The MacValley blog
![]()
Welcome to the MacValley blog, your first stop for all the latest MacValley news and views.
|
The MacValley blog Editor: Tom Briant
|
Labels used in posts
|
To search the blog posts please use the box below
Monday, March 28, 2016
How to Regain Access to a locked folder after you reinstall OS X
I recently did a very dumb act. I tried to install a upgrade from 10.11.3 to 10.11.4 without first ensuring that I had an up to date backup.
I’m paying the consequences. Hunting down files and such.
I did install OS X 10.11.4 after erasing the old installation, but I made a mistake. I didn’t use the same user name as I used before. This locked me out of folders that I had easily accessed before.
Here’s how I regained access. No, it doesn’t require you to use arcane Terminal commands You will use Terminal, but only to see what your user name is now.
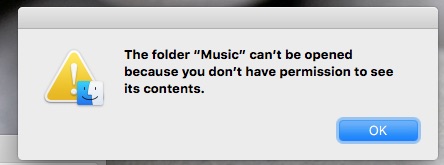
First, the situation. I wanted to access a copy of my Home (or User) folder made on 10-10-2015. This is what I saw when I tried to access my Music folder from my new OS X installation:

When you see that red badge on a folder, OS X has locked you out. It doesn’t recognize you. What?! It’s me! But you’re not the same “me” that created that folder.
So you need to right-cllicl or control-click on that folder (or go to the File Menu) and select Get Info:

Now here’s where I found my error. I clicked on Get Info and I opened Terminal, because the prompt in Terminal shows your user name:

Now as user “thomas” I have read and write privileges to the Music folder.
But wait! I’m not logged in as user “thomas”. I’m logged in as “thomasbriant”. As far as OS X is concerned, that’s a completely different user.
So how do I regain access?
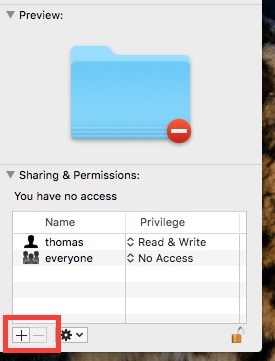
First, click on the padlock in the lower right-hand corner of the Get Info window.
Second, click on the “+” sign in the lower left-hand corner of the Get Info window.

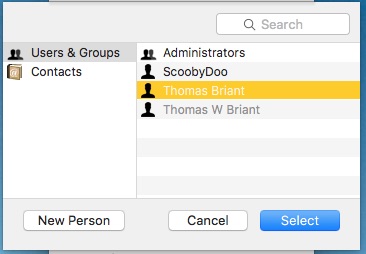
Aha! The user “thomasbriant” is listed. So click on that name and hit Select.
Now I have access. Admittedly, it’s read-only access, but at least I can access my Music folder.
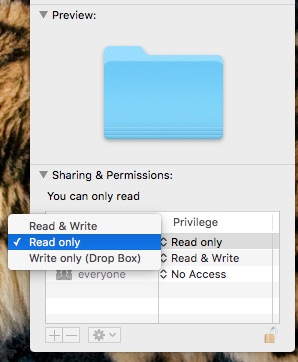
And from here, if I click on the double-headed arrows immediately to the left of “read-only” I can upgrade my privileges to read and write.

Now I have full access to that Music folder and all its treasures:
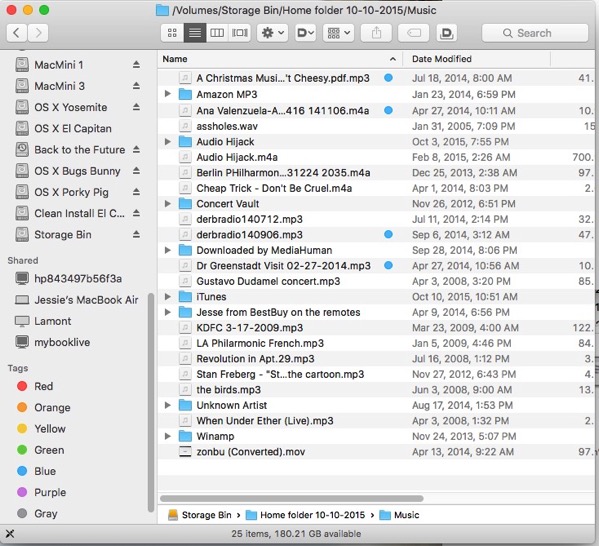
You may disagree with my tastes in music, but you’ll see no red “access denied” badges on these folders!
So that’s how to gain access to an otherwise locked folder.
And always, Always, ALWAYS back up before you do an OS X upgrade. You never know when you might brick your machine.
Tom Briant
Editor, MacValley Blog
Saturday, March 26, 2016
Senior Correspondent Arnold Woodworth's Weekly Web Wrap-up for March 25, 2016
Apple Posts Updated iOS 9.3 Build For iPad 2 Users Bitten By Activation Bug
Users of some iOS devices, especially owners of second generation iPads, found themselves unable to advance past the activation screen after upgrading to iOS 9.3.
Apple has since released a new build of iOS 9.3, build 13E236, which completely fixes the activation error.
http://hothardware.com/news/apple-posts-updated-ios-93-build-for-ipad-2-users-bitten-by-activation-bug
My credit card was stolen, but I found out right away thanks to Apple Pay
Apple Pay sent this person’s iPhone a notification of two purchases he didn’t make within seconds of when they occurred.
http://www.businessinsider.com/my-credit-card-was-stolen-but-i-found-out-right-away-thanks-to-apple-pay-2016-3
The 12 best hidden features in the new iPhone update
http://www.businessinsider.com/hidden-features-and-tips-for-ios-93-2016-3
11 paid iPhone apps on sale for free for a limited time
These are paid iPhone and iPad apps that have been made available for free for a limited time by their developers. There is no way to tell how long they will be free. These sales could end an hour from now or a week from now — obviously, the only thing we can guarantee is that they were free at the time this post was written (Friday March 25).
http://bgr.com/2016/03/25/best-free-iphone-apps-ipad-mar-25/
the new iPad Pro has a high-performance 12-megapixel camera that can record 4K video.
It's for capturing super sharp, high-res photos and videos, and working with/on them on the same device.
This is a camera and an editing station for professionals in a single device.
http://www.businessinsider.com/why-the-new-ipad-pro-has-a-good-camera-2016-3
I've been pleasantly surprised by the new iPad Pro
I didn't expect to like the new 9.7-inch iPad Pro.
But ...... it feels as if Apple took the already excellent iPad Air 2 and supercharged it with a better screen, more power, and the option to connect it to a keyboard or use it with the well-received Apple Pencil.
http://www.businessinsider.com/ipad-pro-9-7-inch-first-impressions-2016-3
Review: iPhone SE puts the same engine in a smaller exterior
What does SE stand for? Apple says Special Edition, but you could also sum it up this way: Same Engine, Smaller Exterior.
The $400 for this Smartphone Extraordinaire is a Smart Expenditure. Its 1.5-day battery life means that it only Sips Energy. Very Solid Equipment, even if it is a Special Edition for people with Small Extremities.
https://www.yahoo.com/tech/review-iphone-se-stands-for-1392832165552182.html
So who would want a more petite iPhone?
Plenty of people, it turns out.
http://www.nytimes.com/2016/03/24/technology/personaltech/who-will-like-the-new-smaller-iphone-se.html?emc=edit_ct_20160324&nl=personaltech&nlid=11893479&_r=0
It’s time to upgrade: iPhone SE vs. iPhone 5S spec showdown
To help you decide if you finally want to upgrade, we’ve pitted the now-discontinued iPhone 5S against the new iPhone SE. This article has a detailed breakdown of the specs for each device.
http://www.digitaltrends.com/mobile/iphone-se-vs-iphone-5s/
The iPhone SE has incredible battery life
http://www.techinsider.io/apple-iphone-se-incredible-battery-life-2016-3
Video:
5 ways you are screwing up your iPhone battery
http://www.techinsider.io/iphone-battery-life-mistakes-2016-3
Video:
9 iPhone keyboard tips only power users know about
http://www.businessinsider.com/keyboard-tips-iphone-6s-apple-texting-imessage-message-2016-3
How Much Money You’ll Make When You Recycle Through Apple’s Renew Program
http://lifehacker.com/how-much-money-you-ll-make-when-you-recycle-through-app-1766610009
Why I’m skeptical about Apple’s future
the way innovation happens now: You release a basic product and let the market tell you how to make it better. There is no time to get it perfect; it may become obsolete even before it is released.
Apple hasn’t figured this out yet. It maintains a fortress of secrecy and its leaders dictate product features.
There is nothing earth shattering or compelling about Apple’s new phones — or any of the products it has released since 2007.
https://www.washingtonpost.com/news/innovations/wp/2016/03/23/why-im-skeptical-about-apples-future/
Here’s a different view about Apple’s future – MacWorld debunks the Washington Post article.
The Washington Post wrote "You release a basic product and let the market tell you how to make it better."
That’s one way to do it, particularly if you want to end up with the Homer (a television parody of the Edsel). Or Linux. There is another way, though, and that’s by employing people with good taste and having them figure out the best way to make a product.
The Washington Post wrote "Consider that its last major innovation — the iPhone — was released in June 2007."
If that’s the standard for a “major invention” — a device that created the most important industry of the last 10 years — has any other technology company had any “major inventions” in the last 20?
http://www.macworld.com/article/3048421/ios/do-nothings-apple-needs-to-ship-more-hot-garbage.html
The 32 ads which tell the story of how Apple became the most valuable brand in the world
http://www.businessinsider.com/apple-history-through-advertising-40-years-anniversary-2016-3-26
Video:
Consumer Reports just rated Samsung's new Galaxy phone better than the iPhone
http://www.businessinsider.com/consumer-reports-samsung-s7-galaxy-better-than-iphone-6s-2016-3
Cracking the Mystery of the Missing iTunes Files
How iTunes sometimes loses track of songs and how to re-connect iTunes to the “missing” songs.
http://www.nytimes.com/2016/03/19/technology/personaltech/cracking-the-mystery-of-the-missing-itunes-files.html?emc=edit_ct_20160324&nl=personaltech&nlid=11893479
Taking Someone Off Your iPhone’s Blocked List
http://www.nytimes.com/2016/03/24/technology/personaltech/taking-someone-off-your-iphones-blocked-list.html?emc=edit_ct_20160324&nl=personaltech&nlid=11893479
These Apps Promise to Encrypt Your Smartphone Communications
Signal, one of the best known private messaging apps, is free on iOS and Android. Its makers promote it with the slogan “privacy is possible,” and it uses end-to-end encryption, ensuring that only the recipient of the communications can read them. Its encryption and privacy protections are highly rated by the Electronic Frontier Foundation, a digital rights group.
To talk, both parties must have Signal installed.
Several other apps are discussed in this article.
http://www.nytimes.com/2016/03/24/technology/personaltech/encryption-by-app-adds-security-to-smartphones.html?emc=edit_ct_20160324&nl=personaltech&nlid=11893479
We’re More Honest With Our Phones Than With Our Doctors
in recent years, mobile technology has granted me and countless others the ability to collect an unprecedented amount of information about our habits and well-being. Our phones don’t just keep us in touch with the world; they’re also diaries, confessional booths, repositories for our deepest secrets. Which is why researchers are leaping at the chance to work with the oceans of data we are generating, hoping that within them might be the answers to questions medicine has overlooked or ignored.
After a few months, the apps weren’t just a repository of daily facts; they had become a legible map to my body. My period no longer caught me off guard, and I eventually learned to connect the arc of my cycle to changes in mood, appetite, fatigue and sex life, and adjust my routines accordingly. By now, I have years of data about my periods and an extremely accurate understanding of how my body works: when I’m likely to experience cramps and breast pain, when to skip yoga and social outings because I’ll need more sleep. All my life, my doctors tended to be vague, making my bodily functions seem ultramysterious, when in fact they are just individualized, and easily understood with the assistance of software.
By divulging every last detail to these apps, we make them incredibly valuable — but also potentially ruinous, if our most sensitive records were to fall into the wrong hands. Clue repeatedly talked up its airtight security, and I currently believe the company about that, just as I once believed eBay’s, Snapchat’s and Evernote’s claims that their services were safe. And yet each was hacked, eventually.
http://www.nytimes.com/2016/03/27/magazine/were-more-honest-with-our-phones-than-with-our-doctors.html?emc=edit_ct_20160324&nl=personaltech&nlid=11893479
At least two dozen cars are vulnerable to being remotely unlocked and started with simple equipment that costs about $225, according to research from German automobile club ADAC.
this type of threat has been around since at least 2011, when Swiss researchers demonstrated it. But five years later, car manufacturers haven't done much to fix the problem.
http://www.techinsider.io/car-radio-amplifier-hack-2016-3
What Is a Robot?
The question is more complicated than it seems.
Humanity, and what it means to be a human, will be defined in part by the machines people design.
“We design these machines, and we have the ability to design them as our masters, or our partners, or our slaves,” said John Markoff.
philosopher Georg Wilhelm Friedrich argues that holding a slave ultimately dehumanizes the master.
Computers help us with information tasks and robots help us with physical tasks.
For a robot to be a robot, many roboticists agree, it has to have a body.
Neil Richards, a law professor, and William Smart, a computer science professor, wrote that it’s essential for humans to think of robots as tools, not companions.
sophisticated autonomous systems may be misunderstood as having free will.
http://www.theatlantic.com/technology/archive/2016/03/what-is-a-human/473166/
In Apple vs. FBI, Remember the Memory Chip
The Federal Bureau of Investigation said, one day prior to a scheduled courtroom hearing with Apple, that it had learned of a possible alternate means of breaking into the iPhone once used by Syed Rizwan Farook, one of the San Bernardino shooters. Talk about being down to the last minute.
The best rundown I’ve seen of how the method might work was written by Jonathan Zdziarski, a computer forensics expert who specializes in Apple products, on his personal blog.
http://fortune.com/2016/03/26/apple-fbi-intel-andy-grove/
Report: Apple designing its own servers to avoid snooping
Apple suspects that servers are intercepted and modified during shipping.
the National Security Agency is known to intercept and modify equipmentbefore it reaches the hands of its intended customers.
Apple has used both Amazon Web Services (AWS) and Microsoft Azure to run parts of iCloud, and recently the company began using the Google Cloud Platform as well.
But Apple wants to rely more on its own data centers, hence the project to design its own hardware. This isn't just about security. VentureBeat reported last week that "Apple isn’t happy with the fact AWS is not able to very quickly load photos and videos onto users’ iOS devices," and it's thus building more of its own infrastructure.
http://arstechnica.com/information-technology/2016/03/report-apple-designing-its-own-servers-to-avoid-snooping/
Hackers forced Kentucky hospital into ‘internal state of emergency’
A Kentucky hospital says its networks have been restored after “working in an internal state of emergency” thanks to hackers who infected its data system and demanded payment a ransom to turn it back on, prompting the organization to use backup files.
An employee had opened a malicious email that made it past spam filters, infecting part of its data network with ransomware. Ransomware is a computer virus that locks up files until the victim pays a ransom, usually in bitcoin.
The Kentucky hospital did NOT pay any ransom and is working with local police and the Federal Bureau of Investigation.
The attack comes just weeks after Hollywood Presbyterian Medical Center was hit with ransomware and paid $17,000 to hackers.
http://www.marketwatch.com/story/hackers-forced-kentucky-hospital-into-internal-state-of-emergency-2016-03-23
FBI Director James Comey is defending the agency's battle with Apple, saying it is about fighting terrorism and not about setting legal precedent.
The arguments essentially boil down to assertions that the FBI lied when stating that it could not open the iPhone used by San Bernardino terrorist Syed Farook and that it wanted a court of law to compel Apple's assistance in order to set a legal precedent.
Comey emphatically denied this idea and repeated that the FBI did not have the ability to access Farook's phone. Instead, he said that the FBI decided to tentatively retreat once it was presented with a possible viable solution—which happened to come just one day before the court hearing.
http://arstechnica.com/tech-policy/2016/03/fbi-director-says-fight-with-apple-about-terrorism-not-setting-precedent/
Britain’s government wants to spy on its citizens
Six of the biggest American technology firms have combined forces to call for major changes to the Investigatory Powers bill, commonly known as the snooper’s charter.
While the bill contains a number of measures that could be seen as requiring companies to weaken their users’ security, it contains little language to the contrary. In their submission, Apple et al “urge the government to make clear that actions taken under authorisation do not introduce new risks or vulnerabilities for users or businesses, and that the goal of eliminating vulnerabilities is one shared by the UK government”.
http://www.theguardian.com/technology/2016/mar/24/apple-google-call-for-changes-snoopers-charter
The snooper’s charter is flying through parliament. Don’t think it’s irrelevant to you
even as the British media and public follow developments in the Apple case, they seem to overlook its relevance to Britian’s investigatory powers bill.
This can in part be explained by differences in British and American attitudes to surveillance. Edward Snowden’s revelations regarding the surveillance activities of the US government sparked outrage among Americans, but failed to make a similar impact in the UK.
Should the British bill pass in its current form, the UK government will have the power to force Apple and other technology companies to undermine the security of their products and services.
http://www.theguardian.com/commentisfree/2016/mar/14/snoopers-charter-apple-fbi-bill-hacking-gagging
Monday, March 21, 2016
Special iOS 9.3 upgrade round-up by Senior Correspondent Arnold Woodworth
iOS 9.3 is ready to install with Night Shift, password-protected Notes, and more
you should upgrade to iOS 9.3 as soon as it’s convenient, as it contains the fix for an iMessage bug that was just reported.
http://www.macworld.com/article/3046456/software/ios-93-is-ready-to-install-with-night-shift-password-protected-notes-and-more.html
Apple iOS 9.3: Should You Upgrade?
Well done Apple. iOS 9.3 is now available and the company deserves a pat on the back. Why? Yes it’s a major update, but the real credit goes to Apple for putting it through no less than seven betas and testing it for almost twice as long as the problem filled iOS 9.0 and iOS 9.1.
http://www.forbes.com/sites/gordonkelly/2016/03/21/apple-ios-9-3-should-you-upgrade/#63bf44432048
Video:
Apple Highlights: Smaller iPhone, iPad, New Features
Good summary of Apple’s latest new products intro.
http://www.marketwatch.com/video/apple-highlights-smaller-iphone-ipad-new-features/E0A1F90D-5667-4FF6-8527-2818DF8E9D9F.html
Video:
More on Apple’s late product announcement
http://www.marketwatch.com/video/iphone-se-and-ipad-pro-apple-deja-vu-moment/3F0E5978-A797-452C-837E-02A73A13940A.html
Here's everything Apple just announced
Apple’s latest product announcement – in reverse chronological order
http://www.businessinsider.com/apple-event-live-blog-iphone-se-ipad-pro-2016-3
Video:
Apple's Liam, a robot that recycles iPhones
http://www.computerworld.com/video/63524/apples-liam-a-robot-that-recycles-iphones
Inside Liam, Apple's super-secret, 29-armed robot that tears down your iPhone
Liam is programmed to carefully disassemble the many pieces of returned iPhones, such as SIM card trays, screws, batteries and cameras, by removing components bit by bit so they’ll all be easier to recycle. Traditional tech recycling methods involve a shredder with magnets that makes it hard to separate parts in a pure way (you’ll often get scrap materials commingled with other pieces).
Liam separates the insides of an iPhone with robotic precision so, for example, pieces of glass and plastic won’t be mixed in with copper. Ultimately, these components can be sold to recycling vendors that focus on specific materials, such as nickel, aluminum, copper, cobalt and tungsten (a conflict mineral), and turn them into something else that can be reused, rather than dumped in a landfill. Some of these materials take decades to decompose and leak toxic materials into the ground along the way.
Liam completes an iPhone disassembly process every 11 seconds, with dozens running through the system at all times.
About 350 units are turned around each hour, equivalent to 1.2 million iPhones each year. Apple wouldn't say when Liam started its work, but emphasized the project is still in the research and development stages.
http://mashable.com/2016/03/21/apple-liam-recycling-robot/#VADO.CJT1qqV
The FBI may be backing out of its case against Apple
"An outside party demonstrated to the FBI a possible method for unlocking Farook's iPhone," reads the motion.
The hearing may not happen at all if the FBI is able to access the iPhone without Apple's help. It sounds like the agency wants to give this method a shot before going through a long legal battle with Apple.
https://assets.documentcloud.org/documents/2773489/2016-03-21-Ex-Parte-Application-Dckt-191-0.pdf
Apple’s CareKit Is the Best Argument Yet for Strong Encryption
CareKit, which would let developers introduce health care apps capable of monitoring a wealth of information though Apple devices. The kind of data that you’d want to guard as closely as your own heartbeat.
FBI Director James Comey often complains of “dark spaces” that could help terrorists.
If anything merits the safety of a “dark space,” it’s our biological ticks and tocks, our blood pressure and our treatments and our tremors. Those things are ours, and no one else’s, whether they’re in our bodies or in our phones.
“If we are going to trust Apple with this data, I think this makes a very strong argument for keeping the data away from prying eyes,” says Jake Williams.
http://www.wired.com/2016/03/apples-carekit-best-argument-strong-encryption-yet/
Beyond surveillance: what could happen if Apple loses to the FBI
An Apple loss in the San Bernardino encryption case risks creating a world in which we can no longer trust the gadgets that track how we drive, when we’re home and whether the door is locked.
Public opinion polls commissioned by Pew and the Wall Street Journal/NBC Newsshow that Americans narrowly back the FBI over the iPhone maker. The problem for Apple and its backers is that consumers tend to put perceived near-term risks, such as mass shootings, over theoretical ones – like Big Brother.
Public opinion polls commissioned by Pew and the Wall Street Journal/NBC Newsshow that Americans narrowly back the FBI over the iPhone maker. The problem for Apple and its backers is that consumers tend to put perceived near-term risks, such as mass shootings, over theoretical ones – like Big Brother.
http://www.theguardian.com/technology/2016/mar/21/apple-fbi-encryption-battle
How Self-Driving Cars Will Threaten Privacy
Automated vehicles will learn everything about you—and influence your behavior in ways you might not even realize.
In this near-future filled with self-driving cars, the price of convenience is surveillance.
This level of data collection is a natural extension of a driverless car’s functionality.
cars will collect reams of information about the people they drive around—like the data Uber has amassed about its customers’s transportation habits.
The companies building self-vehicles have been cagey, so far, about how they’re thinking about using individual data.
http://www.theatlantic.com/technology/archive/2016/03/self-driving-cars-and-the-looming-privacy-apocalypse/474600/
Edward Snowden: Privacy can't depend on corporations standing up to the government
Relying on corporations to protect private data is bad enough in a vacuum – but Snowden pointed out that many tech giants have already proven more than willing to hand over user data to a government they rely on for licensing and a favorable regulatory climate.
He particularly singled out service providers as being complicit in overreaching government surveillance.
http://www.networkworld.com/article/3046135/security/edward-snowden-privacy-cant-depend-on-corporations-standing-up-to-the-government.html
Get a taste of coding with this affordable and beginner-friendly web developer course
Having the chance to try a whole selection of web tools may allow you to figure out which aspect of the web development process you want to delve further into in your next course. Right now, the course is available for just $19.
http://www.businessinsider.com/become-a-web-developer-from-scratch-udemy-coding-online-class-deal-2016-1
OS X 10.11.4 and iOS 9.3 are out and about
Hi All:
Though Apple didn’t announce at the presentation today, OS X 10.11.4 is now out. I’m downloading it even as you read this from the Mac App Store.
And don’t forget to update to iOS 9.3.
Tom Briant
Editor, MacValley Blog
Senior Correspondent Arnold Woodworth's Weekly Web Wrap-up for Sunday, March 20, 2016
One year later, Apple's 12-inch MacBook has become my favorite laptop
Apple's computer OS is simply better at tasks that benefit a small pick-up-and-play laptop, from instantly (and reliably) waking from sleep to easy app switching through multi-finger touchpad gestures to simple file previews via a tap of the space bar. It does lack a touch screen, something standard on nearly every new Windows laptop in its price class, but the especially intuitive multitouch touchpad gestures make up for a least some of that missing functionality.
That's why, despite testing and using nearly every new laptop or 2-in-1 hybrid released over the past year, I find myself returning again and again to the 12-inch MacBook. It's become my default go-to for those times when I need a laptop that's quick and easy to pick up and use.
http://www.cnet.com/news/one-year-later-apples-12-inch-macbook-has-become-my-favorite-laptop/
There's a simple reason serious photographers love iPhones despite their flaws
The best smartphone camera in the world lives on an Android. But as a photographer I'm going to stick with the iPhone.
Whereas Android shooters tend to err on the side of bright overexposures, iPhones go darker, preserving details. And by keeping that saturation, contrast, and brightness under control, iPhones leave a lot more room for editing after the fact.
http://www.techinsider.io/iphones-take-better-photos-than-android-2016-3
13 ways to fix your iPhone or Mac with common household items
http://www.businessinsider.com/best-diy-apple-product-hacks-2016-3
Stock Mac Apps That Apple Quietly Made Useful
The fact is, some of the stock apps aren’t great. Some of them are.
And many apps for OS-X used to be pretty bland, but have seen some big improvements over the years.
http://lifehacker.com/all-the-stock-mac-apps-that-apple-has-quietly-made-usef-1764376667
Video:
How to send self-destructing messages — and other iPhone messaging tricks
http://www.businessinsider.com/iphone-messaging-tricks-apple-smartphone-tech-mute-location-forward-2016-3
Setting Hourly Alarms on Apple Devices
Various ways to set an hourly alarm to remind you to get out of your chair and exercise a little (and be less sedentary)
http://www.nytimes.com/2016/03/10/technology/personaltech/setting-hourly-alarms-on-apple-devices.html?emc=edit_ct_20160310&nl=personaltech&nlid=11893479&_r=0
14 apps every modern gentleman should have on his phone
http://www.businessinsider.com/apps-every-every-man-should-have-on-his-phone-2016-3
iOS 9.1 Jailbreak is here – Some things you need to know
A discussion of the benefits and the risks, and the limitations of jailbreaking an iPhone.
And reasons why most people DON’T need to jailbreak their iPhones.
http://www.slashgear.com/ios-9-1-jailbreak-is-here-some-things-you-need-to-know-15431762/
Video:
A Fully Functional Computer for $79? Yep
http://www.marketwatch.com/video/a-fully-functional-computer-for-79-yep/08BA3EB8-724B-44A8-861D-15DE096F820D.html
A Brief History of Robot Law
A new paper by Ryan Calo, a law professor at the University of Washington, paints a surprisingly colorful picture of this history, which Calo dates back to a 1947 plane crash involving an Army fighter plane on autopilot.
So far, courts have mostly treated robots as mindless machines and held humans responsible for their actions. What’s changing now, Calo says, is that robots are becoming more capable of acting and thinking for themselves. “What’s exciting about robotics today, in part, is that they’re able to solve problems in ways people wouldn’t, and that’s not something courts have encountered or even imagined,” he says.
Based on his historical review, however, Calo worries that judges are too attached to an outmoded view of robots as machines that “do the specific bidding of people.” Unless they update that view, their decisions may not all be wise and just.
http://www.theatlantic.com/technology/archive/2016/03/a-brief-history-of-robot-law/474156/
http://papers.ssrn.com/sol3/papers.cfm?abstract_id=2737598
an important guideline for dealing with AIs. We need to understand and internalize that no matter how well they imitate or outperform humans, they will never have the intrinsic empathy or morality that causes human subjects to opt not to flip the switch.
A really good rule for the use of AIs would be: “Would I put a sociopathic genius in charge of this process?”
http://www.businessinsider.com/google-just-proved-how-unpredictable-artificial-intelligence-can-be-2016-3
How to Get College Credit Without Going to College Classes
Compared to the usual route, competency-based education (CBE) is an often faster and cheaper path to a diploma, designed by colleges and universities with busy working adults in mind.
students in competency-based education programs prove they’ve mastered the material through tests or projects.
There are at least 40 colleges and universities that offer competency-based education programs.
There’s no limit to the number of credits you can earn through many of these programs, but there’s one caveat: Depending on the program, credits might not be transferrable to other colleges or universities, so watch out for that if you plan to transfer credits.
It’s never too late to get that degree, especially when you have a cheaper, faster, and more personalized option than the traditional butts-in-seats model.
http://lifehacker.com/how-to-get-college-credit-without-going-to-college-clas-1764267835
JOHN McAFEE: Here's what it means to be a 'cybersecurity expert’
A very interesting article.
http://www.businessinsider.com/john-mcafee-defines-cybersecurity-expert-2016-3
Edward Snowden Interview on Apple vs. FBI, Privacy, the NSA, and More
A very good interview.
https://www.youtube.com/watch?v=o8pkUTav0mk
John Oliver has the only explanation for the Apple vs. FBI case worth watching
The video is at the end of the article. It’s very good.
http://www.businessinsider.com/john-oliver-explains-apple-vs-fbi-case-2016-3
San Francisco lawmakers use a secret messaging app to keep chats from prying public eyes
Telegram, a self-destructing messaging app, has become popular among San Francisco public officials as a way to evade public records laws, says a report in The Information.
Telegram rose to notoriety after it was apparently used by ISIS members to spread propaganda. Telegram shut down almost 80 such channels last November.
http://www.businessinsider.com/san-francisco-lawmakers-use-telegram-app-2016-3
Former CIA Head: The FBI is wrong about Apple
The former head of the NSA and CIA, General Michael Hayden, has a counter-intuitive view when it comes to the stand-off between Apple (AAPL) and the FBI: He sides with Apple.
“You can parse this problem in a lot of ways. Constitutionally: does the government have a right to order it? I’m not a constitutional lawyer. I’ll let those guys settle that. Privacy? He’s dead. Never his phone. I don’t think it’s a privacy issue. I’m looking at it as a security issue,” he said. “I think on balance, America ends up in a less secure place if we somehow weaken what now appears to be very unbreakable encryption in the iPhone.”
http://finance.yahoo.com/news/former-cia-head--the-fbi-is-wrong-about-apple-165603222.html
Apple’s Brief Hits the FBI With a Withering Fact Check
APPLE’S LATEST BRIEF in its battle with the FBI over the San Bernardino iPhone offered the tech company an opportunity to school the Feds over their misinterpretation and misquotations of a number of statutes and legal cases they cited as precedent in their own brief last week. Many viewed Apple’s arguments as a withering commentary on the government’s poor legal acumen.
Edward Snowden said "Today I learned that #Apple has way better lawyers than the DOJ.”
But the tech giant didn’t stop there. It also pointed out a number of technical errors the government’s forensic experts made.
http://www.wired.com/2016/03/apple-fact-checks-the-feds-in-latest-brief/
Apple's latest legal filing: 'The Founders would be appalled’
While Apple’s brief focuses on the law, it doesn’t ignore the broader context of the encryption debate. This is bigger than the FBI and Apple disagreeing about if and how to break into Farook’s iPhone, in other words, and even top officials that used to work for the government can see the risk.
Good laws come with limits. In its earlier motion to dismiss the court order, Apple complained that the All Writs Act, since it’s designed to fill in the gaps between statutes, doesn’t have that limiting principle.
http://www.macworld.com/article/3045042/security/apples-latest-legal-filing-the-founders-would-be-appalled.html
Link to PDF of FBI brief of 9 March, 2016
https://www.emptywheel.net/wp-content/uploads/2016/03/160310-Pluhar-2-1.pdf
Link to Apple’s Response to above FBI brief
https://assets.documentcloud.org/documents/2762147/Reply-Brief-in-Support-of-Apple-s-Motion-to-Vacate.pdf
6 Powerful Quotes from Apple’s Newest Court Filing
http://www.macobserver.com/tmo/article/6-powerful-quotes-from-apples-newest-court-filing
Android, iOS on Opposite Sides of Encryption Divide
Most Android phones are not encrypted, either by user choice or manufacturer design. About 95 percent of all iPhones are encrypted, compared with less than 10 percent of Android phones.
Why? Google has been slow in mandating full-disk encryption. The feature generally is turned off by default in Android smartphones that have it.
"When it comes to security threats on mobile devices, there is no comparison. Studies show that as much as 97 percent of all mobile malware targets Android, while iOS suffers from functionally none," said Alex Pezold, CEO ofTokenEx.
"This is deeper than just encrypting data. Android phones are outright sitting ducks to a degree," he told LinuxInsider.
Apple has simplified the process of encrypting its devices and their contents, but it requires using a passcode.
"This is something more than 64 percent of smartphone users do not do," said Navroop Mitter.
http://www.technewsworld.com/story/83253.html
JOHN McAFEE: Hacker group Anonymous just declared war on Trump — here's why he'll soon have a different view of cybersecurity
As a longtime observer of Anonymous, I have never seen preparations to this extent for any prior hack in the group's history. Its level of assurance in the success of its attack, in spite of giving advanced notice, indicates that it wants the world to watch an event of serious proportions.
I am personally conflicted by this coming event. Anonymous is partly composed of the very talent that America needs to protect itself from a near certain cyberwar with China, Russia, or some other potentially hostile state. Its core beliefs embrace personal privacy and freedom, which coincide with my own beliefs. And the group has supported our government in times of crisis and was instrumental in crippling ISIS in its social-media campaigns.
On the other hand, I cannot help feeling sympathy for Trump. I am fully aware of what Anonymous is capable of, and I fear that Trump is not.
http://www.businessinsider.com/anonymous-declares-war-on-trump-john-mcafee-wants-to-help-2016-3
The company protecting Trump's websites isn't afraid of an Anonymous cyber-attack
"We see [distributed denial-of-service] attacks all the time," said Matthew Prince.
http://www.techinsider.io/cloudflare-ceo-anonymous-ddos-attacks-2016-3
How far have we come with HTTPS? Google turns on the spotlight
HTTPS is widely considered one of the keys to a safer Internet, but only if it's broadly implemented. Aiming to shed some light on how much progress has been made so far, Google launched a new section of its transparency report dedicated to encryption.
Included in the new section is data that highlights the progress of encryption efforts both at Google and on popular third-party sites.
http://www.computerworld.com/article/3044500/internet/how-far-have-we-come-with-https-google-turns-on-the-spotlight.html
U.S. seeks ideas from professionals to hobbyists on use of available technologies in terror attacks
In an earlier time, DARPA pulled together small groups of technical experts to help it see how potential adversaries might use available technology.
But today, "the easy availability in today's world of an enormous range of powerful technologies means that any group of experts only covers a small slice of the available possibilities," said John Main, who is heading the program for DARPA, in a statement.
http://www.computerworld.com/article/3043984/security/defense-dept-wants-your-help-in-imagining-the-worst.html
Reader Comment:
What will DARPA do when they find that the terrorism our nation faces now as well as in the future is just another tool our own government uses to control it's citizens? Terrorism definition: the use of violence and intimidation in the pursuit of political aims. The only way to defeat terrorism is to refuse to be intimidated and refuse to live in fear. "The only thing we have to fear...........”
Several major news sites are hosting ads infected with devastating computer viruses
A number of major news sites have inadvertently hosted ransomware that could infect visitors' computers and permanently encrypt files.
The ransomware was discovered by security researchers at Trustwave.
http://www.businessinsider.com/major-news-sites-are-hosting-ads-infected-with-viruses-2016-3
Security researchers at Palo Alto Networks Unit 42 on Wednesday announced they had discovered in the wild a method of infecting nonjailbroken iPhones with malware by exploiting design flaws in Apple's digital rights management technology.
The flaw has been exploited since 2013 largely as a means to pirate iOS software, but this is the first time it's been used to infect iPhones with malware.
This article has details on how the malware attack works.
http://www.technewsworld.com/story/Malware-Exploits-Apple-DRM-to-Infect-iPhones-83259.html
Blog Archive
-
▼
2016
(123)
-
▼
March
(13)
- How to Regain Access to a locked folder after you ...
- Senior Correspondent Arnold Woodworth's Weekly Web...
- Special iOS 9.3 upgrade round-up by Senior Corresp...
- OS X 10.11.4 and iOS 9.3 are out and about
- Senior Correspondent Arnold Woodworth's Weekly Web...
- T Rex Dancing Ballet - YouTube
- T-Rex Terrorizes NYC Comic Con - YouTube
- Senior Correspondent Arnold Woodworth's Weekly Web...
- 7 Dead Simple Ways to Make Your Computer Run Like ...
- The 22 best free Mac software apps - Features - Ma...
- Tuesday night commentary from your editor and som...
- Ransomware appears on Apple for the first time!
- Senior Correspondent Arnold Woodworth's Weekly Web...
-
▼
March
(13)


