The MacValley blog
![]()
Welcome to the MacValley blog, your first stop for all the latest MacValley news and views.
|
The MacValley blog Editor: Tom Briant
|
Labels used in posts
|
To search the blog posts please use the box below
Sunday, December 28, 2014
The Editor's Year-End Summary for 2014
Everyone has year-end business to clear up. In some cases, business will post year-end entries to the accounting systems. Inventories will be taken.
In other cases, people will get over year-end colds & flu brought in from work, school, or the mall. Student still snuffing will work on terms papers.
In my cases, I’ll post accounting entries tomorrow for payroll. I avoided the malls and got my flu shot at work, so I haven’t come down with any diseases. I don’t have any papers to write for a class. I do have to write my year-end round-up for the MacValley Blog.
This is my personal view. If you would like to respond to it, my e-mail address is at the top of the page. 500 words in plain text, RTF, Word, Pages, or OpenOffice format. Pictures submitted separately from article, please.
The Single Biggest Event relating to Apple in 2014
The iWatch marks the biggest event for Apple in 2014. Portable health monitoring is the next big frontier for Apple to tackle. Of course, it’s expensive to begin with. So were the iPod and iPhone at their inceptions.

Will other companies want to imitate Apple? Of course. I expect a flood of Android imitations.
The Second Biggest Event relating to Apple in 2014
The introduction of the low-end iMac and the low-end Mac Mini mark the first time Apple has attempted to compete in terms of price in some time for the desktop computer market.
The Third Biggest Event relating to Apple in 2014
The high-end iMac with the 5K display puts Apple ahead of its Windows competitors, such as Dell and Lenovo. If you want to do high resolution photography or CAD, this is your option.

Now for a few quickly selections from the Editor
This app doesn’t have the sexiest user interface, but it does solve the problem of “HELP! I’ve got old files that I need to read and save in a modern format!” In particular, it solves the problem of what to do with old ClarisWorks/AppleWorks word processing and spreadsheet files.
If you’ve got old WordPerfect files, this is the program that can open them. Lotus 1-2-3? This is it. Database files in .dbf format? This is it. About the only old format it doesn’t open is Wordstar 3.3
This is a perfectly good word-processing/spreadsheet/presentation/database office suite. For a $5 or $10 donation, it doesn’t get much better than this.
This software project has gone from a freebie that no one could figure out how to set up, to a $10 program that works very well. If you need to knit together disparate systems, from OS X 10.6 on up with Fedora Linux and Windows 8 so that they only use one keyboard and pointing device on your physical desktop, this is your answer.
Between Windows and OS X, you can even drag files from one screen to another. You share a clipboard between Windows, OS X, and Linux so you can copy and paste text and pictures between platforms.
You don’t have to fiddle with the terminal, not even in Linux.
In Conclusion
Apple is in a very strong position financially and possibly could become the first company valued at a trillion dollars. The whole world waits to see what the Apple Watch will bring. Rumors persist that Apple will bring out a 12” iPad Pro “next year”. So we’ll see what happens.
Tom Briant
Editor, MacValley Blog
Saturday, December 27, 2014
Senior Correspondent Arnold Woodworth's Year-End Wrap-up
2014: The year Apple got me to dump Android
Android is a great mobile platform, I've been using it since the very first phone appeared a few years ago.
If that's the case, then why drop it? For me the answer is simple. The evolution of iOS has been just as significant and it fits my wants and needs better than Android now.
On Android the distinction between smartphone and tablet use has always been clear.
The iPhone 6 Plus and iPad Air I own work the same in the ways that matter, and I can use the same apps on both.
This is so significant it can't be overstated
On Android I often had to stop and think about which device I was using and thus which app to use for a given task. Then I had to figure out the app interface for either the Android phone or tablet. The two devices were never running the same version of the OS, and often the OEM had customized the operation in a different way on the phone and tablet. Far too often this caused the UI to be different, even on the same app.
http://www.zdnet.com/article/2014-the-year-apple-got-me-to-dump-android/
What Impressed Me Most About The iPhone 6 Plus Is Something Nobody Really Talks About
The speakers on the iPhone 6 Plus are incredibly loud, clear, and vibrant.
with the iPhone 6 Plus, you don't get that shallow, tinny sound I've experienced with other phones.
http://www.businessinsider.com/iphone-6-plus-sound-quality-review-2014-12
10 things Apple won't say
http://www.marketwatch.com/story/10-things-apple-wont-say-2014-09-09
The $3 Million iPhone: How Technology Has Raised Our Standard Of Living
We've heard a lot about income inequality and the end of the middle class in the last couple of years.
There's no questioning the math. You can pick from almost any chart you like, but I'll take one that Business Insider has used many times: wages as a percentage of GDP.
a lot of us are carrying, in our pocket, a computer that would have been unspeakably costly in 1991.
http://www.businessinsider.com/technology-the-great-equalizer-2014-12
Here's Why You Should Never Let Your Kids Play With Your Smartphone
http://www.businessinsider.com/parents-giving-children-smartphones-2014-12
BlackBerry Is Working With Boeing On A Phone That Self-destructs
The Boeing Black device encrypts calls and is aimed at government agencies and others that need to keep communications and data secure.
http://www.businessinsider.com/r-blackberry-works-with-boeing-on-phone-that-self-destructs-2014-12
Google unveils 'fully functional' driverless car
http://www.marketwatch.com/story/google-unveils-fully-functional-driverless-car-2014-12-22
How Social Media Is Changing Our Brains And Reshaping Our Relationships
Daniel Siegel says:
The right hemisphere of the brain is used more for nonverbal communications (gestures, expressions, etc.) during face-to-face contact.
The left hemisphere of the brain is used more for verbal communications, including text and "social media".
"There's nothing inherently wrong with social media. But if it is replacing time for face-to-face, then that could be a big problem."
http://www.businessinsider.com/social-media-impact-brain-relationships-siegel-2014-12
The US Navy Tweeted An Intense Holiday Card
http://www.businessinsider.com/the-us-navy-tweeted-an-intense-holiday-card-2014-12
The Webcam Hacking Epidemic
Remote Access Tools (RAT) are software that allow a third party to spy on a computer user from afar, whether rifling through messages and browsing activity, photographing the computer screen, or in many cases hijacking the webcam and taking photographs of whomever is on the other side.
There's a real threat of being watched and recorded where you live, and without your knowledge or consent.
At web sites like HackForums.net, individuals, often men, trade and sell access to strangers' computers, often women, gained via RAT.
The National Security Agency, too, is involved. The agency has budgeted tens of millions of dollars for an aggressive effort to scale its hacking operations and "own the net," a proposition that, as The Intercept reported, envisions indiscriminately infecting millions with malware that has the capability for remote video surveillance by webcam.
http://www.theatlantic.com/technology/archive/2014/12/the-webcam-hacking-epidemic/383998/
Why Hacker Gang 'Lizard Squad' Took Down Xbox Live And PlayStation Network
http://www.businessinsider.com/why-hacker-gang-lizard-squad-took-down-xbox-live-and-playstation-network-2014-12
‘Lizard Squad,’ The Hacker Gang That Shut Down PlayStation Network And Xbox Live For 2 Straight Days, Is Now Reportedly Attacking Tor
http://www.businessinsider.com/report-lizard-squad-attacking-tor-2014-12
Anonymous To 'Lizard Squad': Stop Attacking Tor
http://www.businessinsider.com/anonymous-to-lizard-squad-stop-attacking-tor-2014-12
Hacker Gang 'Lizard Squad' Says It Has Stopped Attacking PlayStation Network And Xbox Live — And Will Never Do It Again
http://www.businessinsider.com/lizard-squad-has-stopped-attacking-playstation-network-and-xbox-live-2014-12
A Hacker Group Has Shared 13,000 Passwords To Sites Like Amazon, Walmart
http://www.businessinsider.com/hackers-released-13000-passwords-2014-12
Forget the Sony Hack, This Could Be the Biggest Cyber Attack of 2015
http://www.defenseone.com/technology/2014/12/forget-sony-hack-could-be-he-biggest-cyber-attack-2015/101727/
Sony to show 'The Interview' in theaters
plans to show once-canceled movie in limited release
The cancellation provoked considerable backlash among actors, directors and screenwriters.
http://www.marketwatch.com/story/sony-to-show-the-interview-in-theaters-2014-12-23
Sony's 'The Interview' grosses $1 million in ticket sales from 331 theaters on Christmas Day.
"The Interview" was originally intended as a broad, wide-release Hollywood comedy set for more than 3,000 screens. But the studio on Dec. 17 scuttled those plans after hackers threatened violence against movie theaters and most exhibitors declined to screen the film.
Some theaters across the country hosted sold-out showings as many moviegoers trekked to the cinemas out of a sense of patriotism and support for free speech after the movie's rocky ride to its release date, while some went mostly for the comedy.
http://www.latimes.com/entertainment/envelope/cotown/la-et-ct-box-office-interview-christmas-20141226-story.html
How A Cisco Exec Vanquished An Internet Troll And Saved 25 People
Web sites authored by anonymous trolls who make libelous accusations against innocent people are very hard to get shut down.
Surya Panditi managed to get 24 such sites shut down.
But the article doesn't say how.
http://www.businessinsider.com/a-cisco-exec-vanquished-internet-troll-2014-12
Friday, December 26, 2014
Set Up and Get to Know Your New Mac
The link below will take you to LifeHacker’s guides to setting up your Mac and adding new stuff to it.
Happy Holidays, from Halloween through Lunar New Year, y’all.
Tom Briant
Editor, MacValley Blog
Set Up and Get to Know Your New Mac: ""
(Via.)
Thursday, December 25, 2014
I need the administrative password for this Mac I bought on eBay! What do I do now?
Good Morning! I hope you enjoy this bright, if windy, Christmas morning here in Los Angeles. I don’t know if you received a shiny new Mac still in the shrink wrap this morning, or whether you received a used Mac purchased on eBay that has some of the previous user’s stickers on the lid.
This is my guide to a situation you may encounter the first week of ownership.
So you got a used Mac. It came with lots of neat software already installed, but the previous owner didn’t tell you what the administrative password is. If the machine runs 10.6, 10.5, or 10.4; I’ll bet they didn’t include the install DVDs, either.
You’ll need the administrative password to install software such as printer drivers and run utility software.
So what do you do? Fortunately, this situation has occurred before and people have documented the steps necessary to remedy it.
You have two choices. The hard one allows you to change the password set up by the original user. It takes a bit more UNIX voodoo than the second method. If you want to use it, go here to MacYourself.
The second method still takes some UNIX voodoo, but the command lines are shorter.
Here’s the recipe for method #2:
Make sure you’re in a calm frame of mind. You’re working at the root level of your Mac and you can trash the whole thing if you feel upset.
Turn off the Mac by pressing the Power button.
Count to 10.
Read this before proceeding: You’re going to restart your Mac by pressing the Power button.
As soon as you hear the “bong” of the start-up chime, hold down the Command and S keys simultaneously. Your screen will turn black and a lot of white text will scroll down the screen. This is normal. You’re in Single User mode.
At the prompt, you will want to type in the command so that you can modify files. In 10.6, Apple is kind enough to give it to you as a on-screen hint.
The command is /sbin/mount -uw /
Note the space between “mount” and “-uw” Note the space between -uw and the final trailing slash!
Press the Enter key. You should return to the prompt.
Now here’s the secret sauce. You want to trick your Mac into setting up a new administrative account where you can change the administrative passwords of the other accounts.
Type this command rm /var/db/.AppleSetupDone
Now press Enter.
If it didn’t work, note this: The rm is the command followed by the things you want to modify. In this case, you’re deleting the file that tells your Mac on bootup that you’ve gone through the initial setup. Your Mac will go through the initial setup all over again.
Now you won’t erase the files on your computer, but the Keychain login for the old account will be destroyed.
Now did you include the “.” before AppleSetupDone? Did you type AppleSetupDone in exactly that way, using capital letters where required? UNIX is picky about capitalization! Did you put a space between “rm” and “/var/db/.AppleSetupDone” ?
When you’ve run that command, now type reboot and your Mac will restart to begin the setup process.
Go through the setup process and set up a new administrative account by default. Write down the password to this account!
Now for the graphical portion.
Now that you’ve got access to your Mac through the new administrative account, you want to change the password on the previous user’s account.
Go to System Preferences. You want the Users or Accounts preference relating to administrative matters.
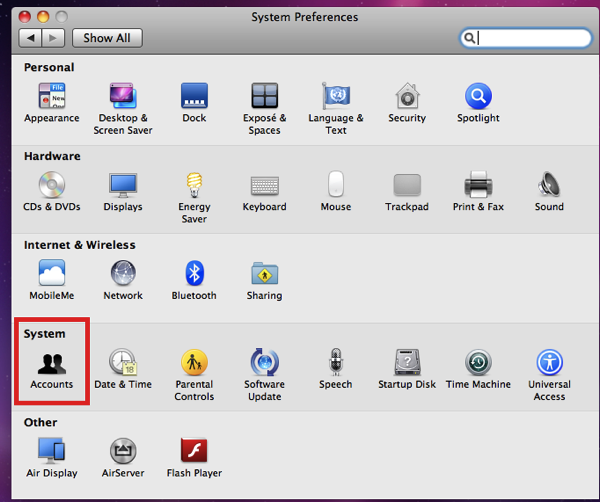
Now in Accounts, you go to your new Account. You will notice that it’s the only one not dimmed. To work on the other accounts, you need to click on the little lock icon in the lower left-hand corner and enter your password for this account (You did write it down, didn’t you?)
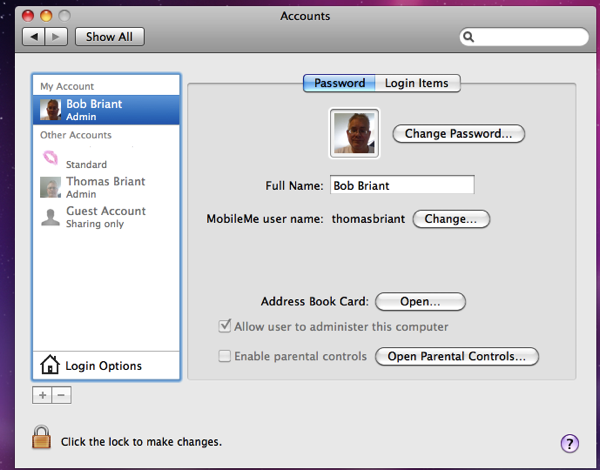
Now that you’ve entered your user password, you can access the other accounts.
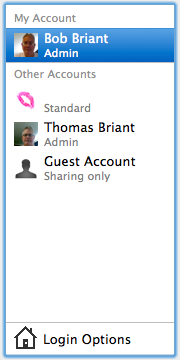
So click on the account whose password you want to change. You will see the following screen:
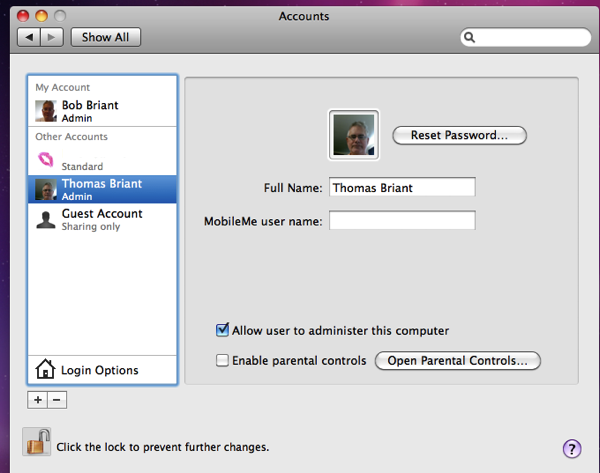
Click on the “Reset Password” button to change the password. You will see the following screen:
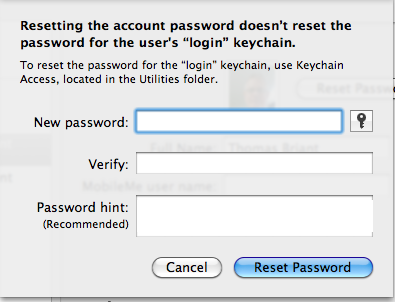
Now notice the box with the key icon in it immediately to the right of “New Password” That is Apple’s Password Assistant, which can offer you tips on a secure password
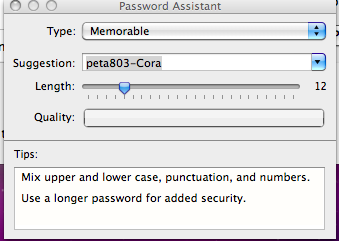
You will now need to log out of this session as the new user and log back in as the old user with the new password you assigned.
You can keep the new administrative account or get rid of it. It’s your choice.
Conclusion
None of what I’ve written above is original. These techniques have been on the Web for some time. I would like to thank Ant & Franky P. of Macyourself.com. I would like to thank those at StackExchange.com who gave me the tip on tricking your Mac into setting up a new administrative account from scratch.
I did test the tips out myself on my 2006 CoreDuo 10.6 MacBook. They worked perfectly.
Tom Briant
Editor, MacValley Blog
Sunday, December 21, 2014
Senior Correspondent Arnold Woodworth's Weekly Web Roundup
10 Secret Features Hidden In Your Mac
http://www.businessinsider.com/secret-mac-features-tips-and-tricks-2014-12
11 Tiny Design Features That Show Apple's Insane Attention To Detail
http://www.businessinsider.com.au/best-apple-design-details-that-show-apples-insane-attention-to-detail-2014-12#a-smart-fan-that-listens-1
20 iPad Apps That Will Make Your Android Friends Jealous
http://www.businessinsider.com/best-ipad-apps-not-on-android-2014-12
A note from analysts at Morgan Stanley estimates Apple could sell up to 70 million iPhones this quarter.
If the average selling price of the iPhone is $605, then that would be $42.3 billion in revenue.
http://www.businessinsider.com/iphone-sales-are-going-nuclear-2014-12
Apple Pay may be easy to use, but security is its biggest strength.
Unlike using a credit or debit card, Apple Pay doesn't show merchants your payment information when you buy something.
Instead, it uses a digital account number called a "token" to tell the merchant you're good for the purchase.
45% of Americans said they had received a letter from a retailer or cardholder saying their payment information had been leaked.
That's staggeringly high.
http://www.businessinsider.com/apple-pay-prevents-leaked-payment-info-from-retailers-2014-12
Here's What People Don't Get About Apple Pay: It's Not Just Changing Payments
Apple already has a way for merchants to push these offers: Passbook.
"The marketing is done through Passbook," said Philbin. "Apple Pay is just the payment functionality."
http://www.businessinsider.com/apple-pay-will-change-marketing-not-just-payments-2014-12
If Apple Were A Worker Cooperative, Each Employee Would Earn At Least $403K
http://www.forbes.com/sites/cameronkeng/2014/12/18/if-apple-was-a-worker-cooperative-each-employee-would-earn-at-least-403k/
Apple found not guilty in iPod antitrust lawsuit
Apple was found not guilty in an iPod antitrust case that was brought against it almost a decade ago. The decision comes after a week-long trial that accused the Cupertino company of forcefully locking in consumers into iTunes software and preventing them from using other services thanks to the now-defunct FairPlay DRM.
http://www.engadget.com/2014/12/16/apple-found-not-guilty-in-ipod-antitrust-lawsuit/
Here's How Much You Have To Buy To Make Amazon Prime Worth It
http://www.businessinsider.com/amazon-prime-is-it-worth-it-2014-12
This person wrote:
"I disagree with some in the Cloud Industry who say calling the storage devices you carry with you and your home storage a personal Cloud is wrong. But they don't want to call it outsourced storage. It's semantics. Key is it's sitting somewhere else out of your control. There are too many people out there who want to put another conquest notch on their hacking skills by tapping into big companies. There are things you can do every day to protect your stuff from evil doers even if you use their Cloud. Be a little paranoid combined with a big dose of common sense/diligence."
http://www.silentpcreview.com/Eliminate_User_and_Security_Breaches,_Hacks_Will_Be_Solved
Sony Pictures Entertainment said it would cancel the Christmas Day release of "The Interview," the subject of recent hack attacks and violent threats against the company and theater owners
http://www.marketwatch.com/story/sony-says-it-will-pull-the-interview-from-theaters-2014-12-17
FBI says 90% Of Cyber Security Systems Out There Would ***NOT*** Have Been Able To Block The Sony Hackers
http://www.businessinsider.com/fbi-90-of-cyber-security-systems-out-there-would-not-have-been-able-to-block-the-sony-hackers-2014-12
How The Hackers Broke Into Sony And Why It Could Happen To Any Company
http://www.businessinsider.com/how-the-hackers-broke-into-sony-2014-12
5 ways the Sony hack will change how America does business
http://www.marketwatch.com/story/5-ways-the-sony-hack-attack-will-change-cybersecurity-2014-12-19
Here's How Cyber-Warfare Started And Where It's Going
In 2007 a computer worm called Stuxnet was detected for the first time by virus-scanning software
At least three more versions followed, seeking to wreak havoc upon Iran's uranium-enrichment facility
Despite the opportunity, the world has yet to see a sequel to Stuxnet.
A cyberwarrior needs only a computer and an internet connection to wreak havoc.
http://www.businessinsider.com/future-of-cyber-warfare-2014-12
Wednesday, December 17, 2014
How to be your family's tech-support hero during the holidays | PCWorld
How to be your family's tech-support hero during the holidays | PCWorld: ""
(Via.)
If you’re going out to see relatives and they’re tech-challenged, read this article and see this video. Gordon’s portrayal of the stereotypical drunk uncle is priceless, too.
Tom Briant
The Computer Uncle and Editor, MacValley Blog
Tuesday, December 16, 2014
Senior Correspondent Arnold Woodworth's Weekly Roundup from the Web
The Best iPad Apps Of The Year, According To Apple
http://www.businessinsider.com/best-ipad-apps-of-the-year-according-to-apple-2014-2014-12
How to download Apple’s iWork apps on older Macs for free
http://www.cultofmac.com/306118/download-apples-iwork-apps-older-macs-free/
Diehard Microsoft fans abandon Windows Phone for iPhone
http://www.cultofmac.com/306051/diehard-microsoft-fans-abandon-windows-phone-iphone/
Apple and IBM Just Showed Everyone The Future Of Enterprise Mobile Apps
http://www.forbes.com/sites/maribellopez/2014/12/10/apple-and-ibm-showcase-a-bold-new-enterprise-mobile-app-frontier/
How to turn Apple’s best keyboard into a fully-functional PC
Important note: Apple's best keyboard is a relatively old model.
http://www.cultofmac.com/306106/turn-apples-best-keyboard-fully-functional-pc/
7 Reasons Why You Should Buy An Android Phone Over An iPhone
Android has more hardware options, but do you really need them?
http://www.businessinsider.com/should-you-buy-an-android-phone-2014-12
Apple ends its arguments in the DRM trial, but it’s far from over
The entire complaint hinges on exactly why Apple hardened its digital rights management software in iTunes and iPods nearly a decade ago.
Earlier in the trial, Apple had argued that such third-party players, including one made by RealNetworks, attempted to hijack the iPod and created all sorts of issues for users that would damage a user's music library and the performance of their iPod. That's become a point of contention where Apple's said it was trying to protect users from buggy software, while the plaintiffs have accused it of shutting out competition.
http://www.theverge.com/2014/12/12/7385577/Apple-DRM-trial-far-from-over
Apple’s Ridiculous Censorship of the Nudity in a game called "Papers, Please"
http://www.wired.com/2014/12/papers-please-ios-censored/
I Asked Jeff Bezos About The Tough Questions — No Profits, The Book Controversies, The Phone Flop — And He Showed Why Amazon Is Such A Huge Success
On his FirePhone failure:
Experiments are, by their very nature, prone to failure. A few big successes compensate for dozens and dozens of things that didn’t work.
companies that are making bets all along, even big bets, but not bet-the-company bets, prevail.
On investor relations:
We meet with investors who have low portfolio turnover. Many investment funds have very high portfolio turnover. They’re not really investors — they’re traders.
On when Amazon will deliver regularly with drones:
That’s a difficult question to answer. Technology is not going to be the long pole. The long pole is going to be regulatory.
On Outer Space:
We need the frontier. We need the people moving out into space.
http://www.businessinsider.com/amazons-jeff-bezos-on-profits-failure-succession-big-bets-2014-12
Friday, December 12, 2014
Sunday, December 7, 2014
Senior Correspondent Arnold Woodworth's Weekly Web Roundup
7-year-old boy cleverly thwarts Apple's iPhone security measures
He quietly reached for his father's iPhone, grabbed his right hand and pressed his large thumb onto the fingerprint scanner.
http://www.tuaw.com/2014/12/02/7-year-old-boy-cleverly-thwarts-apples-iphone-security-measures/
The Best Smartphones In The World
iPhone 6 and iPhone 6+ are (again) first and second.
http://www.businessinsider.com/best-smartphones-2014-12
Months after Apple launched its much-hyped iPhone 6 and iPhone 6 Plus, the company remains unable to meet the huge demand from consumers.
Lots of speculation about why in this article.
The reader comments to this article contain better speculations than those of the pundits quoted in the article.
http://www.cnbc.com/id/102213174
The complete history of Mac OS X gets broken down in one brilliant illustrated guide
Want to see how OS X has evolved over the years? If so then you should check out this complete guide posted over at Git-Tower
http://bgr.com/2014/12/05/apple-mac-os-x-history/
http://www.git-tower.com/blog/history-of-osx/
A Life-Changing App That Every iPhone 6 Owner Should Download
One of the best things about the new iPhone is that it comes with a step tracker built in ...... track how much you walk in a day.
But, even better is Pedometer++, a super simple application that tracks steps. It also tracks elevation changes, providing a look at how many flights of stairs you've climbed in the day.
Every single person who owns an iPhone 5S, 6, or 6 Plus should download Pedometer++. It's free. If you like it, and you want to be generous, you can "tip" the developer $0.99, $2.99, or $5.99 through an in-app payment.
http://www.businessinsider.com/best-step-counting-app-pedometer-2014-12
Apple Retailers Teaching Free 'Hour of Code'
In celebration of Computer Science Education Week, Apple and Code.org will again present Hour of Code workshops across the United States.
The nonprofit said it is joining forces with Cupertino to encourage folks of all ages to learn the basics of computer programming. It's the second year that the Code.org and Apple have hosted such workshops.
http://www.pcmag.com/article2/0,2817,2473171,00.asp
The Best Programming Languages Every Beginner Should Learn
http://www.businessinsider.com/best-programming-languages-2014-12
Woz Shoots Down 'Myth' of Apple's Garage Origins
http://www.pcmag.com/article2/0,2817,2473137,00.asp
Apple removes sexually-explicit 'After School' app
Its removal comes after Apple representatives were in "direct contact" Wednesday evening with Tom McCurdy, Pinckney Community School's assistant superintendent for curriculum, assessment and technology.
http://www.livingstondaily.com/story/news/education/livingston-county/2014/12/04/after-school-app-removed/19906429/
Feds dig up law from 1789 to demand Apple, Google decrypt smartphones
The FBI has made it no secret that it hates Apple and Google's efforts to encrypt files in your smartphones and tablets.
Now court documents have emerged showing just how far the Feds are willing to go to decrypt citizens' data.
It's an interesting legal tactic, but the Feds may find out the hard way that the All Writs Act has its limitation. The argument used by Apple and Google over encryption is that, even if they wanted to help the Feds, they can't do anything about it – because modern iOS and Android encrypts data in a way that only the owner can decrypt.
http://www.theregister.co.uk/2014/12/01/feds_turn_to_1789_law_to_force_smartphone_makers_to_decrypt_handsets/
In both cases, the seized phones—one of which is an iPhone 5S—are encrypted and cannot be cracked by federal authorities. Prosecutors have now invoked the All Writs Act, an 18th-century federal law that simply allows courts to issue a writ, or order, which compels a person or company to do something.
http://arstechnica.com/tech-policy/2014/12/feds-want-apples-help-to-defeat-encrypted-phones-new-legal-case-shows/
ACLU attorney Alex Abdo, in comments to Ars Technica, argued that the government should not be using an 18th century law to address a technological issue that could not possibly have been imagined by those who penned it.
http://benswann.com/prosecutors-say-1789-george-washington-law-requires-google-apple-to-decrypt-smartphones-for-cops/
Why You NEED Unbreakable Encryption
http://www.market-ticker.org/akcs-www?post=229638
How to invest in the Social Communications Revolution
The endgame is total empowerment of the end user.
social communications platforms are creating a more prosperous future with more freedom for all of us.
All forces can be used for good or evil, and over the last decade, with the incessant snooping and spying from the NSA and other long-existing divisions from what I call the Republican/Democrat regime, we’ve already seen much of the downside of social networking gone mainstream.
This concept we’re hitting on can also be called, “Virtuous Entropy.” The whole point is that it isn’t centralized or controlled in any way, but at the same time, that chaos is natural and outright prosperous.
I’m excited about a more prosperous future with more freedom for all. Aren’t you?
http://blogs.marketwatch.com/cody/2014/11/24/why-facebook-remains-the-best-play-in-social/
Why Google Glass and Apple Watch matter so much
wearables are going to be so much bigger than anybody realizes. What you see and consider a wearable computer today isn’t what the Wearables Revolution is all about.
Google Glass isn’t just about the thing you wear on your head. It’s about a new way of interacting with the web using your voice and gestures.
...as the technology/concept of low-interactivity interfaces become ever easier to use...
Likewise for Apple’s upcoming Apple Watch.
the Apple Watch requires a smartphone hub for you to tie into and for heavy interfacing. But for quick interaction with the Web and for the things you use your smartphone everyday for, the new less-intensive interface is much more important.
I’m sticking with Google and Apple in part because they’re about to create the platforms upon which the Wearables Revolution will arise.
http://blogs.marketwatch.com/cody/2014/12/01/why-google-glass-and-apple-watch-matter-so-much/
40% Of LinkedIn Users Earn More Than $100,000 A Year
http://www.businessinsider.com/linkedin-user-wealth-2014-12
5 privacy fixes your Facebook News Feed needs by New Year's
http://www.macworld.com/article/2855596/5-privacy-fixes-your-facebook-news-feed-needs-by-new-year-s.html
Experts Are Divided On Stephen Hawking's Claim That Artificial Intelligence Could End Humanity
http://www.businessinsider.com/afp-artificial-intelligence-hawkings-fears-stir-debate-2014-12
Peer-to-peer loans imperil banks, and cryptocurrencies may finish the job
Wall Street's greatest threat isn't from regulation or another meltdown - it's from technology. So-called cryptocurrencies, including the best known one, bitcoin, will eventually dislodge the power banks, brokerages and other financial institutions have over the system.
There's just one problem: It isn't going to happen anytime soon. This stuff is not ready for prime time.
cryptocurrencies may be the biggest end-game threat, but not the biggest immediate threat. That distinction goes to a new breed of banking that isn't really technology focused at all. It's called peer-to-peer lending. Simply put, it's a platform where people who want to invest money lend it to people who want to borrow.
http://www.marketwatch.com/story/this-bitcoin-alternative-is-a-threat-to-wall-street-2014-12-04
Sony staffers received a new email from hackers Friday, this time threatening their families, from the group who calls itself the Guardians of Peace or the "GOP."
http://www.usatoday.com/story/life/movies/2014/12/05/sony-hacked-again-this-time-employee-families-threatened/19970141/
Hacking Experts Call Sony Cyber Attack ‘Unparalleled And Well Planned Crime’
http://www.businessinsider.com/hacking-experts-call-sony-cyber-attack-unparalleled-and-well-planned-crime-2014-12
Friday, December 5, 2014
Thoughts from an old man on kids learning how to code
I note that Apple will offer children an Hour of Code on December 11th. I have some thoughts on this whole push to expose kids to some computer program coding.
First, I think in principle it’s a great idea. All of us in any size, sex, gender, age and computer proclivity in general have to deal with a lot of code in our lives as it is. From ATMs to Spotify to our damn cars, code is everywhere and we all should have some understanding of it.
To quote a very smart person, Arthur C. Clarke, “Any form of science sufficiently advanced is indistinguishable from magic.”
So before we think it’s a bunch of nerds reciting spells, ala Harry Potter, we should all gain some exposure to coding. It’s a process of writing code, testing it, and seeing where it failed. Then you go back and try it again.
To quote another person, Thomas Edison, “It’s 1% inspiration and 99% perspiration.”
But it would help a lot of people if they could understand loops and if/then/else statements.
Second, no matter what your mother thinks, it’s very unlikely that you will write the next version of Windows or Office. What’s more important is that you know how to write a macro for Office so that you or your boss don’t have to keep doing the same thing over and over again. For instance, learn how to use the mail merge feature in Word. That will introduce you to variables.
I went to school to learn programming. The most involved programming I ever did professionally was to rewrite printer drivers in BASIC-80 so that the client’s printed checks and invoices looked acceptable. But I needed to understand a lot of principles in order to do that.
So, by all means, learn how to code a simple program as a start.
Third, I would also suggest that if we teach girls to code, we should teach them the basics of accounting. Accounting and coding go way back together. Take an extension course in the basics of accounting. Seriously, you should know what an asset, liability, and owner’s equity are. You should know the difference between a balance sheet and an income statement. Don’t become the person on the sweat shirt: “How can I be out of money when I have all these checks left?”
Tom Briant, age 59
Editor MacValley Blog
Sunday, November 30, 2014
Holiday Eating Tips from the Editor's Cousin Judy
Holiday Eating Tips:
1. Avoid carrot sticks. Anyone who puts carrots on a holiday buffet knows nothing of the Christmas spirit. In fact, if you see carrots, leave immediately. Go next door, where they’re serving rum balls.
2. Drink as much eggnog as you can. And quickly. Like fine single-malt Scotch. In fact, it’s even rarer than single-malt Scotch. You can’t find it any other time of the year but now. So drink up! Who cares if it has 10,000 calories in every sips. It’s not as if you’re going to turn into an eggnog-aholic or something. It’s a treat. Enjoy it. Have one for me. Have two. It’s later than you think. It’s Christmas.
3. If something comes with gravy, use it. That’s the whole point of gravy. Gravy does not stand alone. Pour it on. Make a volcano out of your mashed potatoes. Fill it with gravy. Eat the volcano. Repeat.
4. As for mashed potatoes, always ask if they’re made with skim milk or whole milk. If it’s skim, pass. Why bother? It’s like buying a sports car with an automatic transmission.
5. Do not have a snack before going to a party in a effort to control your eating. The whole point of going to a Christmas party is to eat other people’s food for free. Lots of it. Hello?
6. Under no circumstances should you exercise between now and New Year’s. You can do that in January when you have nothing else to do. This is the time for long naps, which you’ll need after circling the buffet table while carrying a 10-pound plate of food and that vat of eggnog.
7. If you come across something really good at a buffet table, like frosted Christmas cookies in the shape and size of Santa, position yourself near them and don’t budge. Have as many as you can before becoming the center of attention. They’re like a beautiful pair of shoes. If you leave them behind, you’re never going to see them again.
8. Same for pies. Apple. Pumpkin. Mincemeat. Have a slice of each. Or, if you don’t like mincemeat, have two apples and one pumpkin. Always have three. When else do you get to have more than one dessert? Labor Day?
9. Did someone mention fruitcake? Granted, it’s loaded with the mandatory celebratory calories, but avoid it at all cost. I mean, have some standards.
10 One final tip: If you don’t feel terrible when you leave the party or get up from the table, you haven’t been paying attention. Reread tips; start over, but hurry. January is just around the corner.
Remember this motto to live by: Life should NOT be a journey to the grave with the intention of arriving safely in an attractive and well preserved body; but to skid in sideways, chocolate in one hand, martini in the other, body throughly sued up, totally worn out and screaming:
WOO HOO! WHAT A RIDE!
Tom Briant
Editor, MacValley Blog
P.S. If you got a good laugh out of this, but have some ideas for variations based on your religion or culture, please! Submit them to me and I’ll post them. For Goodness sake, let’s party together this time of year.
Saturday, November 29, 2014
Holy vintage vehicles! Earliest known official Batmobile goes on sale • The Register
Holy vintage vehicles! Earliest known official Batmobile goes on sale • The Register: ""
(Via.)
You’ve gotta see the picture of this thing. Now will it pass smog inspection here in California?
Tom Briant
Editor, MacValley Blog
Thursday, November 27, 2014
The Return of Forked-Daapd! New and Improved! Thank you, Julien Blache
The Return of Forked-Daapd (Thank you, Julien Blache)
As a nerd in his shorts in his tiny condo in Canoga Park, CA; I have experimented with Linux and various iTunes music server apps. I have written about two music server Linux apps in the past, forked-daapd and Tangerine.
The old version of forked-daapd (0.19) stopped working with iTunes after 15 minutes. The new version of forked-daapd, though, continues to work. To get it, though, you need to install Ubuntu Linux 14.10 “Utopic Unicorn”. This is the latest version with the latest apps.
To install forked-daapd ver 0.2x, you will need to use the Terminal, so roll up your sleeves and get ready. I will guide you through the steps.
To get Ubuntu 14.10, you go to Ubuntu. Com and download the .iso disk image. It’s about 1.16 Gb in size. You will need to burn it to a DVD, not a CD.
I do a lot of playing with Linux, so I have learned to use DVD-RW disks. When I burn a new DVD with a new version of Linux to install, OS X’s disk utility erases the old file to clear the way for the new one. So if you intend to play with Linux, get a package of DVD-RW disks to save yourself from a desk overrun with “coasters”.
To burn a Linux disk in OS X, open Disk Utility which you will find in your /Applications/Utility folder.
Now press the Command key + B. This opens a File Dialog box for you to select the image file you want to burn to that DVD. (Figure 1)
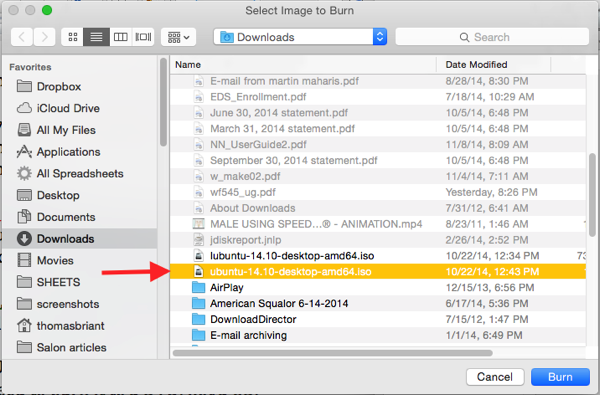
Having selected the file you want to burn, insert the blank or erasable DVD into the burner. Follow the on-screen prompts and you’ll have an install DVD in 10 minutes.
Now you will need a DVD burner, too; if you go this route and install via a DVD. You could use a USB flash drive as an alternative means of installation. The Ubuntu site has instructions on installing the disk image on a USB flash drive. That’s your extra-credit assignment!
The Ubuntu Linux install procedure will remind you of installing OS X from a disk, if you go that far back. You can select which hard drive you want to install to, set up your language, keyboard, and time zone preferences. You set up your user name, your password, and the name of your computer. Then you sit back as Ubuntu presents a slide show as installation goes on, showing the benefits of Linux.
At the end, you reboot the machine, remove the DVD, and press the ENTER key. You should start up in Linux or go to the GRUB menu which lets you choose between the various systems installed on your computer. On my test rig, I have four hard drives (!), each with a different operating system. See Windows Hints at the end if you have trouble with a dual-booting Windows/Linux system.
So you’ve installed Ubuntu Linux 14.10 on a PC. Now what?
You will want to install the updates as your first thing. You will see a blinking/bouncing icon asking for your attention. Install the updates.
Now you want to install several pieces of software from the Terminal’s command line. This may look like Linux voodoo, but I will explain it to you.
You first want to install netatalk, which allows you to connect your Linux machine to your Mac using the Apple File Protocol (AFP).
Open the Terminal by pressing Control+Alt+T. The Linux Terminal comes up, looking a lot like the OS X Terminal. Well, they are cousins with their roots in UNIX.
Enter the following command into the Terminal sudo apt-get install netatalk
Enter your password when requested. You won’t see it on the screen, but press ENTER when you’re done.
Follow the prompts pressing Y when asked to.
Here’s how it breaks down. sudo makes you a temporary superuser with root privileges
Apt-get is the command-line utility for installing programs. It comes from the Debian version of Linux. Ubuntu and many other distros of Linux descend from Debian.
Install tells apt-get that you want to install the following program.
Netatalk is the program you want to install. It comes from a Ubuntu repository. Think of it as the command-line equivalent of Apple’s Mac App Store, only predating it by several years.
Once the installation finishes and you return to the command prompt, you need to edit netatalk configuration file. To do that, enter this command:
Sudo nano /etc/netatalk/atalkd.conf
Again, sudo makes you a temporary superuser. You’ll need to enter your password to gain temporary privileges.
nano is the Terminal-based editor. It’s simple to use, compared to Vim and Emacs, other Terminal-based editors of much great complexity.
/etc/netatalk/atalkd.conf is the path to the atalkd.conf configuration file.
You only need to add the phrase eth0 to the bottom of the configuration file. That’s a Zero at the end of the eth, not an o.
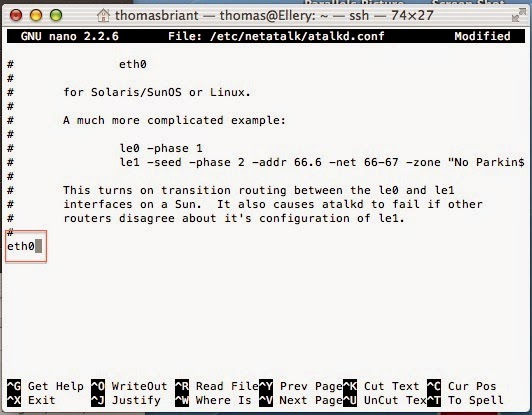
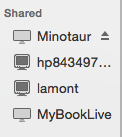
Now look in your Finder. If you connected the Linux computer to your LAN, you should see its computer name appear in the Finder’s sidebar under the Shared devices
In this picture, the shared device is Minotaur. For those of you paying attention, I recycled a picture above showing a Linux machine called Ellery.
Installing and Configuration of forked-daapd
The installation of forked-daapd is easy. You enter this command into the Terminal:
Sudo apt-get install forked-daapd
Enter your password when requested. You’ll see a lot of text scroll by. When asked for your permission, type “y”.
Now for the configuration of forked-daapd. I have read too many articles that gloss over this portion. It is not as easy as the proverbial pie and I will show you the pitfalls.
First off, you have to edit another configuration file, /etc/forked-daapd.conf
You can use the simple nano editor for this.
This is the part of forked-daapd.conf that you need to edit initially.
# Library configuration
library {
# Name of the library as displayed by the clients
# %h: hostname, %v: version
name = "My Mighty Minotaur Music on %h"
# TCP port to listen on. Default port is 3689 (daap)
port = 3689
# Password for the library. Optional.
#password = ""
# Directories to index
directories = { "/home/thomas/Music" }
First off, the name of the libray displayed to clients.
By default, it’s name= “My Music on %h”
I just changed it to “My Mighty Minotaur Music on %h” The “%h” refers to the name of the computer, which in this case is Minotaur.
Now the line read “# Directories to index” This is the path to the directories with the music you want to serve up. This is the line in the configuration line that will drive you nuts if you’re not careful.
As you can see, I have entered “/home/thomas/Music” Notice that some words come in lower-case and the last word comes capitalized. Pay Attention, as Linux is case-sensitive unlike OS X.
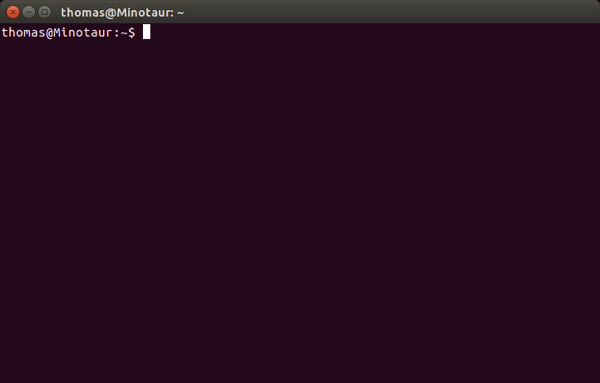
I’m going to show you how to find that path with the correct capitalization without wasting time.
First, open your Terminal with Control+Alt+T You will open to a prompt that should display your user name and the name of the computer. In my case, it’s “thomas@Minotaur”
Now enter the command ls (list) and press the ENTER key. You won’t need to enter your password.
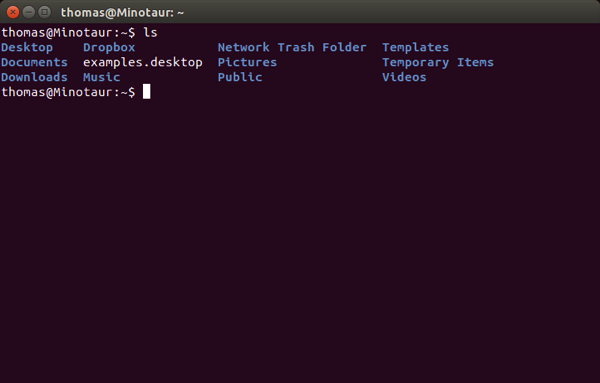
You should see a listing of the directories within your Home directory. One of these should be Music.
Now enter the command cd Music to move into the Music directory.
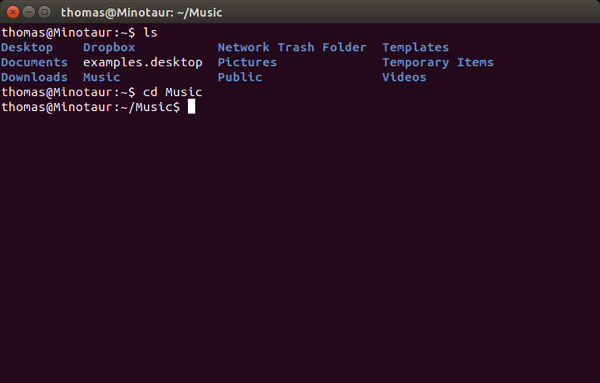
Now my command prompt displays “thomas@Minotaur:~/Music$” This means I am in the Music directory.
Now do ls again to see any directories that you have copied into Music. You should see any directories (folders) of music that you copied in.
Now for the million-dollar command. Enter pwd (print working directory) which gives you the path from the root to the directory you stored the music in. Press the ENTER key. Again, no password is needed.
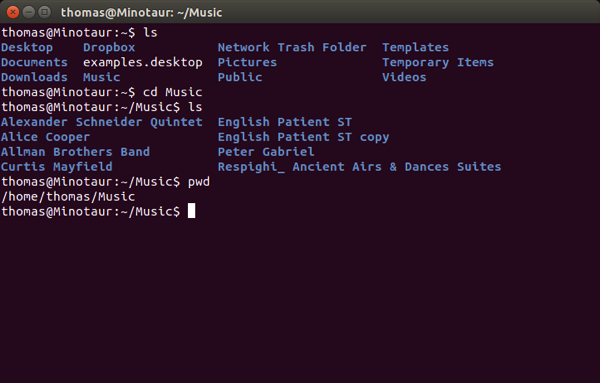
In my case, it’s “/home/thomas/Music” Note the spelling and especially any capitalized words. Yours should be different from mine.
Enter that exactly as the path in forked-daapd.conf
Starting and Stopping forked-daapd
Forked-daapd is a service that automatically starts up when you start up Linux. It will rescan and index the music you have placed in the directory you designated.
If you add or subtract music during a session, forked-daapd will NOT automatically rescan and index these changes. You have to manually stop and start the program.
To stop forked-daapd, open the Terminal and type
sudo /etc/init.d/forked-daapd stop
To restart a stopped session of forked-daapd, open the Terminal and type
sudo /etc/init.d/forked-daapd start
Each time you stop and start , you have to enter your password.
Hints for Windows users
If you use Windows and particularly if you dual boot with Linux, I have some tips for you.
First, Windows 7 & 8.1 include facilities for burning image files to CD or DVD. Right-click on the image file in the Windows Explorer. You will see an option for burning DVDs from image files.
Second, if you want to play with Linux on a dual-boot machine, you need to know about the Linux boot repair distro. This is a specialized Linux distro that will repair your GRUB boot menu. I recommend it you get it and burn several copies, in case you can’t find the first one. At that point, you’ve probably can’t boot into either Windows or Linux. Get it from here. It’s a Godsend for those of us who play with Linux.
Third, if you’ve copied music folders from your Windows user directory to the Linux music directory, you may find that they don’t appear in the music files forked-daapd lists on iTunes. This is a “WTF” moment.
Now the iTunes files I copied from my Mac worked fine. What’s the problem? The problem is pesky permissions.
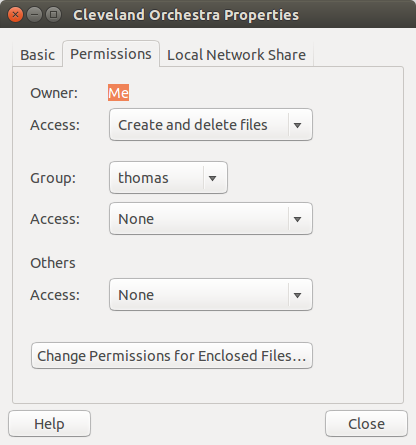
For example, I copied a folder of music from The Cleveland Orchestra from my Windows iTunes directory to my Linux Music directory. I stopped and started forked-daapd. What?! No Cleveland Orchestra?! What is the problem?
As I said, the problem lies with the file and folder permissions.
Here is a screenshot of The Cleveland Orchestra folder.
Here is a screenshot of the permissions for Alice Cooper’s Greatest Hits, which displays in iTunes from forked-daapd.
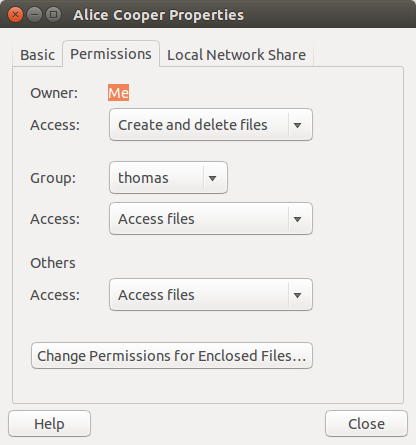
Note that the permissions for the Cleveland Orchestra for group and others do not allow access to files. With Alice Cooper’s Greatest Hits, group and others do have access to files.
So. Change the permissions for The Cleveland Orchestra to match those of the Alice Cooper’s folder. Click on the downward arrow at the right-hand side of Access.
Change the permissions within the folder, too. Click on that button
Click on Change and you’re done.
Now stop and restart forked-daapd and voila! The Cleveland Orchestra plays through forked-daapd on iTunes.
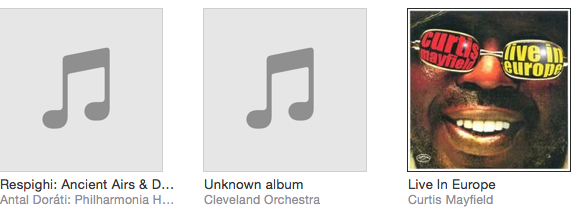
Conclusion
This article covered how to install and configure forked-daapd 0.2x. I would like to thank Julien Blache for his work in developing this app and also to everyone else who has worked on it over the years. Your work, ladies and gentlemen, is greatly appreciated.
Please see my earlier articles on forked-daapd and the Tangerine music server if you need more detail on a part I glossed over.
And last of all, but not least, a big, big vote of thanks to Arvid Srinivasan and his original Mac|Life article on building an OS X friendly Linux Music Server using an old Windows PC. I refer back to that article for many details. Thank you MacLIfe and Future Publications for allowing me to borrow from that article.
Today is Thanksgiving here in the United States, which begins the holiday season of feasting and celebrating. I’ll post a humorous article sent to me by my cousin Judy about how to conduct yourself.
Tom Briant
Editor, MacValley
Saturday, November 22, 2014
Senior Correspondent Arnold Woodworth's Weekly Web Roundup
Apple Releases iOS 8.1.1, It's An Essential Update
http://www.forbes.com/sites/gordonkelly/2014/11/18/ios-8-1-1-released/
Apple releases iOS 8.1.1 to improve performance on old products
Apple says the latest release should speed things up on iPad 2 and iPhone 4S, two of the company's aging devices.
Apple has released OS X 10.10.1, its first update to Yosemite.
http://www.theverge.com/2014/11/17/7235239/apple-ios-8-1-1-now-available-improves-performance-iphone-4s-ipad-2
iOS 8 vs Android 5.0 Lollipop Review: Material Difference
http://www.forbes.com/sites/gordonkelly/2014/11/07/ios-8-vs-android-5-0-lollipop-review/
Exclusive: The iPhone 6's A8 chip can play 4K video
Even though Apple hasn't announced it, the iPhone 6 and 6 Plus are ready to play 4K videos.
The discovery was made by the developers of WALTR, a great Mac app that allows users to quickly upload video files to their iPhone which aren't supported by iTunes.
http://www.tuaw.com/2014/11/21/exclusive-the-iphone-6s-a8-chip-can-play-4k-video/
Apple's A8 Chip In The iPhone 6 And iPhone 6 Plus Enables Support For 4K Video Playback
A device that has 4K support essentially means it has a horizontal resolution of approximately 4,000 pixels.
AW comment: That's getting very close to movie theater resolution.
http://www.forbes.com/sites/amitchowdhry/2014/11/22/apples-a8-chip-in-the-iphone-6-and-iphone-6-plus-supports-4k-video-playback/
According to a report on Friday, Apple's latest iPhone 6 and iPhone 6 Plus models are able to play back 4K video thanks to the powerful A8 system-on-chip, suggesting a future Apple TV model equipped with the same silicon would offer support for ultra high definition programming.
During testing of its media file conversion app WALTR, developer Softorino discovered Apple's A8 processor can play back 4K videos on the iPhone 6 and 6 Plus.
http://appleinsider.com/articles/14/11/21/apples-a8-soc-reportedly-capable-of-4k-video-output-may-pave-way-for-ultra-high-resolution-apple-tv
Reader comment: Now if only 4K TVs weren't so eye-wateringly expensive.
Constantly Staring At Your Phone Is Bad For The Spine, Says Study
Some doctors are already working with patients that have head, neck and back pain caused by “text neck.”
http://www.forbes.com/sites/amitchowdhry/2014/11/21/constantly-staring-at-your-phone-is-bad-for-the-spine-says-study/
DOJ: A child will die due to Apple's iOS 8 encryption tech
Apple General Counsel Bruce Sewell called the theoretical circumstance inflammatory and inaccurate, pointing out police have more tools at their disposal when it comes to gleaning information from mobile devices.
When asked why Apple can't create a backdoor to be used by law enforcement agents acting with proper court approval, Sewell said, "We can't create a key that only the good guys can use."
http://appleinsider.com/articles/14/11/19/doj-a-child-will-die-due-to-apples-ios-8-encryption-tech-
Encryption Again: Choose Wisely America
Note two things:
• The scaremongering using children, the typical way that the government shuts down anything reasoned debate.
• Not even a pretense that the desired change would prevent the death -- it would only be the post-hoc search of the phone that would be curtailed!
In a word, so what? If little Suzy is dead then we have a suspect and a body; the fact that there was a murder hasn't changed. That the police have to actually do their work the old-fashioned way doesn't change anything either, nor does access to someone's phone (or lack thereof) change DNA and other physical evidence.
Apple's executives apparently took this the same way I did, which is good. Credit where credit is due.
But pay attention folks, because there are some 330 million of us here and complying with the DOJ's demands will get a hell of lot more of us killed than just little Suzy!
http://www.market-ticker.org/akcs-www?post=229612
Apple-backed Rockstar ends patent war on Android, deal suggests
The news comes in part via a landmark court order in which a federal judge agrees to stay a series of lawsuits between Google and a patent consortium known asRockstar, that is primarily owned by Apple.
The Rockstar lawsuits threatened to further inflame a global patent battle over smartphones, and led Google to file a lawsuit of its own last Christmas in an attempt toshield phone makers.
Apple and the other Rockstar owners have apparently decided to defang Rockstar once and for all, instead of selling it to people who would operate it as a patent troll.
Some very interesting reader comments on this story.
https://gigaom.com/2014/11/20/apple-ends-patent-war-on-android-deal-suggests/
"I will spend my last dying breath if I need to, and I will spend every penny of Apple's $40 billion in the bank, to right this wrong. I'm going to destroy Android, because it's a stolen product. I'm willing to go thermonuclear war on this."
-- Steve Jobs
Apple has made a slight tweak to its App Store by replacing the "Free" button with the "Get" button. Here's Why.
Apple has been criticized by European regulators over the shady world of in-app purchases.
The EC believes that a free label might mislead a customer regarding the true cost involved with in-app purchases.
Apps on the iOS and Mac App Store will no longer have the "Free" label even if the apps do not have any in-app purchase option.
http://www.techtimes.com/articles/20699/20141122/rip-free-apps-apple-tweaks-app-store-to-replace-free-button-with-get-button-heres-why.htm
Settlement in Apple Case Over E-Books Is Approved
A federal judge on Friday approved a settlement in which Apple could begin paying $400 million to as many as 23 million consumers related to charges that it violated antitrust law by conspiring with publishers to raise e-book prices and thwart efforts by Amazon.
Judge Denise L. Cote of Federal District Court in Manhattan approved an unusual settlement reached this summer in which Apple agreed to pay $400 million to consumers in cash and e-book credits, and $50 million to lawyers.
The case was first tried before Judge Cote in July 2013. In her verdict, she concluded that Apple had been fully aware of the publishers’ frustration with Amazon’s pricing of $9.99 for new releases because it was eroding the perceived value of their books. She said Apple used that leverage, combined with a tight deadline for the introduction of the iPad, to pressure publishers into agreeing to sell their books through Apple’s iBookstore.
“Apple seized the moment and brilliantly played its hand,” Judge Cote wrote in that ruling.
http://www.nytimes.com/2014/11/22/technology/judge-approves-450-million-settlement-in-apple-e-book-case.html?_r=0
Apple's $450 million e-books settlement gets final approval
Although the settlement is final, Apple only has to pay that amount if it loses its appeal of a 2013 price-fixing ruling. If the appeal is successful, Apple will pay only $50 million to ebook purchasers and $20 million to attorneys.
http://www.macworld.com/article/2851352/apples-450-million-ebooks-settlement-gets-final-approval.html
The Masque security bug may pave the way for data to be stolen from legitimate app sources on iOS devices, according to Trend Micro researchers.
Trend Micro is a company that sells anti-malware software.
While Apple is unaware of any reported incidents of the bug, researchers say the flaw could theoretically install malware or steal user data from iPads or iPhones.
However, most users need not worry as malicious apps are barred from the relative safety of Apple's App Store — so if you keep downloads within this sphere, the chance of your device being hijacked is minimal.
http://www.zdnet.com/apple-ios-masque-flaw-dangers-legitimate-app-infiltration-discovered-7000036045/
5 Best Open Source Web Browser Security Apps
http://www.smallbusinesscomputing.com/biztools/5-best-open-source-web-browser-security-apps.html
Now you can search every tweet that was ever sent
http://www.computerworld.com/article/2849324/now-you-can-search-every-tweet-that-was-ever-sent.html
Next Year, One Billion Works Will Be Free to Use Online
The number of creations under open 'Creative Commons' licenses has doubled since 2010.
http://www.theatlantic.com/technology/archive/2014/11/more-than-one-billion-creative-commons-works-in-2015/383014/
When Fitbit Is the Expert Witness
An upcoming court case will use fitness-tracking data to try and prove a plaintiff's claim, bringing us one step closer to the new age of quantified self incrimination.
Self-tracking wearable devices can store up data over time that could be used against you in court.
The first known court case using Fitbit activity data is underway. A law firm in Canada is using a client's Fitbit history in a personal injury claim.
wearables data could just as easily be used by insurers to deny disability claims, or by prosecutors seeking a rich source of self-incriminating evidence.
Will it change people's relationship to their wearable device when they know that it can be an informant?
http://www.theatlantic.com/technology/archive/2014/11/when-fitbit-is-the-expert-witness/382936/
Your outdated Internet browser is a gateway for cyber attacks
http://www.pbs.org/newshour/bb/spam-nation-your-outdated-internet-browser-is-a-gateway-for-cyber-attacks/
An Identity Theft Victim's Story:
'Someone Had Taken Over My Life'
http://www.forbes.com/sites/laurashin/2014/11/18/someone-had-taken-over-my-life-an-identity-theft-victims-story/
Protect your medical data from identity theft
Hackers, notorious for stealing credit- and debit-card information from stores, and other thieves are increasingly targeting medical records, which can be more valuable because they include such coveted data as Social Security numbers, birth dates, driver's license numbers and checking-account numbers, experts say.
A good place to start protecting yourself, say experts, is refusing to provide your Social Security number on forms or elsewhere, which is the key to identity theft. Medical providers usually ask for this number, even though it is rarely needed.
Many hospitals also ask for driver's license numbers, says Peel, even though they are also seldom required.
shred any medical documents, say experts, such as old medical bills and records. Current medical papers and electronic records should be kept in a secure place.
http://www.marketwatch.com/story/protect-your-medical-data-from-identity-theft-2014-11-17
Blog Archive
-
▼
2014
(176)
-
▼
December
(15)
- The Editor's Year-End Summary for 2014
- Senior Correspondent Arnold Woodworth's Year-End W...
- Set Up and Get to Know Your New Mac
- Set Up and Get to Know Your New Mac
- I need the administrative password for this Mac I ...
- Senior Correspondent Arnold Woodworth's Weekly Web...
- How to be your family's tech-support hero during t...
- Senior Correspondent Arnold Woodworth's Weekly Rou...
- Rare photos of the SR-71 Blackbird show its amazin...
- Add shortcuts for the PDF menu items in Print dial...
- Discontinued iPod Classic Sells on Amazon | News &...
- Senior Correspondent Arnold Woodworth's Weekly We...
- Squirrels AirParrot 2 (for Mac) Review & Rating | ...
- Finder labels too subtle? Create garish folder ico...
- Thoughts from an old man on kids learning how to code
-
▼
December
(15)


