
JOHN MCAFEE: This is why the US is losing the ‘cyber war’ to China and Russia
http://www.businessinsider.com/john-mcafee-china-russia-cyber-war-hackers-2016-5
Attackers are developing an aggressive new ransomware program for Windows machines that encrypts user files as well as the computer's master boot record (MBR), leaving devices unable to load the OS.
The program is dubbed Satana -- meaning "Satan" in Italian and Romanian ... functional but still under development.
http://www.computerworld.com/article/3090543/security/satana-ransomware-encrypts-user-files-and-master-boot-record.html
When Should Hacking Be Legal?
A group of academics and journalists say a federal computer-fraud law criminalizes their work.
When Aaron Swartz, a prominent programmer and digital activist, was arrested in 2011, he was halfway through a fellowship at Harvard’s Center for Ethics. Faced with the possibility of decades in prison and up to a million dollars in fines, Swartz took his own life in 2013.
The ordeal brought CFAA—a 30-year-old anti-hacking law that has been updated half a dozen times to keep up with new technology—under intense scrutiny.
Now, a group of academic researchers and journalists is suing the government, challenging the constitutionality of part of CFAA. With the help of the American Civil Liberties Union, they’re targeting the portion of the law that makes it illegal to break private companies’ terms of service, claiming that the rule violates researchers’ and journalists’ rights to conduct research and investigations in the public interest, as guaranteed by the First Amendment.
The four professors bringing the lawsuit are conducting research into racial and other discriminatory biases in online services.
http://www.theatlantic.com/technology/archive/2016/07/when-should-hacking-be-legal/489785/
Saturday, July 2, 2016
How to Sort your Finder's Display of Apps by Date Last Opened
I’ve read the advice in several articles that to improve your Mac’s performance, cut back on the number of installed apps.
So, how do you tell which apps you use frequently and which apps you haven’t touched in years? Can your Mac tell you?
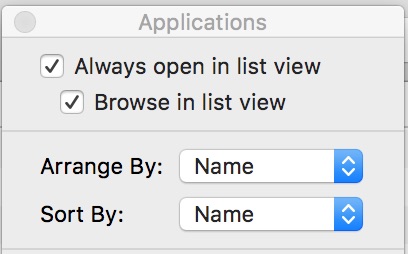
Go to the Finder and open a window showing your apps. By default, the Finder shows them in alphabetical order.

To show them in order of apps last used, do the following:
- Change the Arrange by criteria from Name to Date Last Opened.
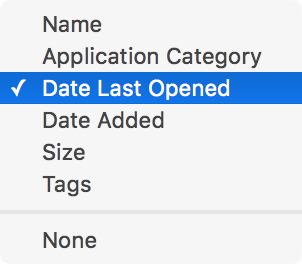
- Change the Sort by criteria from Name to Date last Opened.

- Add another item column (Date Last Opened) by checking the box next to Date Last Opened.
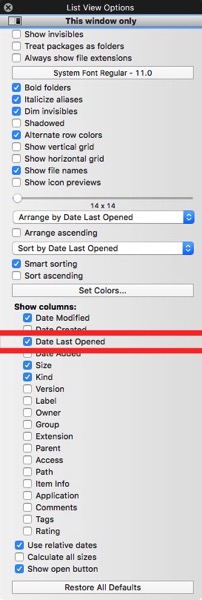
Now your Finder window displays the Apps sorted by time and date last opened.

Now it’s up to you to decide which ones you keep and which ones you archive.
Tom Briant
Editor, MacValley Blog
Time to Start Backing up your Mac!
Hi, All. It’s the middle of the year. Have you set up a backup plan for your Mac/Windows/Linux box? if not, do so!
For your Mac, you need to set up Time Machine. Just go to Costco or Frys or Best Buy or Staples or Office Depot/Office Max or go on-line to Amazon or Newegg to get an external hard drive. Spend $100 for a 2 Terabyte portable drive.

That’s it! Just a small plastic box and a USB 3.0 cable. Just plug it into a USB 3.0 or 2.0 port on your Mac and go to Time Machine. It will walk you through setting it up and even formatting it in the Mac format. It probably came formatted for Windows.
But make those backups! How much would it cost you to recreate (if possible) all those files you spent the past 10 to 20 years working on at $20/hour? See, it pays to get a backup drive and dedicate it to specifically backing up your Mac!
(thanks to DX.com for the use of their Western Digital Elements picture)
Tom Briant
Editor, MacValley Blog
Blog Archive
-
▼
2016
(123)
-
▼
July
(9)
- 5 free Web tools to organize your thoughts | PCWorld
- Senior Correspondent Arnold Woodworth's Special We...
- Excellent review of CleanMyMac 3.x by J P Zhang
- How to fix a long pause with a black startup scree...
- Your top questions to Mac 911—and some answers | M...
- Can’t save a Microsoft Office document? Look for t...
- Senior Correspondent Arnold Woodworth's Weekly Web...
- How to Sort your Finder's Display of Apps by Date ...
- Time to Start Backing up your Mac!
-
▼
July
(9)


