The MacValley blog
![]()
Welcome to the MacValley blog, your first stop for all the latest MacValley news and views.
|
The MacValley blog Editor: Tom Briant
|
Labels used in posts
|
To search the blog posts please use the box below
Saturday, April 23, 2016
Senior Correspondent Arnold Woodworth's Weekly Web Wrap-up for Saturday April 23 2016
The bad: Only includes one port; Expensive
The Smartphone Revolution is dead; long live the smartphone
I'm sick of people looking at their smartphones, checking Facebook, group messaging friends, reading emails, checking the news or otherwise not focusing on the real world going on around them. I'm as bad as most other people about doing that, too. We're all sick of smartphone-dominant culture, but we all do our part to create that smartphone-dominant culture anyway. Is that going to change?
Sort of.
http://www.marketwatch.com/story/the-smartphone-revolution-is-dead-long-live-the-smartphone-2016-04-22
The scam, which appears as a shady text message, is reportedly informing users that their Apple ID has expired and they’ll need to visit a fake website to receive a new one.
The year was 2007, and Apple Inc.’s shiny handheld computer was finally being unwrapped after years of speculation. Not everyone could have predicted that just four years later, mobile devices would officially overtake the PC.
http://www.marketwatch.com/story/one-chart-shows-how-mobile-has-crushed-pcs-2016-04-20
Signaling System 7 (SS7) is a global network that connects all phone carriers around the world into a singular hub, of sorts. The hack exploits a known security flaw in SS7, but one that’s proven relatively difficult to fix due to the way SS7 is governed, or not governed, in this case.
The biggest security mistakes people make when buying things online
1) DON’T use a debit card. A credit card has better protections.
2) Advertisement E-mails: NEVER click a link from any corporate E-mail. Hackers send fake E-mails that look like corporate all the time. A few hackers write stunningly good quality fakes. They’ve even been known to fake E-mails from friends and acquaintances.
3) Fake E-mails often contain links to fake copies of corporate web sites where hackers attempt to trick you into giving them your personal info, such as social security number and credit card number so they can steal your money.
4) Instead of clicking on a link in an E-mail, type the URL of a web site in the web browser.
Every one of us is in the cross-hairs of identity thieves.
http://www.businessinsider.com/security-risks-online-shopping-adam-levin-2016-4
Closing of iTunes Movies Shows Apple Isn't Immune to Chinese Regulators
http://www.bloomberg.com/news/articles/2016-04-22/apple-says-itunes-movies-book-services-closed-down-in-china
Cartoons about encryption
http://dilbert.com/strip/2016-04-18
http://dilbert.com/strip/2016-04-19
http://dilbert.com/strip/2016-04-20
http://dilbert.com/strip/2016-04-21
http://dilbert.com/strip/2016-04-22
http://dilbert.com/strip/2016-04-23
Apple Inc. and Federal Bureau of Investigation officials, joined by independent experts, will face off in a House of Representatives hearing.
Law enforcement has argued that strong encryption that technology companies use to protect user communications allows criminals to “go dark,” or hide without being noticed.
Security experts ... say the current debate fails to recognize that creating a backdoor for the government means weakening security for all users and making people more vulnerable to hackers at a time when computer security is already poor, and breaches are all too common.
A draft of a Senate bill crafted by Republican Richard Burr of North Carolina and California Democrat Dianne Feinstein, released last week, calls for companies to comply with court orders to give the government information — making it impossible for a situation like Apple’s pushback in the San Bernardino case to occur again. Privacy advocates, such as the Electronic Frontier Foundation, called the bill “simply anti-security.”
Security experts and technology companies also say if they allow U.S. law enforcement to have a backdoor, they’d be forced by other governments worldwide to abide by similar requests.
This has happened before. In 2007, lawmakers on Capitol Hill chewed out Yahoo’s then-chief executive, Jerry Yang, for complying with the Chinese government to turn over information about journalist Shi Tao. The company said the government forced its hand with documents similar to subpoenas. Rep. Tom Lantos, a Democrat from California, told Yahoo then that “while technologically and financially you are giants, morally you are pygmies.”
“We talk about the Jerry Yang moment,” Matthew Prince, chief executive of the security company CloudFlare, told MarketWatch in a recent interview.
http://www.marketwatch.com/story/what-you-need-to-know-about-the-latest-battle-over-smartphone-security-2016-04-19
FBI admits it can’t keep up with advances in technology
The FBI has long struggled to convince tech whizzes to take jobs at the bureau. Private companies offer higher salaries, the background-check process for a government job is onerous and, on top of all that, the agency won’t hire people who have used marijuana in the last three years or any other illegal drug in the last 10 years.
http://www.marketwatch.com/story/fbi-admits-it-cant-keep-up-with-advances-in-technology-2016-04-19
Reader comment:
The consequences of this idea to develop back doors to encryption will have devastating effects on all US tech companies that do business around the world. As soon as the US passes a law requiring tech companies to do this then every other Govt in the world will demand the same access and then lots of rogue officials in those Govt's will sell the access to criminal and terrorist organizations
Either something is secure or it is not. The entire future depends on secure encryption so if we do this as a country we wreck our tech industries and make all American citizens a lot more vulnerable to malicious attacks.
But today, their jobs have changed, and so, apparently, have their views on privacy. Both former officials now work with technology companies like Apple at a corporate consulting firm that Mr. Chertoff founded, and both are now backing Apple — and not the F.B.I., with which they once worked — in its fight to keep its iPhones encrypted and private.
kidnappers and extortionists have seized on resources like Facebook and Twitter to identify new targets.
If they know where you are, if they know where you've been, if they know who your family are, then this is all information that they can use against you to try to extort more money.
http://www.businessinsider.com/drug-cartels-using-social-media-sites-for-crime-extortion-2016-4
The internet is the best set of parents a millennial could ask for
Baby Boomers had the skills to pass on, but withheld them out of fear that they would make their kids' lives difficult. So it should be no surprise that the generation raised on car seats, school lockdowns, and helicopter parenting grew into adults that often feel totally unprepared to open a bank account or schedule their own doctor appointments.
The one thing millennials have mastered is the internet.
the internet serves as a handy way to learn a life skill without admitting to the universe that you still feel like a child.
http://www.businessinsider.com/the-internet-is-every-millennials-third-parent-2016-4
How Hacking Is Advancing the World of Farming
Dwindling farm incomes and open-source software are inspiring homespun hackers, helping advance farming technology. Manitoba farmer Matt Reimer has created a tractor that drives itself.
http://www.marketwatch.com/video/how-hacking-is-advancing-the-world-of-farming/A66DE277-DB35-4EF2-B9C2-676DA65188B1.html
This company secretly runs the internet, and now it's raised another $8 million to rule everything else, too
Nginx — pronounced "Engine-X”.
As it stands right now, Nginx's flagship web-server technology is immensely popular, with 150 million websites using it.
Nginx's popularity also puts it in a difficult position. Most of those Nginx fans are using the free, open-source version of Nginx, where they never have to pay the company a dime for the software. But it does have two businesses: A premium version of its software and a consulting business.
http://www.businessinsider.com/nginx-raises-8-million-telstra-2016-4
Monday, April 18, 2016
Boaty McBoatface Name 'Not Suitable', Science Minister Jo Johnson Says
Boaty McBoatface Name 'Not Suitable', Science Minister Jo Johnson Says: ""
(Via.)
If you want Boaty McBoatface, get your own damn boats, peasants!
Tom Briant
Editor, MacValley Blog
Saturday, April 16, 2016
Changing Settings in MacLinkPlus and Classic-On-Intel
Now that you’ve successfully converted a lot of old Word 5.1 files, you’ve got questions. Such as:
1. What if I want the Unix icon in Classic-On-Intel to point to a different folder besides /Users/Shared? What if I want to use an external USB drive?
2. How do I change the file format I translate my old files into? Like, how do I make it Rich Text Format instead of Word 97-2004?
3. What other file formats can MacLink Plus convert besides Word 5.1?
Okay, question #1 about using a different folder on your hard drive or a whole different drive. DON’T CHANGE IT!
Classic-On-intel works well because all the pieces fit together. Don’t try to change them. You can’t reach some of the settings without digging into the application itself and possibly screwing it up. Think twice!!
End of discussion
“Fine, but what about MacLink Plus? Can I change its settings without screwing up the works?”
Yes, you can.
The Preferences for MacLink Plus are not in the place where OS X apps put them. Instead, you want to go under the Edit menu.
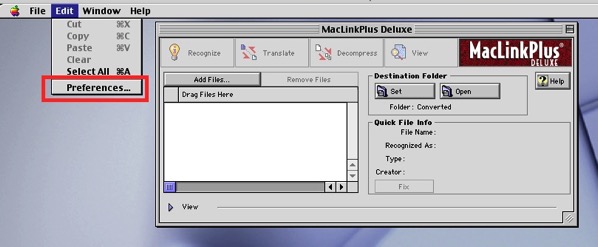
You choose the preferences through cascading sets of boxes with double-headed arrows:
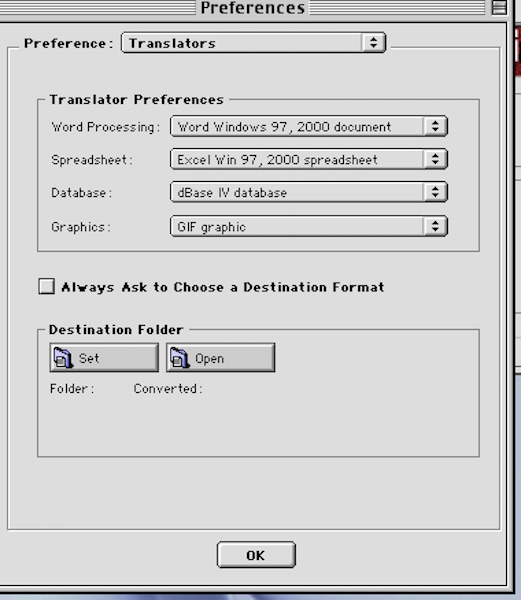
Jon has the preferences set to what should work for most users.
You translate word-processing documents into Word 97-2000 .doc format.
You translate spreadsheets into Excel 97-2000 .xls format.
You translate databases into Dbase IV format. It was the industry leading microcomputer database back in the day.
You translate graphics into GIF format.
Now if you click on the double-headed arrows at the right of the translator preferences for each type of document, you get a range of choices. Some will be archaic (WordStar?) and some will be useful such as Rich Text Format. although you have a choice between RTF for Mac and RTF for Windows.
In all honesty, stick with these defaults for word-processing and spreadsheets. Your current office programs can read those formats.
As I mentioned in the previous article, the MacLink Plus 11 manual comes in PDF format in the MacLink Plus Tech Support folder within the main MacLInk Plus folder in Applications. Refer to it.
Tom Briant
Editor, MacValley Blog
Opening Old Word Processing Formats such as Word 5.1 using LibreOffice or Chubby Bunny to convert them to a modern format
I would like to thank Eric Hsu for defining the problem and giving some answers here.
I recently received an inquiry about translating old Word 5.1 files into a format a modern word processor could read. I gave my correspondent two answers and now I will share them with you.
First, download LibreOffice here LibreOffice 5.x has versions for OS X, Windows, and Linux. I have used it under OS X 10.11.4, Windows 10, and Ubuntu 15.10
LibreOffice will read Word 5.1 documents. You can save them in a variety of formats such as Word 97-2004 with the .doc extension, Word 2007 through 2016 with the .docx extension, and Rich Text Format with the .rtf extension. Of course, you can also use LibreOffice’s default format of .odt, too
LIbreOffice has been referred to as the Swiss Army Knife of office suites as it opens so many formats that otherwise you can’t open in the current version of MS Office.
But what if you have a lot of files? You’ll want to batch convert those files automatically and not spend time opening and saving each file.
Now Eric suggested Edward Mendelson’s WPMac68KApp, but mentioned it has problems preventing it from running it initially. I ran into those problems. I don’t have a fix for those problems. But I DO have an alternative Classic OS emulator that works perfectly under 10.6.8 through 10.11.4, the latest version of OS X.
That emulator is Classic-On-Intel 4.01 (aka Chubby Bunny), which I first mentioned here. It is a self-contained OS 9.04 appliance, which recreates a PPC Mac running OS 9.04 on your desktop. Jon Gardner, the creator of this package, wrote clear & specific instructions both as a PDF to read in OS X and as a SimpleText document to read while you run Classic-On-Intel. You can download it from Jon’s site at home in Texas here.
Go here for my original article
Now the heart of Eric Hsu’s post is that WPMac68KAPP has a copy of MacLinkPlus 11. Well, so does Classic-On-Intel 4.01!
You will find MacLink Plus 11 here on the Classic HD virtual hard drive:

Within the MacLink Plus 11 folder, you will find a sub-folder called “MacLinkPlus Tech Support” Within that you will find the app’s manual in PDF format.
Full Instructions for those who have never used a Classic Mac OS app before!
Now I’m going to assume that a lot of you started with OS X recently. You never used Classic Mac OS and may find it confusing. So I will give you step-by-step instructions.
1. Download COI 4.01+.zip to your Downloads folder. The link to Jon’s site is reliable and you should download it quickly.
2. Click on the icon for COI V4.01+.zip.
![]()
It will automatically expand into a folder with the components inside.
![]()
3. Now double-click on the folder to open it.
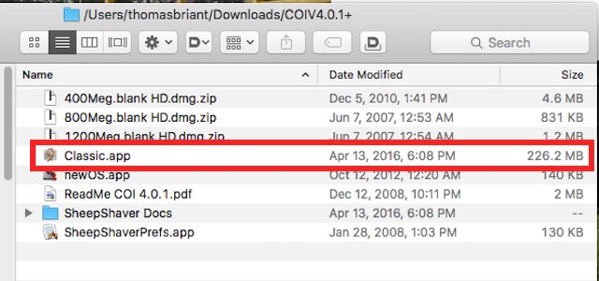
4. Now, what’s in the folder and what could cause you problems?
Right Now, I Want You to Read the ReadMe COI 4.01 PDF. That will tell you information you need to know. Among the items of information is where you can place files on your physical Mac so that you can access them from your virtual Classic Mac and vice-versa.
If you need more disk space for additional programs, the PDF will tell you about the 400 Meg, 800 Meg, and 1200 Meg .dmg files. These serve as additional hard drives for COI.
After you’ve glanced over the ReadMe PDF, now you want to drag and drop the Classic.app into your Applications folder. That’s it for now. No Terminal work or editing of files is involved.
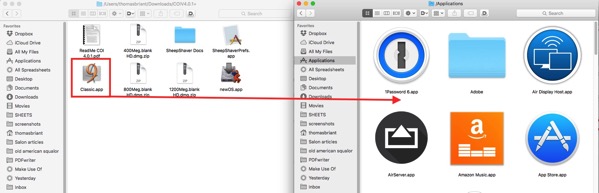

When you double click on the Classic app, you will see this screen initially:

When COI finishes booting up, you will see this screen:

You will see MacLinkPlus on the OS 9 Launcher, ready for you to use.
Double-click on it to launch it
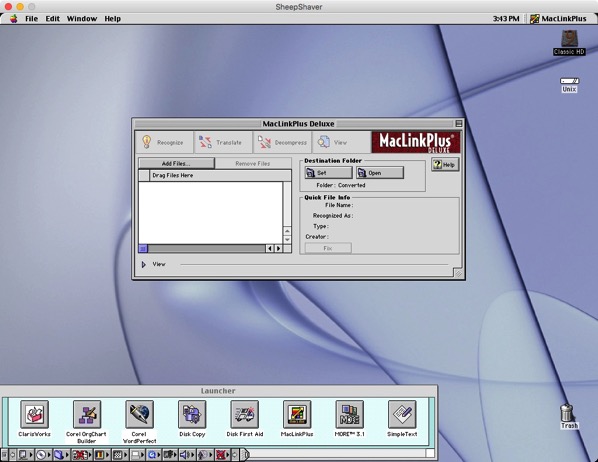
Now to set up a conversion session:
Now, where can you put your Microsoft Word 5.1 files so that MacLink Plus 11 can convert them?
You cannot just put them into your /Users/<myusername>/Documents folder. That will not work.
Instead, and this is in the ReadMe PDF file, you need to put the folder of old files into your /Users/Shared/ folder.

This is not a hidden folder, this is an area that OS X sets for shared data between users. Think of it as the pool area at your apartment or condo complex.
Now how do you reach it? Two ways:
1. You can start by clicking on your desktop hard drive icon:
![]()
2: You can click on Users

3. And within the Users folder, the Shared folder:

Or the quick way via the Finder:
1. Here you see the /Users/Thomas Briant folder, which is usually how I see my Mac’s file system.

2. To switch to the /Users/Shared/ folder in a hurry:
Hold down the Shift key and the Command key together. Hold them down with your left hand. Now press the letter G with your right hand
You will see this window pop up:
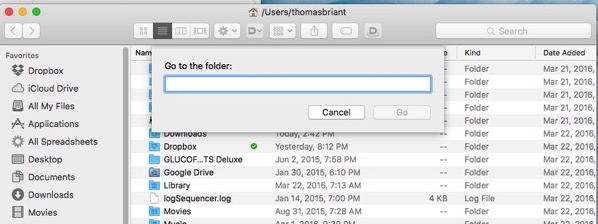
Now for the secret sauce. Type in Users/Shared

Now hit the ENTER key:
And you are in the /Users/Shared folder. Simple, wasn’t it? You’ve just done your first bit of command-line kung fu.

Okay, what’s the big deal about the /Users/Shared folder and COI? How do you get to it from within COI?
You get to the /Users/Shared folder through the Unix icon on your virtual Classic Mac OS desktop:
![]()
Double-click on that Unix icon and it opens a window with the /Users/Shared folder’s contents:

See? They’re the same
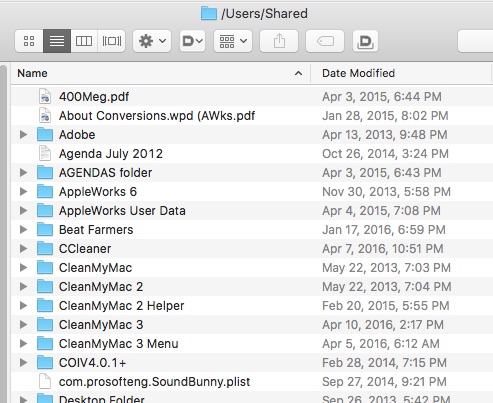
So it comes down to that through the Unix icon & folder, you can drag files into and out of COI. You can also access files in the /Users/Shared folder from COI.
Getting back to MacLink Plus 11
I will go through a test case of translating 20 Microsoft Word 5.1 files into the equivalent Microsoft Word 97-2004 .doc format
Now I have downloaded a ZIP file with 20 Word 5.1 files that I found on line using Google. I have moved them from my Downloads folders to my /Users/Shared folder.
Now you want to add this folder to MacLlinkPlus 11. Three ways to do this:
1. Click on the Add Files button:

2. Go to the File Menu and Click on Add Files. The keyboard shortcut is Command + O.

3. Or just drag and drop the files into the white area below the Add Files button:

Okay, so far so good. You’ve added a list of files you want to convert to MacLinkPlus 11. Now where do you want to put the converted files?
Simple. You click on the Set button that I’ve highlighted in red in the top part of the screenshot. That opens a file dialog box showing the Unix folder

You’ll want a new folder, so click on the New button that I’ve highlighted in red at the bottom of the screenshot.

You type in a name and press Create. Voila! Your new folder inside the Unix folder is done.

Final step before Conversion is to click on the Choose button, which makes the final selection of the folder to send the converted files to. MacLink Plus assumes that you’re going to use the folder you just created, it’s already highlighted. Just press Choose.

Final check. You’ve selected the files in the appropriate folder, set up a destination folder.
Hit the Translate Button!
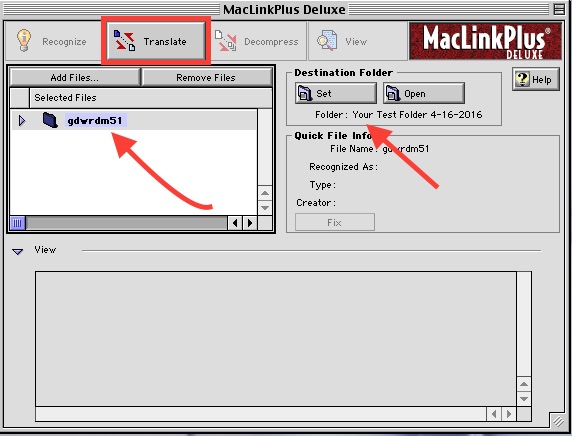
Translation looking good so far.
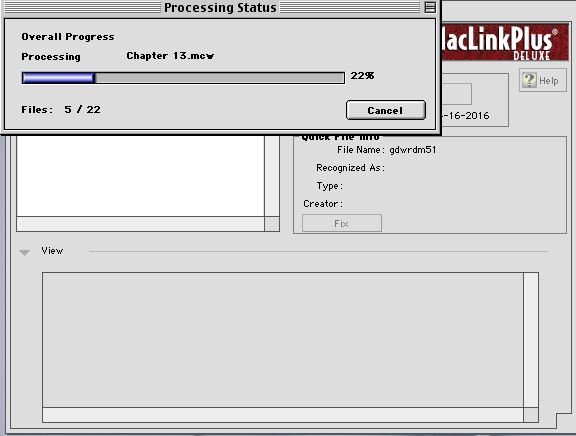
The files look good so far, but we have to test them:

All right! Successful conversion! Word 2016 for Mac reads it with no trouble!

Now that’s all for this article. The next article will cover how to change the settings in COI for the folder that Unix accesses and the file format MacLink Plus translates to.
Tom Briant
Editor, MacValley Blog
Senior Correspondent Arnold Woodworth's Weekly Web Wrap-up for Saturday, April 16, 2016
"Years of use, which are based on first owners, are assumed to be four years for MacOS and tvOS devices and three years for iOS and watchOS devices."
AW comment – oversimplified headline: Your Apple Watch has a Life Span: Three Years
Two slide shows on one web page:
1) A slide show for new iOS (iPhone) apps.
2) A slide show for new Android apps.
This web site has a list (well, actually two lists) of new apps every week.
http://www.phonearena.com/news/Best-new-Android-and-iPhone-apps-April-5th---April-11th_id80111
iPhone 7 concept video is jaw-dropping
I've seen my fair share of iPhone concept videos, but this one strikes the right and rare balance of aspiration and realism.
http://www.networkworld.com/article/3055437/smartphones/iphone-7-concept-video-is-jaw-dropping.html
http://www.androidguys.com/2016/04/11/3-ways-ios-is-beating-android-and-what-google-can-do-to-change-it/
I bought an Apple keyboard from 1990 just for my iPad Pro
Apple found $40 million in gold in used phones and computers last year
As part of that, Apple recovered 2,204 pounds of gold — well over a ton.
The first thing I noticed that phoneless week was just how many people stare at their phones all day. I never noticed that before because I was looking at my phone, too.
most startling was the realization that so many people look at their phones while they are walking. The weekday New York sidewalks are almost like that scene from "Wall-E," an animated science fiction movie.
http://www.businessinsider.com/i-went-without-my-smartphone-for-7-days-2016-4
http://www.businessinsider.com/7-day-digital-detox-2016-3
In Malaysia, the longest python ever discovered, died after lots of pictures of people holding it for pictures.
Find a washed-up dolphin? Great! Now damn well pick that dolphin up and walk around with it over your head so that everyone can get that really good snap for Facebook! (Oh, it died).
If it wasn’t so sad it might be laughable: a love of animals, undermined by thoughtlessness.
http://www.theguardian.com/commentisfree/2016/apr/13/animal-cruelty-death-camera-phone-selfie-giant-python
Make LinkedIn Work for You
http://www.marketwatch.com/video/make-linkedin-work-for-you/4C6010CB-D17D-4405-BC2C-E21A2801F306.html
Why Do Older People Love Facebook? Let’s Ask My Dad
seeing photos and video of grandchildren were a powerful lure.
keeping in touch with family and with the friends.
the online lives of older adults, who are a part of the fastest-growing demographic on social media, are much more mysterious than the much-scrutinized behaviors of younger generations.
http://www.nytimes.com/2016/04/15/technology/why-do-older-people-love-facebook-lets-ask-my-dad.html?emc=edit_ct_20160414&nl=personaltech&nlid=11893479&_r=0
Facebook's chatbots pave way for centralized mobile platform
"No one wants to have to install a new app for every business or service they want to interact with," CEO Mark Zuckerberg said at the company's annual F8 conference in San Francisco. "We think you should be able to just message a business in the same way you message a friend.”
If Facebook can persuade its huge user population to use its platform not only for all manner of social interactions but also for business interactions, it will become a very different company.
http://searchcio.techtarget.com/news/450281451/Facebooks-chatbots-pave-way-for-centralized-mobile-platform
until now most technology has only been able to replace narrow slices of human capability, like physical strength or mathematical calculations.
But things are changing. A recent analysis by McKinsey showed that up to 45% of all current job tasks could be automated with existing technology.
We have of course had disruptive technologies in the past, and significant migration in the workforce from farm to factory to services.
In each transition, we increased education levels and moved human labor into tasks that machines could not yet perform. But the difficulty is that the set of available tasks only humans can do will get narrower and narrower over time.
We need to begin preparing for this inevitability and reimagine a society where most people cannot 'work for a living,” but instead can be liberated to pursue their own vision of a meaningful life.
There is a growing global movement to explore basic income, which can provide economic security to people as we shift into a world where machines do most of the work. This can and should be a very positive development for humanity — we just need to prepare for a potentially difficult transition, as human labor becomes less and less necessary.
http://www.businessinsider.com/basic-income-is-the-best-way-to-survive-the-robot-takeover-2016-4
Why Artificial Intelligence (AI) still needs us: To build quantum computers
We're doing a lot better than machines are at solving some of the key problems of quantum computing.
Researchers at Danish Aarhus University have created a bunch of online games to turn key quantum problems into fun challenges, and, to put it bluntly, they're finding that humans are whipping AI's pants.
The researchers' games are available online for anyone to download or play.
http://www.pcworld.com/article/3056778/analytics/why-ai-still-needs-us-to-build-quantum-computers.html
How Early Computer Games Influenced Internet Culture
“I strongly believe that games have been largely underrated in the spread of what we might think of as our ‘orientation’ toward computing,” said Laine Nooney, a cultural historian of video games and computing. “In the span of less that 20 years, many Americans went from having never seen a computer to interacting with these machines in many facets of their daily lives. Gaming is the first form of computational technology most of us ever handled … Games taught us principles of interaction and screen responsiveness, about coordination between hand and eye, how to type, how to sit, how to look at a screen.”
http://www.theatlantic.com/technology/archive/2016/04/how-early-computer-games-influenced-internet-culture/478167/
August 6 – Los Angeles, CA / The Theatre at the Ace Hotel
http://www.businessinsider.com/star-wars-coming-back-to-theaters-2016-4
Six tech revolutions you better be ready for
Because you can invest in them. They are:
Artificial Intelligence
Chatbots
Virtual Reality
Drones
Robotics
there have never been so many tech revolutions setting up to boom over a five- to 10-year period as there are right now.
http://www.marketwatch.com/story/six-tech-revolutions-you-better-be-ready-for-2016-04-15
This warning arrived too late – unless you filed for an extension on your taxes.
But it’s probably a good idea for next year too.
The Internal Revenue Service on Friday warned tax preparers of a new scam in which cyberthieves hijack a preparer's computer system, file client tax returns, and redirect refunds to thieves' accounts.
http://www.marketwatch.com/story/hackers-seek-to-hijack-tax-preparers-computers-2016-04-15
8 cybersecurity technologies the Department of Homeland Security (DHS) is trying to commercialize
The Department of Homeland Security is publicizing eight new cybersecurity technologies developed under federal grants that are looking for private businesses to turn them into commercial products.
http://www.cio.com/article/3056899/security/8-cyber-security-technologies-dhs-is-trying-to-commercialize.html
“I saw something in the news, so I copied it, I put a piece of tape over the camera,” Comey explained, “because I saw somebody smarter than I am had a piece of tape over their camera.”
https://www.entrepreneur.com/article/273950
Surveillance and public-benefits programs gather large amounts of information on low-income people, feeding opaque algorithms that can trap them in poverty.
Once an arrest crops up on a person’s record, for example, it becomes much more difficult for that person to find a job, secure a loan, or rent a home. And that’s not necessarily because loan officers or hiring managers pass over applicants with arrest records—computer systems that whittle down tall stacks of resumes or loan applications will often weed some out based on run-ins with the police.
When big-data systems make predictions that cut people off from meaningful opportunities like these, they can violate the legal principle of presumed innocence, according to Ian Kerr, a professor and researcher of ethics, law, and technology at the University of Ottawa.
http://www.theatlantic.com/technology/archive/2016/04/how-big-data-harms-poor-communities/477423/
Microsoft sues U.S. government over secret customer data searches
The suit, filed in the federal court here, raises a fundamental question about the cloud computing era: Can the government force technology companies to remain silent about when and how federal agents search their customers’ data?
Microsoft says in its suit that it received 5,624 federal demands for customer information in the past 18 months, and nearly half—2,576—came with gag orders preventing the company from telling customers the government was looking at their data.
http://www.marketwatch.com/story/microsoft-sues-us-government-over-secret-customer-data-searches-2016-04-14
How a Cashless Society Could Embolden Big Brother
When money becomes information, it can inform on you.
In a cashless society, the cash has been converted into numbers, into signals, into electronic currents. In short: Information replaces cash.
But wherever information gathers and flows, two predators follow closely behind it: censorship and surveillance. The case of digital money is no exception. Where money becomes a series of signals, it can be censored; where money becomes information, it will inform on you.
The choke points are private corporations that are not only subject to government regulation on the books, but have shown a disturbing willingness to bend to extralegal requests—whether it is enforcing financial blockades against the controversial whistleblowing organization WikiLeaks or the website Backpage, which hosts classified ads by sex workers, and allegedly ads from sex traffickers as well. A little bit of pressure, and the whole financial system closes off to the government’s latest pariah. Operation Choke Point exploited this tendency on a wide scale.
it is part of a larger trend, pushing us closer to a world where the cashless society offers the government entirely new forms of coercion, surveillance, and censorship.
A cashless society promises a world of limitation, control, and surveillance—all of which the poorest Americans already have in abundance, of course. For the most vulnerable, the cashless society offers nothing substantively new, it only extends the reach of the existing paternal bureaucratic state.
As paper money evaporates from our pockets and the whole country—even world—becomes enveloped by the cashless society, financial censorship could become pervasive, unbarred by any meaningful legal rights or guarantees.
http://www.theatlantic.com/technology/archive/2016/04/cashless-society/477411/
From software that records your every keystroke, to GPS tracking, to ignition kill switches—lenders have more power over their customers than ever.
In 2012, the Federal Trade Commission settled with seven companies over their undisclosed use of the Detective Mode software. Detective Mode webcam activations have taken pictures of children, individuals not fully clothed, and couples engaged in sexual activities.
While few lenders will go as far as to take naked pictures of their debtors, wherever there is an expensive device that can be easily absconded with, it makes sense for lenders to add both a kill switch and GPS.
the history of digital rights management (DRM) has always had a dark side.
wherever DRM went, privacy invasion followed.
http://www.theatlantic.com/technology/archive/2016/04/rental-company-control/478365/
the Royal Canadian Mounted Police (RCMP), Canada’s federal police force, intercepted and decrypted “over one million” BlackBerry messages during an investigation into a mafia slaying, called “Project Clemenza," that ran between 2010 and 2012.
According to privacy expert Christopher Parsons from Canadian security research hub Citizen Lab, the RCMP may still have the ability to read anybody’s encrypted BlackBerry messages, as long as the phone isn’t linked to a corporate account.
The defence initially argued that the RCMP should disclose the global encryption key in court, but it was ultimately considered privileged and withheld. If the key used in Project Clemenza was revealed in open court, Boismenu said, then it would “essentially mean to disclose a key that would unlock the doors of all the houses of the people who use the provider’s services, and that, without their knowledge.”
The key, according to Boismenu, is so powerful that it could be used to “illegitimately” decipher any “prerecorded communications encrypted with that key”—so it’s striking that the RCMP had access to it.
Indeed, Crown attorney Robert Rouleau stated in an ex parte hearing: “So right now, with my device, if I’m not on the [Business Enterprise Server], I’m a dead chicken. That’s the reality of it, that’s what we don’t want the general public to know.”
Disclosing such a key would be disastrous for BlackBerry, the court heard.
The RCMP also used a spy tool popular with US police known as an IMSI catcher, or “StingRay,” which collects phone numbers and other identifying information from devices within a one kilometre radius, according to court documents.
http://motherboard.vice.com/read/rcmp-blackberry-project-clemenza-global-encryption-key-canada
An App That Tracks the Police to Keep Them in Check
data-gathering isn’t just the government’s game. Since recording technology became portable and cheap, citizens have been keeping tabs on their governments, too.
Brandon Anderson wants to systematize sousveillance, by creating a platform for organizing citizen-supplied information about police.
Right now, it can be hard to know what to do with an incriminating photo or a story about a negative interaction with law enforcement. People with a strong following on Twitter or Facebook might be able to broadcast their news widely, but the never-ending sea of social content can swallow others’ stories. If there’s a central destination for depositing data about police, it can become a valuable vehicle for keeping government accountable.
http://www.theatlantic.com/technology/archive/2016/04/mapping-encounters-with-the-police-to-keep-them-in-check/478284/
Senators Richard Burr (R-N.C.) and Dianne Feinstein (D-Calif.) introduced a bill on Wednesday that aims to weaken encryption, thus making it easier for outsiders to see your messages and personal data.
The “Compliance with Court Orders Act of 2016” — which was leaked late last week, but officially released Wednesday — requires tech companies, or really any company or person involved in processing or storing data, to provide a way to access that data if the government asks for it via court order.
http://www.businessinsider.com/lawmakers-just-took-a-big-step-to-kill-encryption-on-your-phone-2016-4
The encryption security debate that is the fallout from the FBI-Apple debacle has taken a dangerous — and utterly predictable — turn. Congress has gotten involved, in a most unhelpful way.
A preliminary version of an encryption bill from Senate Intelligence Committee Chairman Richard Burr (R-N.C.) and ranking member Dianne Feinstein (D-Calif.) ... truly secure encryption would be illegal.
http://www.computerworld.com/article/3056690/encryption/let-s-not-make-secure-encryption-illegal.html
Saturday, April 9, 2016
Senior Correspondent Arnold Woodworth's Weekly Web Wrap-up for Saturday, April 9, 2016
What the Apple Watch Does, One Year Later
http://www.nytimes.com/2016/04/07/technology/personaltech/what-the-apple-watch-does-one-year-later.html?emc=edit_ct_20160407&nl=personaltech&nlid=11893479&_r=0
What the iPhone has done to cameras is completely insane
When was the last time you used an MP3 player or held a calculator? What about a physical map? Or a BlackBerry? Do BlackBerrys even exist anymore?
There might, however, be no better example than the camera, which has suffered mightily since the iPhone was introduced almost 10 years ago.
The biggest hit has been to [lower priced] point-and-shoot cameras. Sales of the lower-quality, fixed-lens, hand-held devices way too many people used to tie to their wrists have fallen off a cliff since the iPhone's introduction. And few no one expects them to climb back up.
https://www.washingtonpost.com/news/wonk/wp/2016/04/07/what-the-iphone-has-done-to-cameras-is-completely-insane/
How to create slo-mo videos for Instagram on your iPhone
http://www.cnet.com/how-to/how-to-create-slo-mo-videos-for-instagram-on-your-iphone/
How to Switch to iPhone from Android: Patience and Persistence
Long ago, I wrote a blog post with the headline: “Why my phone won’t be an iPhone.”
But now I have finally caved in: My phone is now an iPhone.
Switching phone operating systems should in theory be simple. First you transfer your data from the old phone to the new one. Then you reinstall your favorite apps. Finally you customize the settings for features like ring tones and notifications and learn the quirks of your new device.
But as I learned, many things can go wrong, and my experience is not unusual.
Given the headaches of switching, most people avoid it.
Over all, I am getting more comfortable with my iPhone. I like Apple’s fingerprint reader and have finally figured out how to align my fingertips precisely enough to unlock the phone (at least most of the time).
Will the iPhone ever feel like home? Check back in two years, when I am due for my next upgrade
http://www.nytimes.com/2016/04/07/technology/personaltech/how-to-switch-to-iphone-from-android-patience-and-persistence.html?_r=0
Cookie Monster's Apple ad 'outtakes' are pure joy
Treat yourself to this video. Then treat yourself to a cookie.
http://www.theverge.com/2016/4/7/11388556/cookie-monster-apple-siri-commercial-so-cute
A really bizarre way to test an iPhone
http://motherboard.vice.com/blog/guy-tries-and-fails-to-kill-an-iphone-se-by-freezing-and-dropping-it
iPhone SE Sold Out, Reddit's Controversial App, iPhone 5S Is Not Dead
This article also describes a newly discovered security bug in iOS. However, Apple was able to address through its own servers, so you don’t need to update your iPhone to fix it.
FBI’s New Hacking Tool Is Limited
As part of Autism Acceptance Month, Apple released a video about Dillan, a teenager who uses his iPad and a number of augmented and alternative communication apps to allow him to communicate with the world even though he is non-verbal.
http://www.forbes.com/sites/ewanspence/2016/04/08/apple-news-digest-iphone-se-sales-ios031-reddit-app/
My life as an Apple guy
A very interesting view of Apple and Mac history.
http://www.macworld.com/article/3050937/macs/my-life-as-an-apple-guy.html
51 Facts About Apple’s Future Headquarters
And several videos too that show progress at different times over the past year.
http://www.macworld.co.uk/feature/apple/apple-spaceship-campus-facts-pictures-video-info-video-3489704/
How Apple is grooming the iPad to take over the Mac
Where the original iPad was criticized for being a giant iPhone, the Pro is much more than a refresh of the classic tablet; it’s Apple’s first touchscreen device truly imagined for professionals.
http://www.macworld.com/article/3053477/ipad/how-apple-is-grooming-the-ipad-to-take-over-the-mac.html
Apple's aging Mac Pro is falling far behind Windows rivals
the Mac Pro is again falling behind the competition, with powerful new workstations from Lenovo, Dell and HP carrying superior technology. The PC companies are waging an active campaign to tempt Mac Pro users, many of them creative professionals, to move over to Windows PCs with better CPUs, GPUs, and memory.
http://www.computerworld.com/article/3052871/computer-hardware/apples-aging-mac-pro-is-falling-far-behind-windows-rivals.html
As wearable devices in workplace spread, so do legal concerns
Devices can monitor employees’ health, track their locations. How are companies allowed to use that data?
http://www.marketwatch.com/story/as-wearables-in-workplace-spread-so-do-legal-concerns-2016-04-04
Facebook is hiding messages from you in a secret inbox — here's how to find it
http://www.businessinsider.com/how-to-find-hidden-message-requests-on-facebook-messenger-2016-4
5 insider tips for getting noticed on LinkedIn
Keywords
Benefit statement
Actively post content (or curate content)
View other people’s profiles
Give recommendations (don’t ask for them)
http://www.businessinsider.com/how-to-get-noticed-on-linkedin-2016-4
Open Source Replacements for Expensive Applications
52. Dia:Replaces Visio Professional ($589.99)
53. Gimp:Replaces Photoshop ($239.88 per user per year)
61. Libre Office:Replaces Microsoft Office ($99 per user per year and up)
63. Neo Office:Replaces Microsoft Office ($99 per user per year and up)
97. Bluefish:Replaces Adobe Dreamweaver ($239.88 per user per year)
http://www.datamation.com/open-source/open-source-replacements-for-expensive-applications-1.html
This person figured out the Windows 10 upgrade from a photograph.
Another replied:
Best of all, Windows is associated here with "ow my balls."
http://www.computerconsultantsforum.com/forum/politics/finally-figured-out-windows-10-upgrade/
Neil deGrasse Tyson explains the meaning of life
He says “The meaning of life is what you create” and “ways you can enrich the meaning for others”.
http://www.techinsider.io/neil-degrasse-tyson-meaning-life-2016-4
The police could be controlling your self-driving car
There have to be authentication standards and encryption standards to limit commands to those who are authorized to use them. There should be techniques that direct commands to one autonomous vehicle (AV) rather than all in the neighborhood.
Last, but by no means least, is whether such override systems could possibly be made hack-proof. A system to allow authorized people to control someone else’s car is also a system with a built-in mechanism by which unauthorized people — aka hackers — can do the same.
http://www.marketwatch.com/story/the-police-could-be-controlling-your-self-driving-car-2016-04-02
Video:
Hackers-for-Hire Business Is Booming
http://www.marketwatch.com/video/hackers-for-hire-business-is-booming/3A23E0CA-9EFF-4AF7-8428-EB8F93C79A41.html
It's surprisingly easy for hackers to get your health insurance information in these 3 states
California
Kentucky
Vermont
http://www.businessinsider.com/ap-security-flaws-found-in-3-state-health-insurance-websites-2016-4
Victims paid more than $24 million to ransomware criminals in 2015 — and that's just the beginning
Ransomware is a type of computer virus that scrambles its victim's files and demands a ransom in exchange for the code to restore them.
Perhaps most disturbing is how often infected organizations end up paying ransoms to regain access to their computer systems.
Police departments (PDs) are particularly vulnerable to ransomware. Police departments have been forced to hand over taxpayer dollars to criminals in Tennessee, Illinois, and three times in Massachusetts.
http://www.businessinsider.com/doj-and-dhs-ransomware-attacks-government-2016-4
The next Cold War has already begun — in cyberspace
When we think of cyber attacks, we often think of terrorists or criminals hacking their way into our bank accounts or damaging government websites. But they have now been joined by agents of different governments that are launching cyber attacks against one another.
They aren’t officially at war, but the tension between the US and Russia – and to a lesser degree China – remains high over a number of disputed decisions.
Advanced encryption technologies make it almost impossible to prove exactly who is responsible for a specific cyber attack. As a result, states can now act unilaterally with little fear of open retaliation.
http://www.businessinsider.com/the-next-cold-war-has-already-begun-in-cyberspace-2016-4
WhatsApp Introduces End-to-End Encryption
WhatsApp, the messaging app owned by Facebook and used by more than one billion people, on Tuesday introduced full encryption for its service, a way to ensure that only the sender and recipient can read messages sent using the app.
Known as “end-to-end encryption,” it will be applied to photos, videos and group text messages.
The government has faced similar issues with companies like Telegram, Signal and Wickr Me, messaging services that also offer encrypted communications.
http://www.nytimes.com/2016/04/06/technology/whatsapp-messaging-service-introduces-full-encryption.html?emc=edit_ct_20160407&nl=personaltech&nlid=11893479
And at a time when the FBI and other governments are seeking to install backdoors in major products, most notably Apple’s iPhone, the Panama Papers show just how vital encryption is to revealing stories of corruption that are undoubtedly in the public interest.
http://www.forbes.com/sites/thomasbrewster/2016/04/05/panama-papers-amazon-encryption-epic-leak/#5844f1f31df5
JOHN McAFEE: A time bomb is hidden beneath the Panama Papers
I am just one of more than 200,000 people to have downloaded the Panama Papers, a record for hacked documents. It was a gold mine.
In September I keynoted the Lawtech conference in Australia's Gold Coast and gave a live demonstration of how easy hacking can be. The room, packed to the brim with lawyers, was stunned into silence. After the demonstration and talk I was mobbed by frightened lawyers. The common comment was, "I had no idea."
http://www.businessinsider.com/john-mcafee-panama-papers-evidence-we-need-better-cybersecurity-2016-4
FBI says method used to unlock iPhone doesn’t work with iPhone 5s or newer
http://techcrunch.com/2016/04/07/fbi-says-method-used-to-unlock-iphone-doesnt-work-with-iphone-5s-or-newer/
Video:
Why the FBI-Apple Battle Over the iPhone Is a Win for Users
http://www.wsj.com/video/why-the-fbi-apple-battle-over-the-iphone-is-a-win-for-users/783A005B-9FFA-443C-B6CD-3345DC67F734.html
Apple-Justice Department Standoff Over iPhone Access Goes On, In New York
The Justice Department told a judge that Apple's help is still needed to unlock an iPhone seized from a methamphetamine dealer. The DOJ is appealing a ruling from a magistrate judge, who sided with Apple in February.
http://www.npr.org/sections/thetwo-way/2016/04/08/473423254/apple-justice-department-standoff-over-iphone-access-goes-on-in-new-york
The FBI still wants to get into your iPhone
http://www.marketwatch.com/story/the-fbi-still-wants-to-get-into-your-iphone-2016-04-08
take a look at the draft text of a bill to be introduced in the Senate that would require tech companies to provide either the data itself or technical assistance needed to access data when presented with a valid court order:
https://www.lawfareblog.com/draft-feinstein-burr-encryption-bill-here
And at a time when the FBI and other governments are seeking to install backdoors in major products, most notably Apple’s iPhone, the Panama Papers show just how vital encryption is to revealing stories of corruption that are undoubtedly in the public interest.
http://www.forbes.com/sites/thomasbrewster/2016/04/05/panama-papers-amazon-encryption-epic-leak/#5844f1f31df5
Blog Archive
-
▼
2016
(123)
-
▼
April
(12)
- Senior Correspondent Arnold Woodworth's Weekly Web...
- Boaty McBoatface Name 'Not Suitable', Science Mini...
- Changing Settings in MacLinkPlus and Classic-On-Intel
- Opening Old Word Processing Formats such as Word 5...
- Senior Correspondent Arnold Woodworth's Weekly Web...
- Senior Correspondent Arnold Woodworth's Weekly Web...
- Spring Cleaning Your Mac-Article 4-You're a Space ...
- Spring Cleaning Your Mac-Article 3-Moving It off t...
- Spring Cleaning Your Mac-Article 2-What's on My Ha...
- Spring Cleaning Your Mac-Article 1-What Happened t...
- The Best Tips From Professional Organizers – Life ...
- Senior Correspondent Arnold Woodworth's Weekly Web...
-
▼
April
(12)


